Masslogger - malicious code possesses the ability to steal all the login information of Chrome, Edge Outlook of the target
Masslogger - a notorious trojan that steals login credentials targeting Windows systems has officially hit a dangerous 'comeback' in a new phishing campaign, aimed at stealing credentials Import from Microsoft Outlook, Google Chrome and a series of popular instant messaging applications today.
Primarily targeting users in Turkey, Latvia and Italy starting mid-January, these attacks were essentially related to the use of MassLogger - a .NET-based malware ability to interfere with the process of static analysis (static analysis).
Through initial analysis, experts say there is a clear similarity between these new attacks and an earlier campaign targeting users in Bulgaria, Lithuania, Hungary, Estonia, Romania and Spain in January. 9, 10 and 11, 2020. The similarities come from both the attack method and the malicious agent.
MassLogger was first discovered in April last year and has been storming since then. However, the recently discovered MassLogger variant is an all-new 'upgrade', making them more dangerous and difficult to cope with.
'Although the activities of the Masslogger trojan have been relatively well documented before, we found a significant difference in this campaign. For example, the malware uses the compiled HTML file format to initiate the infection sequence, "said the researchers from Cisco Talos, the group responsible for monitoring Masslogger's activity.
Compiled HTML (or .CHM) is a proprietary online help format developed by Microsoft, and is used to provide topic-based reference information.
The new wave of attacks began with phishing emails containing "legitimate looking" headlines and extremely sophisticated camouflage, seemingly relevant to a particular business.
Regardless of the subject, the attachments in the fake email follow the same format: The RAR file has a fairly long header with various strings of characters (for example, "70727_YK90054_Teknik_Cizimler.R09").
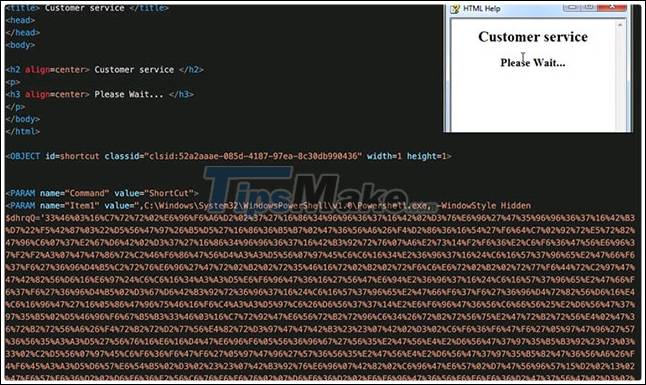
These attachments contain a single compiled HTML file that, when opened, displays the message "Customer service ', but is in fact embedded with scrambled JavaScript code to create the HTML page. , from there, contains the PowerShell downloader to connect to the legitimate server and fetch the downloader that is ultimately responsible for launching the MassLogger malware payload.
In addition to extracting accumulated data via SMTP, FTP or HTTP, the latest version of MassLogger (version 3.0.7563.31381) also adds the ability to steal login information from messaging apps Pidgin, Discord, NordVPN, Outlook, Thunderbird, Firefox, QQ Browser, and Chromium-based browsers like Chrome, Edge, Opera, and Brave.
The new offensive campaign along with a more dangerous variant of Masslogger is still being closely watched.
You should read it
- How many types of malware do you know and how to prevent them?
- What is malware analysis? How are the steps taken?
- Learn about polymorphic malware and super polymorphism
- What is Malware? What kind of attack is Malware?
- What is Safe Malware? Why is it so dangerous?
- How to remove Trojan, Virus, Worm or Malware?
