Learn about SpeakUp - New Malware targets Linux servers
With electronic money today is very popular, so the attractiveness of installing virtual money digging tools on servers without the owner's permission also increases. Making virtual money requires processing power, and this has inspired hackers to stealthily install exploit tools on other hardware and let victims do everything for them. A recent malware chain called SpeakUp is using backdoor attacks to exploit on Linux-based servers. This is particularly worrying, as software becomes the target of SpeakUp, which accounts for about 90% of the top million domains in the United States today!
Learn about malware SpeakUp
- How to speak SpeakUp
- How far has the SpeakUp spread?
- What does SpeakUp do?
How to speak SpeakUp

The SpeakUp function is to exploit vulnerabilities in ThinkPHP. After installation, it creates a backdoor that allows it to contact the main control server. It notifies the server that the server has become a new victim. The control server records the violation in the database of the compromised servers, so it monitors all locations where the server has control. Then the control server sends malware some instructions on what to do next.
Currently, SpeakUp only seems to be interested in installing virtual money digging tools on the servers it infects. He used Monero as a currency and at the time of writing, the malware had accumulated about $ 4500 from these attacks. It also gives itself advanced permissions, allowing for self-installation even after rebooting.
More worrying is how it spreads. It proactively searches for another server in the same infected server's network, if it sees that the server has the same error, it will automatically attack and spread to that server. This makes it very difficult for users to assess the severity and how to remove this malware, as it can spread itself.
How far has the SpeakUp spread?
Currently, SpeakUp is focusing on attacking a vulnerability found in systems only in China. Thus, the majority of infected servers are in China. However, some serious damage to other Asian and South American countries has also been recorded, after the SpeakUp Cross-border program seeks new networks to infect.
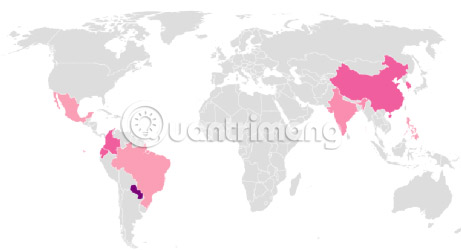
Currently, other countries in the world do not seem to be affected. However, this malware may be required to attack servers, using a different exploit method, which will allow it to infect servers based in the United States, so the section This software may not exist for too long.
What does SpeakUp do?

Currently, the answer is correct. All SpeakUp is doing is just installing an exploit tool to get more Monero from the victim. However, the main problem is how this malware is set up to perform the tasks sent by the control server. Although this malware is only installing exploit tools at the present time, nothing prevents the bad guys from sending a new task to infected servers.
This is what makes it really worrying for these servers. Nothing proves this malware has that capability. All we can predict now is that it is capable of receiving commands from an unknown third party. That these commands require what is not yet determined, but it certainly is not a good thing!
As a new malware that attacks most of the top domains, SpeakUp is a big threat. Currently, it is simply making money for the owner, but not knowing how it will grow in the future.
Does this new development worry you? Let us know in the comments below!