What is a botnet, who does it use to attack, and how can you prevent botnet?
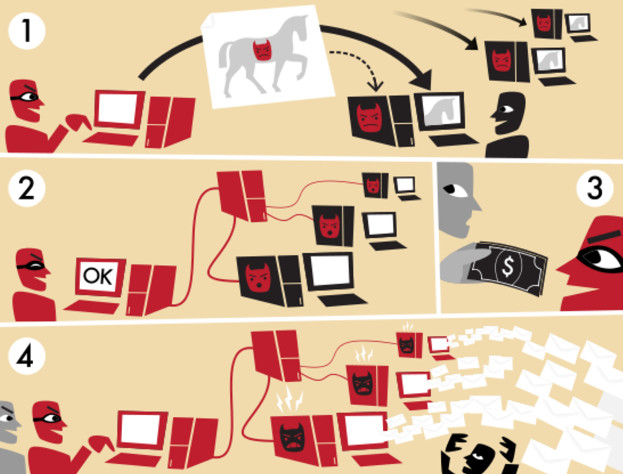
A botnet is a network of computers that have software installed to do a certain job. People often talk about botnets with a worse meaning than good because the botnet is used by a black hacker to attack a website or an online service. Botnet is not only used to harm others, but also to the infected computer / phone itself because it can carry other malicious software, such as a ransomeware that encrypts your data and demands ransom to unlock for example.
What is a botnet?
The history of botnets started like this: In 2000, Professor Vijay Pande, a researcher at Stanford University, released a software when downloaded by the user, which would simulate the kinking process of protein. This is a necessary step to study medicine, however, because the folding is very complicated, it takes a lot of computer power to simulate the most basic stages. Instead of using a powerful computer to run simulations, Pande spreads this "burden" to many personal computers to save costs while still gaining the power needed to run calculations.
Basically, Pande created a botnet.
According to McAfee, botnets are a network of personal computers that work together to accomplish a task. The word botnet is used because most of them are automation programs spread out in the network. Often these computers will be controlled by a server, and in the case of a botnet this server is called by the command name or server control. Later, there was another peer-to-peer (P2P) botnet, at that time there was no need for a central server.
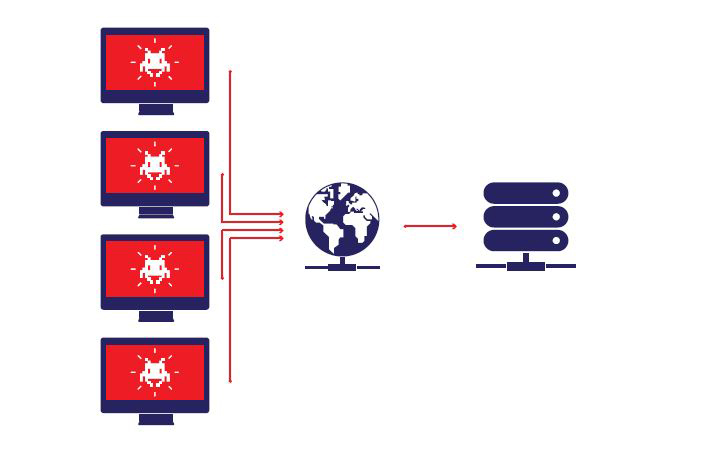
If only individual software (bots) are considered, they are only relatively weak programs. But if thousands or hundreds of thousands of bots work together, they become extremely powerful and can cause great damage.
It should be noted that there are two types of botnets: one is legal, often used for scientific research like the case of Dr. Pande. It helps scientists save costs and increase processing performance for their research, of course users will know well that their machine is running the bot written by the researcher. The second type is illegal, often used by bad guys to do bad things and users do not know they have been installed bot on the computer. In this article we mainly talk about illegal types.
What is the botnet used for?
One of the most popular ways to use botnet is to create denial of service (DDoS) attacks. Computers that are infected with botnets will constantly ask for access to a website, which will cause the server of the website to be overloaded and unable to meet the access of the users who are actually on the site. DDoS attacks can cost businesses from a few hundred to a million dollars depending on the size of the attack and what kind of website is attacked.