- The Purple Fox malware targets vulnerable Windows systems worldwide
- Symbian S60 attack appears again
May be interested
- Discovered a group of hackers who use secret code to spy on 21 countries
 a group of secret hackers specialized in using android malicious code and other sophisticated reconnaissance tools to steal messages, call history, documents of the press, military, corporation and many other targets at 21 newly discovered country in beirut.
a group of secret hackers specialized in using android malicious code and other sophisticated reconnaissance tools to steal messages, call history, documents of the press, military, corporation and many other targets at 21 newly discovered country in beirut. - Warning: The new Facebook virus, a malicious code that is spreading rapidly through Messenger
 from yesterday (december 18, 2017), a new type of malicious code has appeared and raged in vietnam. this malicious code is not too sophisticated but is spreading very fast through facebook messenger because it is sent from the friends in the friend list.
from yesterday (december 18, 2017), a new type of malicious code has appeared and raged in vietnam. this malicious code is not too sophisticated but is spreading very fast through facebook messenger because it is sent from the friends in the friend list. - How to block pop-up windows on Chrome, Coc Coc, Edge, Firefox browsers
 how to block pop-up windows on chrome, coc coc, edge, firefox browsers. advertising is the main source of free websites on the internet. however, some sites are for personal gain, so they include ads that contain malicious code or ads that lead to phishing websites.
how to block pop-up windows on chrome, coc coc, edge, firefox browsers. advertising is the main source of free websites on the internet. however, some sites are for personal gain, so they include ads that contain malicious code or ads that lead to phishing websites. - UXSS bug on Microsoft Edge allows hackers to steal user information
 last week, microsoft rolled out updates to its edge browser to fix two security flaws, including a uxss vulnerability that could be exploited to inject and execute arbitrary code in the content of any web page. which.
last week, microsoft rolled out updates to its edge browser to fix two security flaws, including a uxss vulnerability that could be exploited to inject and execute arbitrary code in the content of any web page. which. - Researchers create malware based on artificial intelligence
 deeplocker is unrecognized and 'performs malicious behavior as soon as this ai code detects the target via face detection, location or voice'.
deeplocker is unrecognized and 'performs malicious behavior as soon as this ai code detects the target via face detection, location or voice'. - Ransomware STOP started installing Trojans to steal victim passwords
 in addition to encrypting files on the system, ransomware stop strains have also started quietly installing the azorult password stealing trojan on the victim's computer to steal account information, electronic wallet, and file desktop ...
in addition to encrypting files on the system, ransomware stop strains have also started quietly installing the azorult password stealing trojan on the victim's computer to steal account information, electronic wallet, and file desktop ... - Detecting malicious code 'super dangerous'
 security researchers have discovered a very malicious type of malicious code that has infected and stole user information on millions of pcs.
security researchers have discovered a very malicious type of malicious code that has infected and stole user information on millions of pcs. - Warning: New malware can hijack Vietnamese users' access to Facebook and Gmail
 a new line of malicious code using plugx rat is attacking vietnamese users.
a new line of malicious code using plugx rat is attacking vietnamese users. - New Edge is very similar to Chrome, so is there any reason to switch from Chrome to Edge?
 after years of listening to comments from users, microsoft decided to build a new edge version, which can both ensure the maintenance of the advantages and completely overcome all the downsides of the old version.
after years of listening to comments from users, microsoft decided to build a new edge version, which can both ensure the maintenance of the advantages and completely overcome all the downsides of the old version. - Malicious ad campaigns abuse Chrome to steal 500 million iOS user sessions
 in recent times, many large malvertising attacks targeted ios users from the united states and many european union countries have been deployed.
in recent times, many large malvertising attacks targeted ios users from the united states and many european union countries have been deployed.










 Warning: The malware campaign hides the shadow of gift emails from Amazon
Warning: The malware campaign hides the shadow of gift emails from Amazon Google Project Zero reveals a serious privilege escalation vulnerability in Windows
Google Project Zero reveals a serious privilege escalation vulnerability in Windows What is Ransomware Task Force (RTF)?
What is Ransomware Task Force (RTF)? Google revealed a critical flaw in Qualcomm's Adreno GPU
Google revealed a critical flaw in Qualcomm's Adreno GPU RegretLocker: A new strain of ransomware that targets Windows virtual machines
RegretLocker: A new strain of ransomware that targets Windows virtual machines Zalo PC has a serious RCE error, you should be careful when receiving attachments
Zalo PC has a serious RCE error, you should be careful when receiving attachments