Another serious memory leak discovered in Intel chips
Computer scientists at ETH Zurich University (Switzerland) have discovered a serious vulnerability in Intel processors that allows hackers to steal sensitive data by exploiting the chip's speculative execution mechanism. Through a special command sequence, attackers can bypass security barriers and gradually read the entire memory on the shared processor. This vulnerability affects most Intel chips released in the past 6 years, from personal computers to cloud servers.
The ETH Zurich team summarizes the key aspects of the vulnerability as follows:
- Related to speculative execution : Technology that helps chips predict the next step to speed up processing, but also creates loopholes for hackers.
- Blurring security boundaries : Attackers can access private data of other users sharing the same processor.
- Data theft speed up to 5,000 bytes/second : Repeated continuously, hackers can "clean" RAM and cache memory.
- Global impact : Every Intel chip from PCs, laptops to cloud servers could be vulnerable.
Speculative Execution: A Double-Edged Sword
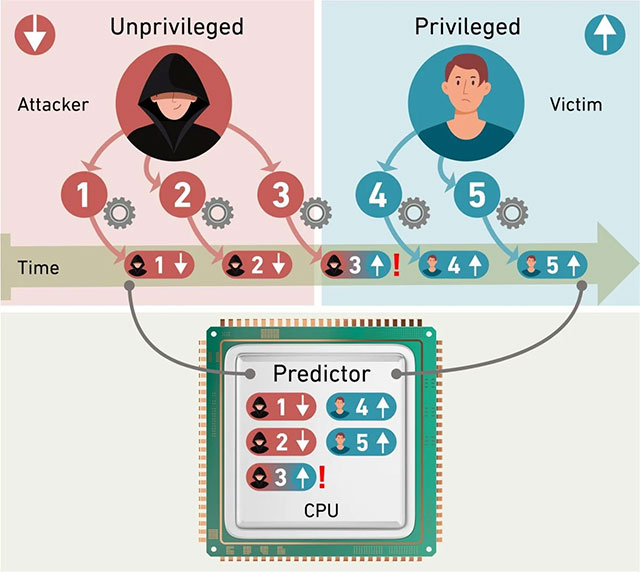
Speculative execution — the technique of 'predicting' instructions to make chips run faster — has now become a fatal weakness. A team of researchers at ETH Zurich demonstrated: With sophisticated instruction sequences, hackers can exploit the prediction mechanism to bypass the decentralization barrier and access other users' data on the same CPU.
"The vulnerability allows reading the entire cache and RAM of other users. This is especially dangerous in cloud computing, where many users share hardware," warned Kaveh Razavi , head of the COMSEC team.
The bug, called BPRC (Branch Predictor Race Conditions), occurs in a matter of nanoseconds when the CPU switches between prediction processes for two users with different permissions. Security engineer Sandro Rüegge (ETH Zurich team member) explains:
- Permission conflicts : When switching users, permissions are not updated simultaneously with calculations, creating a loophole for hackers to "impersonate".
- From 1 byte to entire memory : Each attack only takes 1 byte, but repeated 5,000 times/second, the entire RAM will be "gutted" over time.
This isn't the first time speculative execution has led to data leaks. Spectre and Meltdown made headlines in 2017, followed by Retbleed (2022) — a bug discovered by former ETH Zurich researcher Johannes Wikner.
'When I analyzed Intel's Retbleed patch, I found anomalous signals from the cache — regardless of whether the patch was enabled or not,' Wikner said. Rüegge then dug deeper and found a new attack vector.
Although Intel has patched the bug since September 2024 through a microcode update , the fact that vulnerabilities are continuously discovered shows that the platform architecture is flawed . Intel can only patch each bug, not completely fix it. On the user side, it is necessary to regularly update the BIOS and operating system to receive the latest patches from Intel. In addition, it is also important to monitor warnings from cloud service providers (if using a server).
You should read it
- ★ Microsoft releases tool to help detect memory leaks with Edge
- ★ Samsung's new memory chip incorporates EUFS 3.0 technology, recording speed of 2100MB / s, copying Full HD movies in just 3 seconds
- ★ What does leak mean?
- ★ Intel is about to launch a new Wifi chip that makes web browsing speed unbelievably fast
- ★ Microsoft released an Intel chip patch