Comodo Internet Security - 'Tightening' system security
With the new version released, Comodo Internet Security (CIS) continues to enhance two technologies: Secure DNS allows to manage domain name access through standby server, Defense + technology helps the web surfing process become more secure. Full and fast. Software compatible with XPSP2 / Vista 32bit version, 39MB capacity. Interested readers can stay here
CIS is a combined product between Comodo Antivirus and Comodo Firewall. This is one of the few free security software in the best category today. With this combination, your computer will be absolutely secure before 'enemies in the outside'.
The program has a simple installation method, after downloading, double-click on the CIS.Setup file. During the installation process, as soon as the dialog box informs Email Address, click Next to skip, and then select two installation components, Comodo Antivirus and Firewall . Done, click Next , then select the next line I do NOT want to join . continue, click the Make Ask.com my default search provider line, Install Comodo Hopsurf toolbar and Make Hopsurf.com my homepage , click Next to continue. If the computer is connected to the network, in this step the program will give you the option to use the Secure DNS feature, click on the line I would like to use Comodo Secure DNS Server .

Program interface includes main tags:
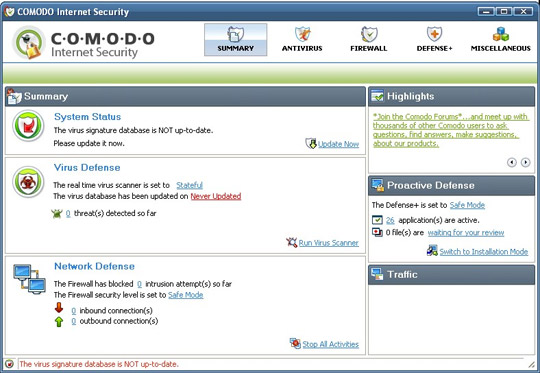
- Summary : Provides information about the status of the system such as updated data about the virus, updated status of the program, network defenses (blocking / blocking strange addresses accessed from the party). out). To set the level and configuration of the system, in the Realtime virus scanner line is set to large , you click the Stateful link. Here, you can choose the level of alert (automatic background scan mode) according to three levels: Disabled , Stateful (detection and removal when entering), On Access (blocking before intrusion) ), the default setting is set to Stateful state.
Detection helps you to identify scanning problems, you will have the option to activate Scan Memory at start , Automatically update the database before scanning virus (auto update). Virus data before scanning), the default Heuristics scanning / level function is Low , you click on Medium , the function Do not scan larger files of Manual Scanning , select Scan archive files . Done, click OK to accept. only perform file scanning below the specified volume (by typing the corresponding volume). If you want to specify additional compression format when scanning, you access the card.
- Antivirus : Provides functions related to scanning and "processing" of viruses found on the system. Includes six main tasks:
+ Run a scan : Execute the scan task, including two provided scripts: My computer (full computer scan), Critical Areas (scanning sensitive areas). You choose one of the two tasks to perform, then click the Scan button. If you want to create another script (specify some folders to scan), click Create new scan button, then Add the folder you want to put in the list, press the button -> , click Apply , name in Profile, click Apply again to confirm.
+ Update virus database : Update the latest virus data
+ Quarantined items : The area for "treating" the viruses that the system finds, this function is arranged similarly to other antivirus software, including: Delete (only delete the infected files selected from the list) , Clear (delete all infected files in the list), Restore (restore infected files to the original location).
+ View Antivirus Events : Review the scan log
+ Scheduled Scans : Specify the scan time automatically according to the scheduling mechanism, click the Add button and assign the time according to the form provided.
+ Scan profiles : Set up scan scenarios
+ Scanner settings : Set up scanning options
- Firewall : Provides powerful firewall system, easy to control the I / O of the network process, including eight main tasks:
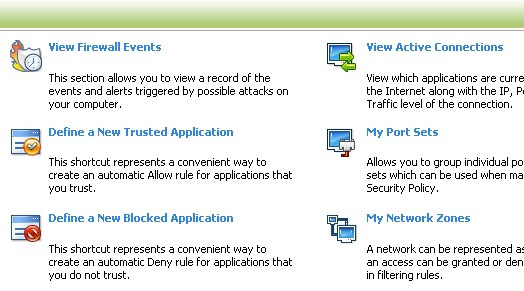
+ View firewall events : Allows monitoring and recording of events or factors that can attack your computer.
+ Define a new trusted application : Locate 'safe' objects in the white list quickly, the specified object can belong to the group: executables (executables), all applications All applications, temporary files, startup folders, running processes (running processes). Click the Select button, then select one of the above groups to include on the list. Done, click Apply.
+ Define a new blocked application : Same as above, but instead of allowed (allow), the applications included here will be locked.
+ Stealth ports wizard : Set up rules for firewalls. After this task is activated, you will have three options: Define a new trusted network . (the system will be hidden, not visible by another system, except for the designated secure network area via IP. or My Network Zone of Comodo Firewall), Alert me to incomming connections stealth . (notify incoming and requested connections), Block all incoming connections (not visible by the entire network and prevent any connection sent to).
+ View active connections : View all ports (ports) and IP connection to computers, protocols and traffic during network connection.
+ My port sets : Allows grouping of ports with the same function as the name, which makes network management and monitoring easy. To do this, click the Add button> A new port sets, name a new Port, and enter a new port.
+ My Network Zones : Network access area, you can use the address specified by CIS or set up your own network address area, by clicking the Add new network zone button to name and A new address to specify network IP address. My Network Zones will be used with the Stealth ports wizard function.
+ My blocked network zones : Creating a range containing the restricted access area, this will help you remove unsafe addresses by putting them on the blacklist. Then, these addresses will be locked (block).
- Defense + : In addition to anti-virus and firewall features. This is the third feature added in this version. It enhances system protection tools such as file and folder protection, . this card contains nine tasks:
+ View defense + events : Track events about memory access applications, registry, .
+ My protected files : Allows the program to perform the function of automatically protecting files and folders according to a predetermined list or editing from users, this feature is similar to the KIS Self-defense. Files, folders or extensions are included in the list. By default, they cannot be edited, which helps to limit the changes in file structure when viruses are invaded.
+ My blocked files : Set the right to prohibit access to files and folders in the list.
+ My pending files : Whenever executing an exe file, the program will proceed with the previous scanning process, if it feels unsafe, they will be put into the pending area waiting for processing from the user.
+ My own safe files : The area contains safe files, in this area you can add / delete files to a safe area or from a safe area into the database.
+ View active process list : This area will display information about the running process on the system, the identification process will be displayed as a directory tree for you to monitor.
+ My trusted software vendors : This area will help you define which software vendors are rated as safe, thereby helping the software identification process easier.
+ My protected registry keys : This feature allows the program to protect the keys in the registry, in order to limit the changes that occur when viruses enter, by default the program will provide some important keys such as: Load, Run, Starup, Policies, etc. However, you can specify additional keys by clicking the Add button, selecting the Registry Entries branch. To remove a key from the list, click the Remove button.
+ My protected COM files : Allows creating security keys with components related to the interface such as Windows shell, Windows management, Classes, . To edit the key, you press the Group button.
- Miscellaneous : Provides functions related to program use. Here, there are two important cards:
+ Settings : Adjust program settings such as automatic update mode of new version of the program, display language, proxy. In particular, Parental Control feature, allows you to set a password for the program.
+ Check for updates : Check the new version of the program.
In addition, there are other interesting features that you can explore more through the help of the program