Description of the P2P-Worm.Win32.BlackControl.g template
With the name P2P Worm - they are mainly spread through peer-to-peer sharing (eg Kazaa, Grokster, EDonkey, FastTrack, Gnutella .), most of which operate in a fairly simple way: to invade Importing into P2P networks , all they need to do is copy themselves to shared folders - such folders are usually on local computers. And the P2P network model will 'accidentally' do the rest: whenever a request to find a file is done, it will notify the user that the file can be downloaded ( from infected computer).
In addition, there are a number of P2P-Worm types with a much more complex mechanism of action and infection: they mimic the network model of a specific data sharing system, and respond to all of them. requests, search queries from users.
This malware sample was discovered on August 18, 2010 at 13:59 GMT, beginning to spread and operating on August 18, 2010 at 20:24 GMT, fully informed. only after 2 days ie August 20, 2010 at 09:51 GMT.
Technical description
To operate, these worms block all user requests and redirect them all to a URL that contains malicious code. At the same time, they also come with specialized tools to send phishing messages to users. They are primarily transmitted via email and P2P peer networks. In essence, they are Windows PE EXE files, with a capacity of about 300KB and their source code is written in C ++ language.
When enabled, they will automatically copy executable files to Windows system folders:
% system% HPWuSchdq.exe
Also continue to extract the bundled packages and other executable files on the hard drive - these are essentially different parts of malicious programs:
% appdata% SystemProclsass.exe
And to ensure that they will be activated automatically every time the operating system starts, these Trojans create the following autorun keys in the registry:
[HKÑUSoftwareMicrosoftWindowsCurrentVersionRun]
"HP Software Updater v1.2" = "% system% HPWuSchdq.exe"
[HKLMSOFTWAREMicrosoftWindowsCurrentVersionpoliciesExplorerRun]
"RTHDBPL" = "% appdata% SystemProclsass.exe"
On the other hand, they manually 'register' into the list of Windows firewall security applications:
[HKLMSYSTEMCurrentControlSetServicesSharedAccessParameters
FirewallPolicyStandardProfileAuth orizedApplicationsList]
"% system% HPWuSchdq.exe" = "% system% HPWuSchdq.exe: *: Enabled: Explorer"
And they continue to create keys to store information and data:
[HKÑUIdentities]
"Curr version"
"Inst Date"
"Last Date"
"Send Inst"
"First Start"
"Popup count"
"Popup date"
"Popup time"
"KillSelf"
Analysis of Payload process
When the installation is successful, they will send the 'infection successful' message to the C&C server at the following address:
http:///contr***.com/inst.php? aid = blackout
Request the IP address information of the victim computer from the following website to determine the location:
http:///whatis***.com/automation/n09230945.asp
At the same time, they 'track' traces of the following browsers:
Internet Explorer
Opera
Google Chrome
Mozilla Firefox
If the user accesses the site with a header containing 1 or more of the following keywords:
cialis pharma mortgage insurance gambling health
hotel travel antivir antivirus pocker poker video vocations design graphic
football footbal estate baseball books money money spyware credit dating dating
myspace virus amazon iphone software iphone mobile music craigslist sport
medical school wallpaper military weather twitter fashion spybot trading
tramadol cigarettes cigarettes doctors flights airlines comcast
they will immediately stop and redirect them all to the following address:
http:///oxobla***.com/se.php? pop = 1 & aid = YmxhY2tvd
XQA9D8 & sid = & key =
with is a random number, and is one of the keywords listed above. These malicious scripts also track all search requests from users with the following Search Engine:
yahoo
live
msn
bing
youtobe
And the search data will be sent to the following URL:
http:///tetro***.com/request.php? aid = blackout & ver = 25
On the other hand, they collect all the email addresses stored in the computer and send the following pieces of spam to them:
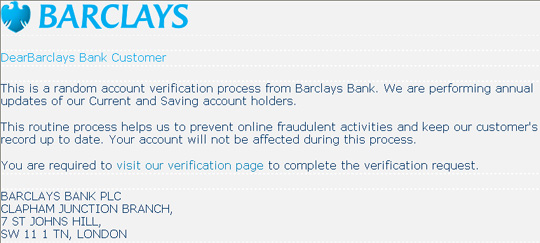
If you look a little bit, you will see the blue link 'visit our verification page' is a piece of fake message, which will take users to a phishing site of the form http:///barc***.ath.cx /LogIn.html is controlled directly by hackers. Once you have access to that website, the system will ask them to provide Barclays Bank online bank account information. At the same time, they will interrupt all activities of popular security and security programs such as Kaspersky Anti-Virus, Antivirus System Tray Tool, Avira Internet Security, AntiVir PersonalEdition Classic Service, Rising Process Communication Center .
