How to Tell if Your Asus Router Is One of the Thousands of Hacked Models
More than 9,000 Asus routers have been quietly hacked, and if you own one of those routers, there's a good chance yours is on the list. Luckily, you don't have to wait for things to go wrong to find out.
- What can hackers actually do if they gain access to your Wi-Fi router?
Over 9,000 ASUS Routers Compromised in Ongoing Attack
A cybersecurity firm, GreyNoise, claims to have identified an 'ongoing exploitation campaign' affecting thousands of ASUS routers connected to the Internet .
The attackers behind the campaign, who have not yet been identified, gained unauthorized and persistent access to more than 9,000 ASUS routers, the report states. Based on their tactics, which included stealthy initial access and abuse of built-in system features to maintain control, GreyNoise said the activity indicated a highly resourced and capable adversary, consistent with the attackers seen in advanced, long-term campaigns.
The attackers are believed to have used brute-force login attempts and two different authentication methods. After successfully gaining access to the ASUS router, they exploited a known vulnerability (CVE-2023-39780) to run arbitrary commands. Through this, they enabled SSH access if it was not already active and injected their own SSH public key, granting persistent access.
Since the SSH key is stored in non-volatile memory ( NVRAM ) rather than the file system, it persists across reboots and firmware updates. The attackers went one step further by disabling logging, erasing any trace of their access. Surprisingly, the report claims that the attackers did not appear to have installed any type of malware, which ultimately begs the question — why attack? GreyNoise said in its report:
It appears to be part of a covert operation to assemble a distributed network of backdoor devices — potentially laying the foundation for a future botnet.
In case you don't know, a botnet is a network of compromised computers or devices that are used to carry out fraud and attacks, all remotely controlled by attackers. Usually, the best solution in such cases is to update the router's firmware . However, doing so won't help here because the attacker's changes are stored in the router's NVRAM.
Is your Asus router one of the thousands of hacked models?
Luckily, there is a way to check if hackers have access to your ASUS router. You can do this by logging into your router's firmware and going to the Administration section . Then, look for the Enable SSH option under the Service heading .
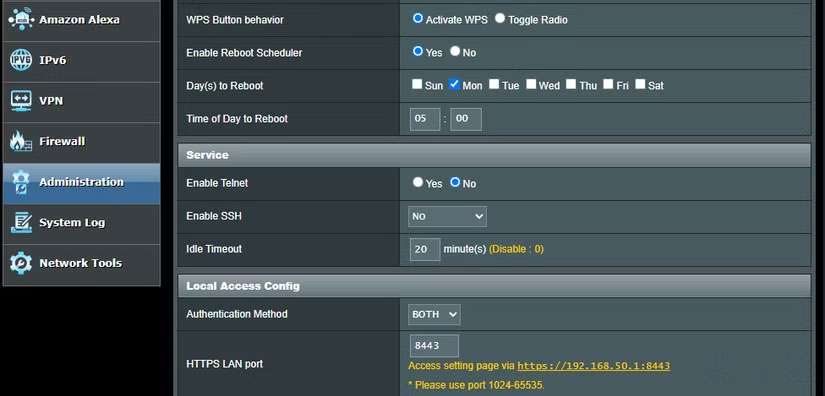
If your router is compromised, you will see SSH access enabled on an unusual port, specifically port 53282, along with the following truncated SSH public key: ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAo41nBoVFfj4HlVMGV+YPsxMDrMlbdDZ.
Since a firmware update won't fix this issue, your best bet is to factory reset your router . Asus also recommends removing or disabling the SSH entry, along with blocking the following IP addresses: 101.99.91.151, 101.99.94.173, 79.141.163.179 , and 111.90.146.237 .
If you're among the "lucky ones," now is a good time to update your router's firmware to avoid falling victim to this bug in the near future. That's because Asus has fixed the CVE-2023-39780 bug that allows hackers to run arbitrary commands on routers.