In recent weeks, the Lapsus$ hacker group has appeared in the media. Security researchers are actively investigating the activities of the Lapsus$ hacker group.

On the morning of Sunday, March 20, 2022, the Lapsus$ hacker group announced that they were in possession of some Microsoft source code.

Microsoft recently released build 22579 Windows 11 to the Insider community in the Dev channel. The new build is mainly focused on improving existing features.

Canonical has just revealed the first details about the new Ubuntu logo design, which is expected to be applied starting with the next Long-Term Support update coming out in April.

Taking advantage of distribution channels of unapproved applications for testing purposes, malicious code has quietly sneaked into iOS users' devices.

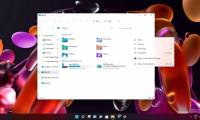
Context menus are a core component of the Windows user experience in general, and Windows 11 is no exception, especially when interacting with File Explorer.

Recently, security researcher Max Kellermann shared about a security flaw called 'Dirty Pipe'. It affects Linux Kernel 5.8 and above and even Android devices.

Somehow, the SharkBot anti-virus application has been approved on the Google Play Store.

GDPR stands for General Data Protection Regulation and aims to give people more control over their personal data.

A malicious code called Electron Bot has infiltrated Microsoft's official app store, Microsoft Store.

Usually, when updating Windows you will see a message that says: Do not turn off your computer.

Microsoft Teams is one of the most popular communication tools for business environments at the moment.

The Google homepage (Google.com) is one of the most familiar websites on the internet. You visit and are greeted by an interface that couldn't be simpler: the keyword search box

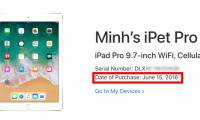
Recently, Apple has officially allowed users to check the original purchase / activation date of the device so users can know the actual life of the product. This is extremely

This is a new discovery by the developers on the newly released Android 13 Developer Preview.

The master decryption key of the Maze, Egregor and Sekhmet ransomware has just been posted by a user on the BleepingComputer forum. This person claims to be the developer of the

Mozilla has just released a security update to patch a critical security vulnerability that allows hackers to escalate privileges on Windows computers. This critical security flaw

Binarly, a security research company that specializes in dealing with firmware-related threats, revealed a very disturbing piece of information in a recent blog post.

International security researchers have just discovered a dangerous fake two-factor authentication application on the Android platform.

If you discover a remote arbitrary code execution vulnerability affecting Microsoft Outlook, you can sell it for up to $ 400,000.
 In recent weeks, the Lapsus$ hacker group has appeared in the media. Security researchers are actively investigating the activities of the Lapsus$ hacker group.
In recent weeks, the Lapsus$ hacker group has appeared in the media. Security researchers are actively investigating the activities of the Lapsus$ hacker group. On the morning of Sunday, March 20, 2022, the Lapsus$ hacker group announced that they were in possession of some Microsoft source code.
On the morning of Sunday, March 20, 2022, the Lapsus$ hacker group announced that they were in possession of some Microsoft source code. Microsoft recently released build 22579 Windows 11 to the Insider community in the Dev channel. The new build is mainly focused on improving existing features.
Microsoft recently released build 22579 Windows 11 to the Insider community in the Dev channel. The new build is mainly focused on improving existing features. Canonical has just revealed the first details about the new Ubuntu logo design, which is expected to be applied starting with the next Long-Term Support update coming out in April.
Canonical has just revealed the first details about the new Ubuntu logo design, which is expected to be applied starting with the next Long-Term Support update coming out in April. Taking advantage of distribution channels of unapproved applications for testing purposes, malicious code has quietly sneaked into iOS users' devices.
Taking advantage of distribution channels of unapproved applications for testing purposes, malicious code has quietly sneaked into iOS users' devices. Context menus are a core component of the Windows user experience in general, and Windows 11 is no exception, especially when interacting with File Explorer.
Context menus are a core component of the Windows user experience in general, and Windows 11 is no exception, especially when interacting with File Explorer. Recently, security researcher Max Kellermann shared about a security flaw called 'Dirty Pipe'. It affects Linux Kernel 5.8 and above and even Android devices.
Recently, security researcher Max Kellermann shared about a security flaw called 'Dirty Pipe'. It affects Linux Kernel 5.8 and above and even Android devices. Somehow, the SharkBot anti-virus application has been approved on the Google Play Store.
Somehow, the SharkBot anti-virus application has been approved on the Google Play Store. GDPR stands for General Data Protection Regulation and aims to give people more control over their personal data.
GDPR stands for General Data Protection Regulation and aims to give people more control over their personal data. A malicious code called Electron Bot has infiltrated Microsoft's official app store, Microsoft Store.
A malicious code called Electron Bot has infiltrated Microsoft's official app store, Microsoft Store. Usually, when updating Windows you will see a message that says: Do not turn off your computer.
Usually, when updating Windows you will see a message that says: Do not turn off your computer. Microsoft Teams is one of the most popular communication tools for business environments at the moment.
Microsoft Teams is one of the most popular communication tools for business environments at the moment. The Google homepage (Google.com) is one of the most familiar websites on the internet. You visit and are greeted by an interface that couldn't be simpler: the keyword search box
The Google homepage (Google.com) is one of the most familiar websites on the internet. You visit and are greeted by an interface that couldn't be simpler: the keyword search box Recently, Apple has officially allowed users to check the original purchase / activation date of the device so users can know the actual life of the product. This is extremely
Recently, Apple has officially allowed users to check the original purchase / activation date of the device so users can know the actual life of the product. This is extremely This is a new discovery by the developers on the newly released Android 13 Developer Preview.
This is a new discovery by the developers on the newly released Android 13 Developer Preview. The master decryption key of the Maze, Egregor and Sekhmet ransomware has just been posted by a user on the BleepingComputer forum. This person claims to be the developer of the
The master decryption key of the Maze, Egregor and Sekhmet ransomware has just been posted by a user on the BleepingComputer forum. This person claims to be the developer of the Mozilla has just released a security update to patch a critical security vulnerability that allows hackers to escalate privileges on Windows computers. This critical security flaw
Mozilla has just released a security update to patch a critical security vulnerability that allows hackers to escalate privileges on Windows computers. This critical security flaw Binarly, a security research company that specializes in dealing with firmware-related threats, revealed a very disturbing piece of information in a recent blog post.
Binarly, a security research company that specializes in dealing with firmware-related threats, revealed a very disturbing piece of information in a recent blog post. International security researchers have just discovered a dangerous fake two-factor authentication application on the Android platform.
International security researchers have just discovered a dangerous fake two-factor authentication application on the Android platform. If you discover a remote arbitrary code execution vulnerability affecting Microsoft Outlook, you can sell it for up to $ 400,000.
If you discover a remote arbitrary code execution vulnerability affecting Microsoft Outlook, you can sell it for up to $ 400,000.