A cybersecurity expert has made a stir in security circles by revealing a relatively detailed method of hiding up to 3MB of data inside an image on the social networking platform

We all know that the cybercrime world is constantly moving, parallel and has a close relationship with the development of the internet in general. That is why new hacking

Vulnerabilities are currently being tracked with identifiers CVE-2021-27365, CVE-2021-27363, and CVE-2021-27364.

International cybersecurity researchers recently found two completely new types of ransomware that are quite strange. They carry very different and rarely recorded features, which

Microsoft has just released a new update to MSERT, which comes with the ability to detect web shells deployed in recent Exchange Server attacks.

International security researchers have just stumbled upon a strain of ransomware that possesses rather strange behavior. Called 'Hog', this ransomware still enters the system and

Phishing attack is probably a term that is not unfamiliar to most internet users. In fact, it is also one of the most common forms of cyberattacks.

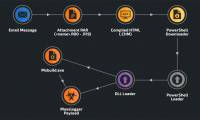
Masslogger - a notorious trojan that specializes in stealing credentials targeting Windows systems that officially have a dangerous 're-export'.

Traditionally, the holidays and year-end shopping holidays are always a golden opportunity for bad actors to launch a series of malicious campaigns on cyberspace to gain illegal

Google Project Zero is one of the highly regarded professional security organizations today. The team's findings are not only important to the Google product itself, but also for

Ransomware has become one of the top security threats in the past three years. The first ransomware strain and one of the worst nightmares in the history of global cybersecurity -

The Google Project Zero team has publicly revealed a security hole that exists in the Adreno GPU integrated on the Snapdragon chip.

RegretLocker was first discovered in October, and is considered to be a formally simple ransomware strain.

Zalo PC's critical vulnerabilities have just been announced by the CyberJutsu security research team.

An SS7 attack is a very dangerous attack method. An SS7 attack can be used to bypass two-factor authentication. So what specifically is the SS7 attack? What can a hacker do with an

This is a vulnerability that exists in the cryptographic authentication scheme used by the Netlogon Remote Protocol.

If the vulnerability in Cisco Jabber is exploited successfully, the hacker will gain control of the victim's computer.

Taking advantage of users' typos, typos, bad guys with a sharp mind have devised a Typosquatting attack technique.

An unresolved security weakness in Google Drive can be exploited by software attackers to distribute malicious files.

Google just patched a critical vulnerability affecting Gmail and G Suite. This vulnerability allows hackers to send fake identity emails to scam users.
 A cybersecurity expert has made a stir in security circles by revealing a relatively detailed method of hiding up to 3MB of data inside an image on the social networking platform
A cybersecurity expert has made a stir in security circles by revealing a relatively detailed method of hiding up to 3MB of data inside an image on the social networking platform We all know that the cybercrime world is constantly moving, parallel and has a close relationship with the development of the internet in general. That is why new hacking
We all know that the cybercrime world is constantly moving, parallel and has a close relationship with the development of the internet in general. That is why new hacking Vulnerabilities are currently being tracked with identifiers CVE-2021-27365, CVE-2021-27363, and CVE-2021-27364.
Vulnerabilities are currently being tracked with identifiers CVE-2021-27365, CVE-2021-27363, and CVE-2021-27364. International cybersecurity researchers recently found two completely new types of ransomware that are quite strange. They carry very different and rarely recorded features, which
International cybersecurity researchers recently found two completely new types of ransomware that are quite strange. They carry very different and rarely recorded features, which Microsoft has just released a new update to MSERT, which comes with the ability to detect web shells deployed in recent Exchange Server attacks.
Microsoft has just released a new update to MSERT, which comes with the ability to detect web shells deployed in recent Exchange Server attacks. International security researchers have just stumbled upon a strain of ransomware that possesses rather strange behavior. Called 'Hog', this ransomware still enters the system and
International security researchers have just stumbled upon a strain of ransomware that possesses rather strange behavior. Called 'Hog', this ransomware still enters the system and Phishing attack is probably a term that is not unfamiliar to most internet users. In fact, it is also one of the most common forms of cyberattacks.
Phishing attack is probably a term that is not unfamiliar to most internet users. In fact, it is also one of the most common forms of cyberattacks. Masslogger - a notorious trojan that specializes in stealing credentials targeting Windows systems that officially have a dangerous 're-export'.
Masslogger - a notorious trojan that specializes in stealing credentials targeting Windows systems that officially have a dangerous 're-export'. Traditionally, the holidays and year-end shopping holidays are always a golden opportunity for bad actors to launch a series of malicious campaigns on cyberspace to gain illegal
Traditionally, the holidays and year-end shopping holidays are always a golden opportunity for bad actors to launch a series of malicious campaigns on cyberspace to gain illegal Google Project Zero is one of the highly regarded professional security organizations today. The team's findings are not only important to the Google product itself, but also for
Google Project Zero is one of the highly regarded professional security organizations today. The team's findings are not only important to the Google product itself, but also for Ransomware has become one of the top security threats in the past three years. The first ransomware strain and one of the worst nightmares in the history of global cybersecurity -
Ransomware has become one of the top security threats in the past three years. The first ransomware strain and one of the worst nightmares in the history of global cybersecurity - The Google Project Zero team has publicly revealed a security hole that exists in the Adreno GPU integrated on the Snapdragon chip.
The Google Project Zero team has publicly revealed a security hole that exists in the Adreno GPU integrated on the Snapdragon chip. RegretLocker was first discovered in October, and is considered to be a formally simple ransomware strain.
RegretLocker was first discovered in October, and is considered to be a formally simple ransomware strain. Zalo PC's critical vulnerabilities have just been announced by the CyberJutsu security research team.
Zalo PC's critical vulnerabilities have just been announced by the CyberJutsu security research team. An SS7 attack is a very dangerous attack method. An SS7 attack can be used to bypass two-factor authentication. So what specifically is the SS7 attack? What can a hacker do with an
An SS7 attack is a very dangerous attack method. An SS7 attack can be used to bypass two-factor authentication. So what specifically is the SS7 attack? What can a hacker do with an This is a vulnerability that exists in the cryptographic authentication scheme used by the Netlogon Remote Protocol.
This is a vulnerability that exists in the cryptographic authentication scheme used by the Netlogon Remote Protocol. If the vulnerability in Cisco Jabber is exploited successfully, the hacker will gain control of the victim's computer.
If the vulnerability in Cisco Jabber is exploited successfully, the hacker will gain control of the victim's computer. Taking advantage of users' typos, typos, bad guys with a sharp mind have devised a Typosquatting attack technique.
Taking advantage of users' typos, typos, bad guys with a sharp mind have devised a Typosquatting attack technique. An unresolved security weakness in Google Drive can be exploited by software attackers to distribute malicious files.
An unresolved security weakness in Google Drive can be exploited by software attackers to distribute malicious files. Google just patched a critical vulnerability affecting Gmail and G Suite. This vulnerability allows hackers to send fake identity emails to scam users.
Google just patched a critical vulnerability affecting Gmail and G Suite. This vulnerability allows hackers to send fake identity emails to scam users.