'Great technique' Autorun virus removal by hand
Perhaps, with the current mobile information era, not having a USB is . rare.Sharing and storing data through this small but extremely handy gadget has become extremely popular.

However, with the spread of viruses, malicious code becoming more and more powerful, it is rare for anyone who has never "cried badly " because of the harmful effects these malicious software created when spreading through the public. This tool shares data.
First, it must be affirmed, the solution to spread the virus through Windows Autorun function has many ways. This article is only a summary of the author's experiences that have been accumulated over a long period of use and learning on many forums. These practices are quite manual, but it helps implementers better understand the security and security principles of the system.
1. On Windows XP:
Unfortunately for users of long-lived Windows versions, such as Windows XP, these operating systems lack a lot of security "blocks" to counteract the artifacts from the Autorun virus.
However, with the following approach you can 'catch the enemy ' to permanently solve this shenanigans virus.
Step 1: Open Run (press Windows + R key combination or click Start button > Run ).
Step 2: Type secpol.msc to enter the operating window of the system's security policies.
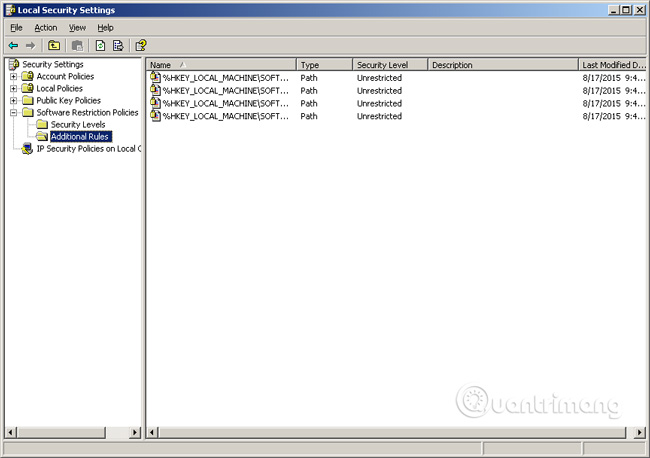
Step 3: Access the Software Restriction Policy / Additional Rules path.
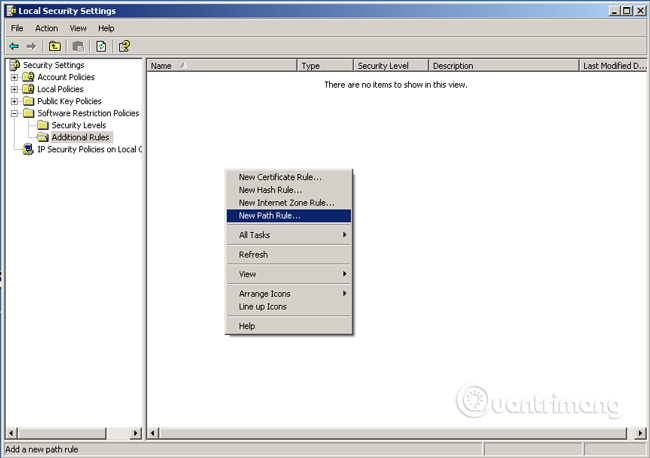
Step 4: Delete all the paths in this section, right-click and select New Path Rule .
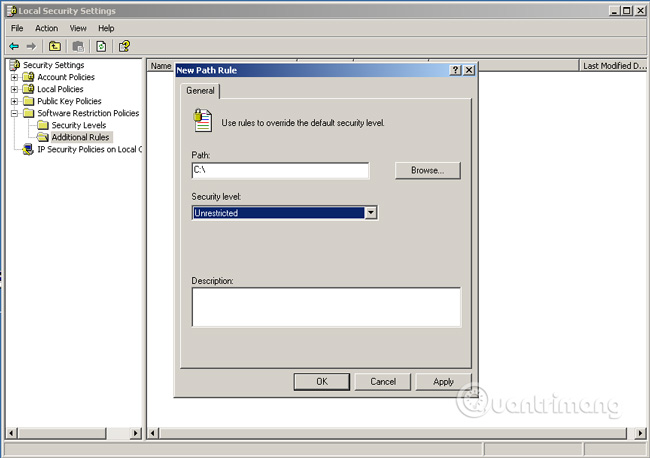
Select the existing partitions in your computer. For example, if your device is divided into 2 partitions, C and D, you select New twice these drives. Select the applicable rule as Unrestricted .
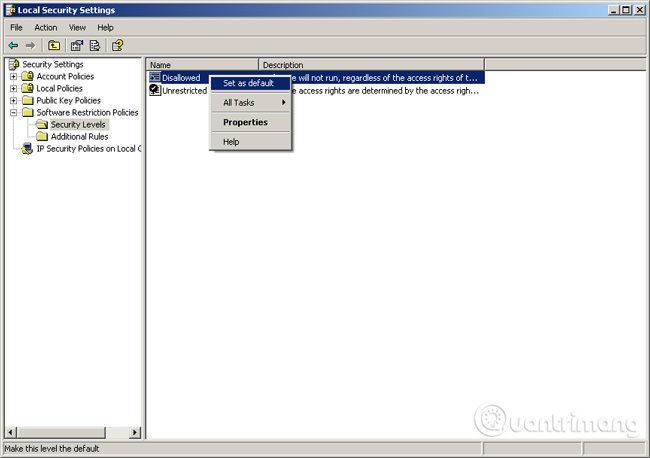
Step 5: Go to the Security Levels branch , go to Disallowed, select Set as Default.