The image of a DDoS attack on a website with lots of requests sent over extremely short periods of time can overwhelm the server.
For example, a bank's online trading site was attacked in an hour. In that hour, the bank's real customers could not trade, causing them to switch to the website of an intermediary or another bank, so the attacked bank lost revenue. Or as delicate as that, if you are attacked, you cannot go to read the article, too many times, you will be bored and not play anymore.
Botnets can also be used to distribute viruses, steal passwords or to distribute spam. Generally, botnets are extremely cheap and effective ways for cyber criminals to take advantage of the power of many computers to do bad things.
To tell a little story, McAfee once said they collaborated with the US Justice Department to destroy a botnet called Gameover Zeus. This botnet will steal personal information, such as bank account username and password. It is also used to distribute Cryptolocker, a specialized ransomware that encrypts user's files for ransom. You can learn more about ransomeware here. Since its inception, Gameover Zeus and Cryptolocker have caused more than $ 100 million in damage and $ 27 million in order. The creator of this botnet, Evgeniy Mikhailovich Bogachev, is being wanted by the FBI.
Previous botnets only appeared on computers, but now extended to both mobile devices and most recently an Internet-connected surveillance camera in Vietnam was also struck. In fact, these cameras are also a miniature computer. But the danger is that people do not know in this camera installed bot, and it is only used to attack many other websites but also makes the transmission of the user is markedly slow. See more here: Details of many security cameras in Vietnam are being taken advantage of for DDoS attacks.
Most recent botnets have used the P2P peer model completely (so is Gameover Zeus). The command and implementation are completely embedded in the botnet instead of having to use the server, so there is no single weakness. In the traditional way, the hacker server is knocked down, the attack will stop, while in P2P, one PC will be destroyed, the remaining PCs will continue their work.
How to prevent botnet?
Listen, the botnet doesn't seem to be harmful to your computer, because it is used to attack people's websites? But no, botnets can also be integrated with other functions to disrupt files in our PCs, such as the ransomeware above or the credit card stealing virus. Some botnets are capable of downloading other malware themselves, so once the bot has entered, it will open the door to other malicious software. In general, the risk of botnets with us is still very high, not inferior to other types of malicious software.
Anti-botnet is like anti-virus, you can apply the same measures to protect your device.
1. Be careful with USB or strange devices plugged into your computer: there may already be a bot available on the USB device from another computer, when it is attached to your PC, it will infect and sneak in your PC. unaware. The best way is to be careful with USB devices like this and use more anti-virus software to protect against bot attacks.
2. Speaking of antivirus software, you should use Win to choose a solution that is safe for your computer. Currently Windows 10 and the built-in alert mechanisms in Windows are smart enough to prevent many threats but are still only normal, with complex bots or malware, Windows cannot detect. So you might consider using an antivirus software if your environment is often at risk (for example, a copier desktop computer). Currently copyright of antivirus software is also quite cheap, about 150,000 to 200,000 VND a year.
3. Be careful when surfing the web. This is a great way for hackers to use it because he can easily trick you into downloading a certain image file or document file but actually has malware inside. As soon as you click on the file, the bot has started running and is able to infect other PCs on the same network. When you see messages like "Your computer is infected with a virus" or "You are lucky to be chosen to .", don't be fooled by it because you may accidentally download the bot to your computer without knowing it.
4. Talking about mobile devices, you should only install the app that is confirmed to be safe and install only from Play Store or App Store, do not use third-party app stores. Currently there are many malware appearing on both Android and iOS (jailbroken) devices to turn your smartphone into a network bot.
5. Security cameras are a new danger when talking about botnets. Cameras with unclear origins, mostly non-branded Chinese, have the ability to be embedded with botnets without you knowing it. Choose a camera from reputable firms and regularly monitor the line to see if something is wrong.
You should read it
- ★ Microsoft has just taken down a huge botnet network
- ★ Microsoft dismantled the ZLoader botnet, naming key members as a deterrent
- ★ GoldBrute botnet campaign is trying to hack 1.5 million RDP servers worldwide
- ★ The US warned about DealtaCharlie - DDoS botnet malware from Korea
- ★ Botnet Echobot spreads across a wide range, specifically targeting Oracle and VMware applications