Typosquatting, attacking techniques, extortion with typos, typos
What is Typosquatting?
Typosquatting, also known as URL hijacking, poisoning a website or spoofing a URL, is a form of cybersquatting attack. This attack is based on typos, typos of the user when entering the website address into the browser.
If you enter the wrong website address, users run the risk of accessing a phishing website, containing malicious code, advertising .
There are 5 common types of errors that are commonly used for Typosquatting:
(Compare with root domain eg diachiweb.com)
- Common spelling mistakes like diachuweb.com
- Typing errors like diachiwbe.com
- A domain name similar to diachiwebs.com
- Type in the wrong domain name like diachiweb.org
- Type in the wrong domain name like diachiweb.cm, .co, .om. Each missing character in the .com domain name can lead to a fake, dangerous website.
Other types of Typosquatting attacks:
- Combosquatting: There's no mistake but adding an arbitrary, seemingly reasonable word to deceive users like diachiweb-uytin.com. According to statistics, Cobosquatting is 10 times more popular than Typosquatting.
- Doppelganger domain: Ignore dot thietkediachiweb.com instead of thietke.diachiweb.com
- Add extra element: a.thietkeweb.com
- Add words to create an attractive, visual domain name like diachiweb-hay.com or diachiweb-ngon.com.
When entering a bad guy's site, users may be fooled into believing that they are accessing the real website because of the look, layout, or similarly copied content.
Spam emails also sometimes use Typosquatting to trick users into visiting malicious or fake websites.
 Typosquatting is an attack based on the user frequently misspelling, typing errors
Typosquatting is an attack based on the user frequently misspelling, typing errors
What are the bad guys doing Typosquatting for?
Bad guys with sharp minds often buy misspelled domain names, typos from famous websites, banking websites . for illegal profit. They make money by the following behaviors:
- To resell the domain name with typographical errors, misspellings to the owner of the original domain name
- Monetize advertising on websites with typographical errors and typos
- Redirects visitors to a competitor's website
- Redirect visitors back to the original website but through the affiliate link and earn commissions from that affiliate program.
- Creates a fake website with a design similar to the original to steal user login information to steal money, this type of attack usually targets banking websites
- To install malicious code or adware that generates revenue on the user's device
- Collect users' emails when they mistype them and then use them for malicious purposes
- Typing and misspelling domain names are also bought by the owners of the original domain to prevent bad guys from taking advantage of them.
Examples of Typosquatting attacks
In 2006, a typewritten Google domain name "Goggle.com" appeared, when users visited a phishing / fraud site. Then, between 2011 and 2012, the Goggle.com domain was pointed to Google.com.
In 2018, Goggle.com once again directed users to a website containing ad malware. Currently, when you visit Goggle.com you will see a statistics blog page.
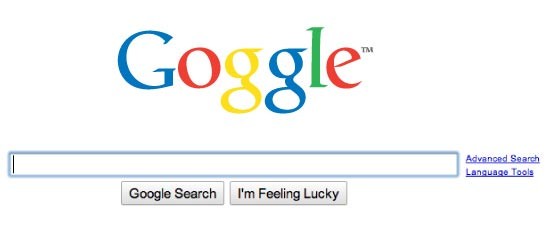 Google websites are frequently the subject of Typosquatting
Google websites are frequently the subject of Typosquatting
Another example is yuube.com, the typo version of youtube.com. When entering yuube.com, YouTube users will be redirected to a malicious website, asking users to install a security check utility (essentially a malware) on the device.
Currently, yuube.com no longer links to a malicious website, but instead is a page containing ads.
How to prevent Typosquatting attacks
You should carefully vertical the content, carefully censor the content when typing to avoid mistyping or mistaking urls for malicious websites that are deliberately trapping you. Malicious websites usually look very similar to real ones, if you quickly look at them, you will not be able to distinguish and will be trapped by bad guys using you.
The advice is to always look in the address box of your browser to distinguish, this is simple but will help you avoid the Typosquatting attack completely.
It is possible to sue Typosquatting attackers
To attack Typosquatting, the bad guys will have to register using the domain names with typos, typos. Under the Uniform Domain Name Dispute Resolution Policy (UDRP), root domain owners can sue name registrants free of typos and typos with the World Intellectual Property Organization (WIPO).
The owner of the root domain name will have to prove that the registered faulty domain name is identical or confusingly similar to the original domain name. In addition, there should be evidence that the owner of the faulty domain name does not have legitimate rights and interests to the root domain name and is using the faulty domain with malicious intent.
You should read it
- ★ How to use the shortcut function in Unikey?
- ★ Customizable English spell checker dictionary in Word 2007
- ★ The software for checking Vietnamese spelling errors is the most standard
- ★ 6 ways to undo and redo when you make a mistake or accidentally delete a note in the Notes application
- ★ Summary of popular network attacks today