At the same time, they will delete their information from the autorun keys of the registry:
[HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun]
And continue to prevent user access requests to sites that provide security and security services. Also remove User Account Control service in Windows Vista and 7:
[HKLMSOFTWAREMicrosoftSecurity Center]
"UACDisableNotify" = dword: 00000001
[HKLMSOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem]
"EnableLUA" = dword: 00000000
Continue, they cancel the following system services:
ERSvc - Error Reporting Service
wscsvc - Windows Security Center Service
Besides, they silently download patches from the following addresses:
http:///simfree***.com/update.php? sd = 2010-04-27 & aid = blackout
http:///posit***.com/update.php? sd = 2010-04-27 & aid = blackout
http:///rts***.com/update.php? sd = 2010-04-27 & aid = blackout
http:///qul***.com/update.php? sd = 2010-04-27 & aid = blackout
The next versions of them will be downloaded to file C: autoexec.exe and automatically activated. Then this file will be automatically deleted.
The process of spread
In essence, these malicious code spread through email form by automatically sending messages with executable files (* .exe format) attached under various names:


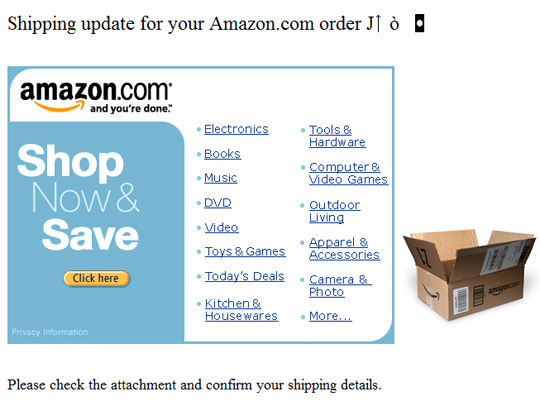
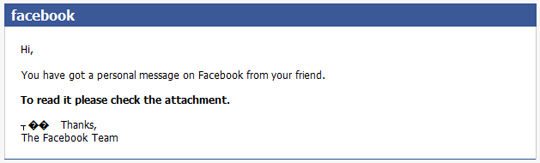
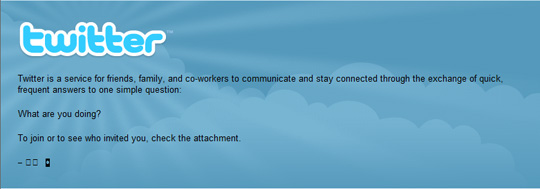
With P2P peer-to-peer models, they will copy themselves to shared folders on the network:
% ProgramFiles% winmxshared
% ProgramFiles% teslafiles
% ProgramFiles% limewireshared
% ProgramFiles% morpheusmy shared folder
% ProgramFiles% emuleincoming
% ProgramFiles% edonkey2000incoming
% ProgramFiles% bearshareshared
% ProgramFiles% grokstermy grokster
% ProgramFiles% icqshared folder
% ProgramFiles% kazaa lite k ++ my shared folder
% ProgramFiles% kazaa litemy shared folder
% ProgramFiles% kazaamy shared folder
with names like this:
YouTubeGet 5.6.exe
Youtube Music Downloader 1.3.exe
WinRAR v3.x keygen [by HiView] .exe
Windows2008 keygen and activator.exe
[+ MrKey +] Windows XP PRO SP3 valid-key generator.exe
Windows Password Cracker + Elar3 key.exe
[Eni0j0 team] Windows 7 Ultimate keygen.exe
Windows 2008 Enterprise Server VMWare Virtual Machine.exe
Winamp.Pro.v7.xx.PowerPack.Portable + installer.exe
Website Hacker.exe
[Eni0j0 team] Vmvare keygen.exe
VmWare 7.x keygen.exe
UT 2003 KeyGen.exe
Twitter FriendAdder 2.3.9.exe
Tuneup Ultilities 2010.exe
[antihack tool] Trojan Killer v2.9.4173.exe
Total Commander7 license + keygen.exe
Super Utilities Pro 2009 11.0.exe
Sub7 2.5.1 Private.exe
Sophos antivirus updater bypass.exe