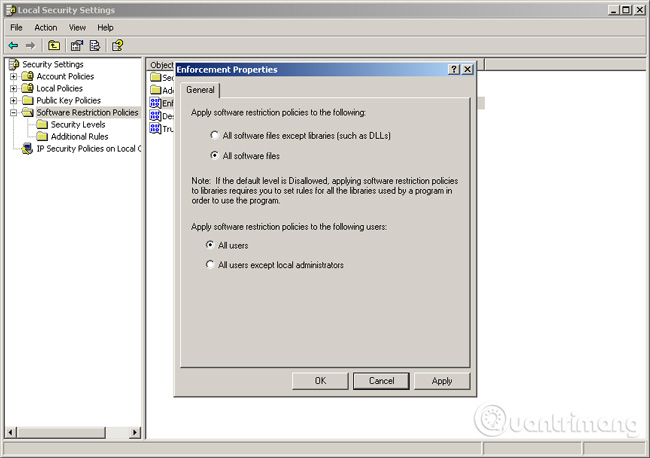
Step 6: Go back to Software Restriction Policy, click Enforcement, switch to All Software Files and OK.
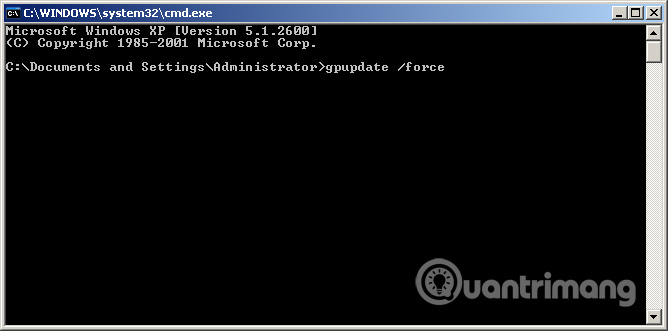
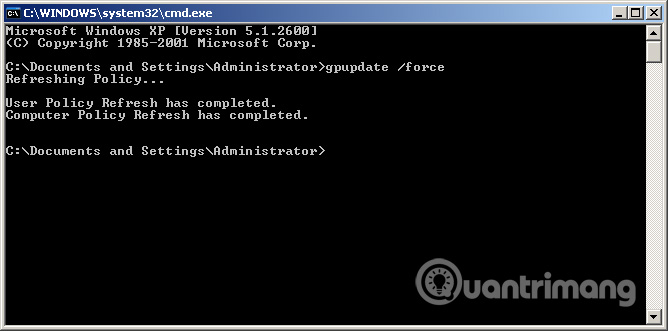
Step 7: Restart the machine or run the 'gpupdate / force' command in the Command Prompt window so that the policy is applied.
From now on, only the program file in the drives created in the Additional Rules section will be able to start. Drives that are not on this list (ie, USB drives added) do not run the program files themselves.
Of course, Autorun files cannot run and spread viruses to your computer.
2. With Windows 7, Windows 8:
With these operating systems, mechanisms for preventing automatic drives from starting are available, so it is quite simple. We can follow the steps with Windows XP, but below is an easier way.
Step 1 : Open the Run dialog box .
Step 2: Type gpedit.msc , Enter to access the administration policy Menu on the system.

Step 3: Access the Computer Configuration / Administrative Templates / System / Removable Storage Access path.
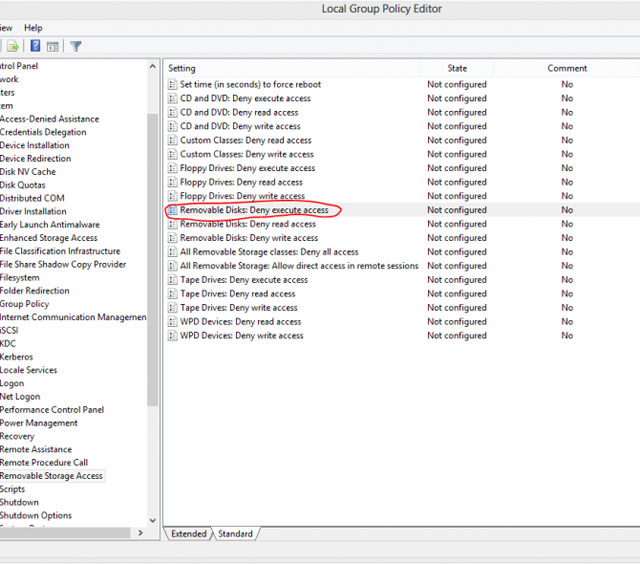
Step 4 : Double-click Policy: Removable Disks: Deny Execute access, select Enable , Apply and OK. Exit the Policy Administration window .
Step 5: Restart the machine or run the 'gpupdate / force' command in the Command Prompt window so that the policy is applied.
At this point, the machine will not automatically run files in USB drives or external drives.
Please note some points:
- These methods only prevent the virus from automatically spreading to the computer through the function of automatically running the program files, if you copy the virus file to the computer and then start it . it must be through the virus removal program.
- To launch the program (such as portable versions of the software, Silent Install versions for example), compress the file and run it directly in the compressed file.This time, the files will run from the temporary directory of the drive on the computer, so there are no problems.
- This does not prevent the virus from spreading to the USB.
Good luck!