Basic operations to remove fake security software
TipsMake.com - Recently, the number of computers infected with fake security software has increased significantly, especially those with the 2012 characters included, for example:
XP Antispyware 2012
XP Antivirus 2012
XP Security 2012
XP Home Security 2012
XP Internet Security 2012
Vista Antispyware 2012
Antivirus Vista 2012
Vista Security 2012
Vista Home Security 2012
Vista Internet Security 2012
Win 7 Antispyware 2012
Win 7 Antivirus 2012
Win 7 Security 2012
Win 7 Home Security 2012
Win 7 Internet Security 2012
However, the process of recognizing and destroying such destructive software is not as difficult and complicated as many people think. Basically, this entire work will be conducted in the following order:
- Fix errors in Registry.
- 'Destroy' processes that are silently active and constantly generated by malware.
- Use tools that are capable of reviewing, detecting and recovering errors and vulnerabilities in the operating system.
Some tools you should use like:
- FixNCR is used to fix Registry errors.
- RogueKiller software to destroy automated processes generated by counterfeit software.
- Software supports Malwarebytes.
The first step is to make sure that the Windows 'Registry' system works correctly with the * .exe files working normally. If you have not completed this step, the infected files will continue to spread and affect other files in the system, so using future support programs will become meaningless.
The next step is to turn off the operation of automated processes generated by these fake programs using the RogueKiller tool mentioned above. Specifically, we conducted another test on Microsoft Windows XP SP3 and Windows 7 Ultimate SP1 operating systems, the results were very positive, the program detected most of the symptoms of the following fake software. when infecting the system, it is also easy to fix all the errors (mostly related to hosts files, proxies, dns .). First, download the RogueKiller.exe file to your computer, operating under Administrator in Windows Vista or 7:
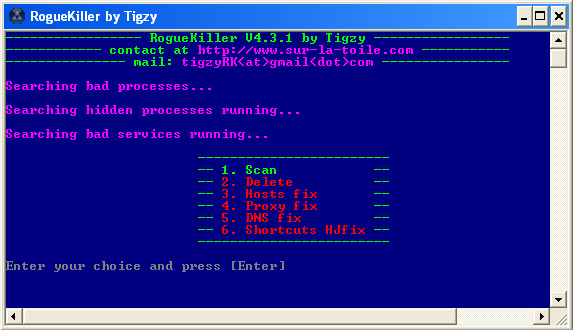
The main interface of the program with 6 different options
Start with the first option - Scan to perform a system check and check, then refer to the information generated in the report file:
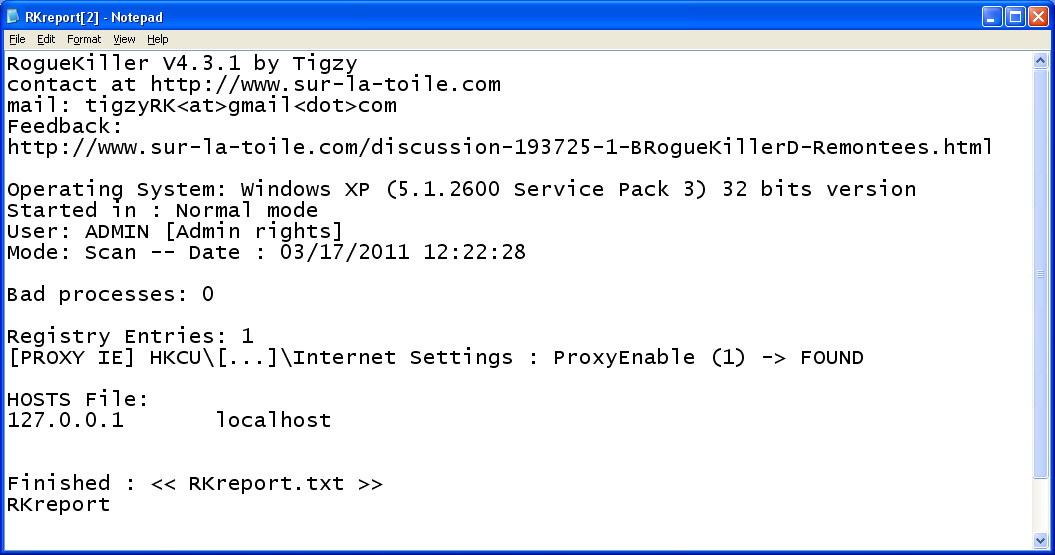
To continue, install a security program that recognizes highly malicious programs, typically MalwareBytes, along with a quick update support file. After scanning the entire system (it is recommended to use the Full Scan option after the update), destroy the malware, fix the infected files and problems with the operating system vulnerability, You should restart the computer. With only 3 simple steps, the probability of our success is about 90%. And to ensure the computer system is absolutely safe, you should equip yourself with security measures based on the 'top' software in the world today such as PC Tools Spyware Doctor, Avira Antivir Premium, Kaspersky Internet Security, ESET Smart Security . Wish you success!
You should read it
- ★ 'Battle' between KeyScrambler and KeyLogger
- ★ Microsoft has a group of 'elite' hackers that specialize in attacking Windows to keep the operating system safe
- ★ More than 1 million computers are infected by hackers
- ★ Android operating system is the top target of hackers
- ★ 4 reasons why white hat hackers love to use Kali Linux