sdbot with NetBIOS Spread.exe
[fixed] RapidShare Killer AIO 2010.exe
Rapidshare Auto Downloader 3.8.6.exe
Power ISO v4.4 + keygen milon.exe
[patched, serial not needed] PDF Unlocker v2.0.5.exePDF-XChange Pro.exe
[patched, serial not needed] PDF to Word Converter 3.4.exe
PDF password remover (works with all acrobat reader) .exe
Password Cracker.exe
Norton Internet Security 2010 crack.exe
Norton Anti-Virus 2010 Enterprise Crack.exe
Norton Anti-Virus 2005 Enterprise Crack.exe
NetBIOS Hacker.exe
NetBIOS Cracker.exe
[patched, serial need not] Nero 9.x keygen.exe
Myspace theme collection.exe
MSN Password Cracker.exe
Mp3 Splitter and Joiner Pro v3.48.exe
Motorola, nokia, ericsson mobil phone tools.exe
Microsoft.Windows 7 ULTIMATE FINAL activator + keygen x86.exe
Microsoft Visual Studio KeyGen.exe
Microsoft Visual C ++ KeyGen.exe
Microsoft Visual Basic KeyGen.exe
McAfee Total Protection 2010 [serial patch by AnalGin] .exe
Magic Video Converter 8.exe
LimeWire Pro v4.18.3 [Cracked by AnalGin] .exe
L0pht 4.0 Windows Password Cracker.exe
K-Lite Mega Codec v5.2 Portable.exe
K-Lite Mega Codec v5.2.exe
Keylogger unique builder.exe
Kaspersky Internet Security 2010 keygen.exe
Kaspersky AntiVirus 2010 crack.exe
IP Nuker.exe
Internet Download Manager V5.exe
Image Size Reducer Pro v1.0.1.exe
ICQ Hacker version Trial [brute] .exe
Hotmail Hacker [Brute method] .exe
Hotmail Cracker [Brute method] .exe
Half-Life 2 Downloader.exe
Grand Theft Auto IV [Offline Activation + mouse patch] .exe
Google SketchUp 7.1 Pro.exe
G-Force Platinum v3.7.6.exe
FTP Cracker.exe
DVD Tools Nero 10.xxxexe
Download Boost 2.0.exe
Download Accelerator Plus v9.2.exe
Divx Pro 7.x version Keymaker.exe
DivX 5.x Pro KeyGen generator.exe
DCOM Exploit archive.exe
Daemon Tools Pro 4.8.exe
Counter-Strike Serial key [Miona patch] .exe generator
CleanMyPC Registry Cleaner v6.02.exe
Brutus FTP Cracker.exe
Blaze DVD Player Pro v6.52.exe
BitDefender AntiVirus 2010 Keygen.exe
Avast 5.x Professional.exe
Avast 4.x Professional.exe
Ashampoo Snap 3.xx [Skarleot Group] .exe
AOL Password Cracker.exe
AOL Instant Messenger (AIM) Hacker.exe
AnyDVD HD v.6.3.1.8 Beta incl crack.exe
Anti-Porn v13.xxxexe
Alcohol 120 v1.9.x.exe
Adobe Photoshop CS4 crack by M0N5KI Hack Group.exe
Adobe Illustrator CS4 crack.exe
Adobe Acrobat Reader keygen.exe
Ad-aware 2010.exe
[patched, serial not needed] Absolute Video Converter 6.2-7.exe
In order to prevent and prevent this threat, users always fully update the identity database for the system's current security program, only use their security software. The company is reputable and well-known, or you can refer to the following list of security software.