China has found that more than 1 million phones in the country have been infected with a virus. The virus constantly sends text messages and damages about $ 300,000 a day for

The security advantage of Linux you probably already know. Not only that, Linux can also be used to rescue a 'paralyzed' Windows computer due to a virus infection.

BitDefender warned of the dangers of a new spy Trojan described by them as 'scary rivals', which can be used as an enterprise scout tool.

This is the most common case of computers after and after being infected with a virus. Even if the virus is completely removed from the system, you still cannot connect to the

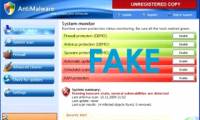
This is one of the most dangerous variants of the WiniSoft series, and is also a copy of the System Veteran malicious application.

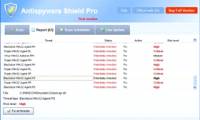
Created for the purpose of targeting the low-cost users, AntiSpyware Shield Pro often comes with other malicious Trojans and malware.

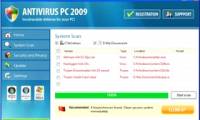
Antivirus PC 2009 is also a fake antispyware security application, capable of spreading and multiplying extremely strongly

In essence, this is a copy of the Total Security rogue program, and it's not too hard to remove

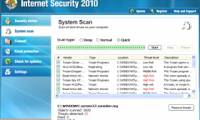
Internet Security 2010 - aka IS2010, is one of the members of the 'family' of Advanced Virus Remover fake security software

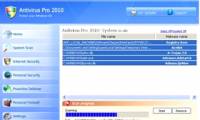
Antivirus Pro 2010 - is currently one of the fake security applications with the fastest transmission rate in the beginning of 2010

According to M86 Security, a new version of trojan Zeus silently stole money from bank accounts around the beginning of last month.

In the following article, TipsMake.com will introduce you to some polymorphic viruses - here is Virus.Win32.Virut and its ce variants

Symptoms of a computer infected with WIN32.Zafi.B is that Windows Firewall will automatically appear accompanied by messages like 'Security Center Alert' ...

Do you suspect that your computer is infected with the virus, but the Anti-virus program on your computer is inefficient or your computer has not had any program to fight the

Classified as extremely toxic Net-Worms, they have strong spread properties through computer networks, their most distinguishing feature is self-replication and spread without the

With the name P2P Worm - they are mainly spread through peer-to-peer sharing models like Kazaa, Grokster, EDonkey, FastTrack, Gnutella ...

The concept of backdoor is used to refer to malware, created to install and distribute malicious code to users' computers ...

Viruses like these often have a mechanism to replicate the resources on the infected computer, unlike worms, unused viruses and exploit network services to replicate and spread

Kaspersky Lab has discovered a worm called IM-Worm.Win32.Zeroll with 4 variants that can spread in all chat programs such as Yahoo Messenger, Skype ...

