
'Great technique' Autorun virus removal by hand
first, it must be affirmed, the solution to spread the virus through windows autorun function has many ways. these practices are quite manual, but it helps implementers better

first, it must be affirmed, the solution to spread the virus through windows autorun function has many ways. these practices are quite manual, but it helps implementers better

dynamic lock is one of the new features integrated on windows 10 creators update version. this feature automatically locks the computer every time a user leaves his or her desk.

on windows 8 and windows 10 versions, microsoft integrates on a feature system called secure boot, and by default this feature has been activated. the secure boot feature supports

on windows 10 is integrated a lot of login options, users can choose, including pin code. if you're using a mobile device, you're probably familiar with pin codes, an
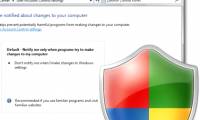
if you have been using windows vista or windows 7, you will probably feel a lot of pain when you have to get the system approval every time you install an application. this
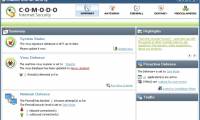
with the newly released version, comodo internet security (cis) further enhances two technologies: secure dns and defense +
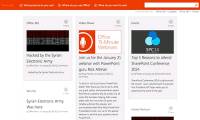
the syrian electronic army hackers team (sea) promised that they would continue to attack microsoft, and today the team hacked the official microsoft office blog just hours after

according to cso statistics, more than 80% of organizations and businesses have been using services from 2 or more public cloud infrastructure providers, and nearly two-thirds of

internal attacks are becoming more and more popular in recent years.

we live in an era of internet globalization. the internet invades every corner of the street, is present in every living room and appears in every breath of life. in addition to