Classified as Trojan-PSW - for the purpose of stealing personal information, accounts include user login and password access on the infected computer. PSW is an acronym for
 China has found that more than 1 million phones in the country have been infected with a virus. The virus constantly sends text messages and damages about $ 300,000 a day for
China has found that more than 1 million phones in the country have been infected with a virus. The virus constantly sends text messages and damages about $ 300,000 a day for The security advantage of Linux you probably already know. Not only that, Linux can also be used to rescue a 'paralyzed' Windows computer due to a virus infection.
The security advantage of Linux you probably already know. Not only that, Linux can also be used to rescue a 'paralyzed' Windows computer due to a virus infection. BitDefender warned of the dangers of a new spy Trojan described by them as 'scary rivals', which can be used as an enterprise scout tool.
BitDefender warned of the dangers of a new spy Trojan described by them as 'scary rivals', which can be used as an enterprise scout tool. This is the most common case of computers after and after being infected with a virus. Even if the virus is completely removed from the system, you still cannot connect to the
This is the most common case of computers after and after being infected with a virus. Even if the virus is completely removed from the system, you still cannot connect to the This is one of the most dangerous variants of the WiniSoft series, and is also a copy of the System Veteran malicious application.
This is one of the most dangerous variants of the WiniSoft series, and is also a copy of the System Veteran malicious application. Created for the purpose of targeting the low-cost users, AntiSpyware Shield Pro often comes with other malicious Trojans and malware.
Created for the purpose of targeting the low-cost users, AntiSpyware Shield Pro often comes with other malicious Trojans and malware. Antivirus PC 2009 is also a fake antispyware security application, capable of spreading and multiplying extremely strongly
Antivirus PC 2009 is also a fake antispyware security application, capable of spreading and multiplying extremely strongly In essence, this is a copy of the Total Security rogue program, and it's not too hard to remove
In essence, this is a copy of the Total Security rogue program, and it's not too hard to remove Internet Security 2010 - aka IS2010, is one of the members of the 'family' of Advanced Virus Remover fake security software
Internet Security 2010 - aka IS2010, is one of the members of the 'family' of Advanced Virus Remover fake security software Antivirus Pro 2010 - is currently one of the fake security applications with the fastest transmission rate in the beginning of 2010
Antivirus Pro 2010 - is currently one of the fake security applications with the fastest transmission rate in the beginning of 2010 According to M86 Security, a new version of trojan Zeus silently stole money from bank accounts around the beginning of last month.
According to M86 Security, a new version of trojan Zeus silently stole money from bank accounts around the beginning of last month. In the following article, TipsMake.com will introduce you to some polymorphic viruses - here is Virus.Win32.Virut and its ce variants
In the following article, TipsMake.com will introduce you to some polymorphic viruses - here is Virus.Win32.Virut and its ce variants Symptoms of a computer infected with WIN32.Zafi.B is that Windows Firewall will automatically appear accompanied by messages like 'Security Center Alert' ...
Symptoms of a computer infected with WIN32.Zafi.B is that Windows Firewall will automatically appear accompanied by messages like 'Security Center Alert' ... Do you suspect that your computer is infected with the virus, but the Anti-virus program on your computer is inefficient or your computer has not had any program to fight the
Do you suspect that your computer is infected with the virus, but the Anti-virus program on your computer is inefficient or your computer has not had any program to fight the Classified as extremely toxic Net-Worms, they have strong spread properties through computer networks, their most distinguishing feature is self-replication and spread without the
Classified as extremely toxic Net-Worms, they have strong spread properties through computer networks, their most distinguishing feature is self-replication and spread without the With the name P2P Worm - they are mainly spread through peer-to-peer sharing models like Kazaa, Grokster, EDonkey, FastTrack, Gnutella ...
With the name P2P Worm - they are mainly spread through peer-to-peer sharing models like Kazaa, Grokster, EDonkey, FastTrack, Gnutella ... The concept of backdoor is used to refer to malware, created to install and distribute malicious code to users' computers ...
The concept of backdoor is used to refer to malware, created to install and distribute malicious code to users' computers ... Viruses like these often have a mechanism to replicate the resources on the infected computer, unlike worms, unused viruses and exploit network services to replicate and spread
Viruses like these often have a mechanism to replicate the resources on the infected computer, unlike worms, unused viruses and exploit network services to replicate and spread Kaspersky Lab has discovered a worm called IM-Worm.Win32.Zeroll with 4 variants that can spread in all chat programs such as Yahoo Messenger, Skype ...
Kaspersky Lab has discovered a worm called IM-Worm.Win32.Zeroll with 4 variants that can spread in all chat programs such as Yahoo Messenger, Skype ... Classified as Trojan-PSW - for the purpose of stealing personal information, accounts include user login and password access on the infected computer. PSW is an acronym for
Classified as Trojan-PSW - for the purpose of stealing personal information, accounts include user login and password access on the infected computer. PSW is an acronym for