MVVM (Model-View-ViewModel) is a software architectural pattern designed to separate application components, improving maintainability and development.

VDC can be understood as a set of cloud resources that help businesses store and process data online, eliminating the need to set up and maintain on-site data centers.

Flush DNS is to clear the DNS cache, clearing the DNS Cache will help the computer update the website information and access the website quickly.

ETL stands for Extract - Transform - Load, commonly used in big data, mostly in data warehouse.

Software-Defined Storage, or SDS for short, is a software-based method of data storage management.

RBAC, short for Role-Based Access Control, is a method of managing access to systems and data based on a user's role in an organization.

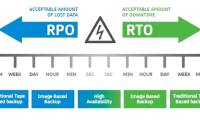
RTO and RPO both play an important role in minimizing losses to businesses when incidents occur.

DBMS stands for Database Management System. This is the system software that serves the activities of creating and managing databases.

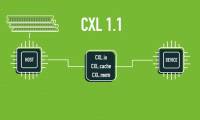
CXL is expected to be a coherent interconnect interface for caching to connect any number of CPUs, memories, processing accelerators (especially FPGAs and GPUs), and other

The main difference between 4K and 8K lies in the number of pixels included in the resolution.

A file with the 000 extension is most likely an Indexing Service data file used to store locations where the Windows operating system can perform file searches.

Technically, 12K resolution does exist… currently mostly in prototypes and high-end professional use cases rather than consumer displays.

Desktops are generally more durable than laptops. They are easier to upgrade and repair, making them a great choice for long-term use. However, many people still stick with laptops

For advanced Windows users, the command line has long been a powerful tool for managing and interacting with the operating system. But PowerShell offers enhanced automation and

LTPO is replacing AMOLED, which has been the standard in the premium segment for years. But what exactly is LTPO, and is it better than AMOLED?

These sites offer free games to download and have been operating for years, which begs the question: Is abandonware legal?

This is one of the simple step-by-step tutorials provided by Microsoft help for users. This article describes how to apply the predefined security templates in Windows Server 2003.

Split Tunneling performs the task of dividing Internet traffic. With Split Tunneling, you have the ability to route Internet traffic through a VPN or a local network.

UPnP is a network protocol (or set of network protocols). These protocols outline a specific communication method that all kinds of devices can use to instantly communicate with

When you use a virtual private network (VPN), your Internet activity becomes more private, but not all of your online traces disappear.
 MVVM (Model-View-ViewModel) is a software architectural pattern designed to separate application components, improving maintainability and development.
MVVM (Model-View-ViewModel) is a software architectural pattern designed to separate application components, improving maintainability and development. VDC can be understood as a set of cloud resources that help businesses store and process data online, eliminating the need to set up and maintain on-site data centers.
VDC can be understood as a set of cloud resources that help businesses store and process data online, eliminating the need to set up and maintain on-site data centers. Flush DNS is to clear the DNS cache, clearing the DNS Cache will help the computer update the website information and access the website quickly.
Flush DNS is to clear the DNS cache, clearing the DNS Cache will help the computer update the website information and access the website quickly. ETL stands for Extract - Transform - Load, commonly used in big data, mostly in data warehouse.
ETL stands for Extract - Transform - Load, commonly used in big data, mostly in data warehouse. Software-Defined Storage, or SDS for short, is a software-based method of data storage management.
Software-Defined Storage, or SDS for short, is a software-based method of data storage management. RBAC, short for Role-Based Access Control, is a method of managing access to systems and data based on a user's role in an organization.
RBAC, short for Role-Based Access Control, is a method of managing access to systems and data based on a user's role in an organization. RTO and RPO both play an important role in minimizing losses to businesses when incidents occur.
RTO and RPO both play an important role in minimizing losses to businesses when incidents occur. DBMS stands for Database Management System. This is the system software that serves the activities of creating and managing databases.
DBMS stands for Database Management System. This is the system software that serves the activities of creating and managing databases. CXL is expected to be a coherent interconnect interface for caching to connect any number of CPUs, memories, processing accelerators (especially FPGAs and GPUs), and other
CXL is expected to be a coherent interconnect interface for caching to connect any number of CPUs, memories, processing accelerators (especially FPGAs and GPUs), and other The main difference between 4K and 8K lies in the number of pixels included in the resolution.
The main difference between 4K and 8K lies in the number of pixels included in the resolution. A file with the 000 extension is most likely an Indexing Service data file used to store locations where the Windows operating system can perform file searches.
A file with the 000 extension is most likely an Indexing Service data file used to store locations where the Windows operating system can perform file searches. Technically, 12K resolution does exist… currently mostly in prototypes and high-end professional use cases rather than consumer displays.
Technically, 12K resolution does exist… currently mostly in prototypes and high-end professional use cases rather than consumer displays. Desktops are generally more durable than laptops. They are easier to upgrade and repair, making them a great choice for long-term use. However, many people still stick with laptops
Desktops are generally more durable than laptops. They are easier to upgrade and repair, making them a great choice for long-term use. However, many people still stick with laptops For advanced Windows users, the command line has long been a powerful tool for managing and interacting with the operating system. But PowerShell offers enhanced automation and
For advanced Windows users, the command line has long been a powerful tool for managing and interacting with the operating system. But PowerShell offers enhanced automation and LTPO is replacing AMOLED, which has been the standard in the premium segment for years. But what exactly is LTPO, and is it better than AMOLED?
LTPO is replacing AMOLED, which has been the standard in the premium segment for years. But what exactly is LTPO, and is it better than AMOLED? These sites offer free games to download and have been operating for years, which begs the question: Is abandonware legal?
These sites offer free games to download and have been operating for years, which begs the question: Is abandonware legal? This is one of the simple step-by-step tutorials provided by Microsoft help for users. This article describes how to apply the predefined security templates in Windows Server 2003.
This is one of the simple step-by-step tutorials provided by Microsoft help for users. This article describes how to apply the predefined security templates in Windows Server 2003. Split Tunneling performs the task of dividing Internet traffic. With Split Tunneling, you have the ability to route Internet traffic through a VPN or a local network.
Split Tunneling performs the task of dividing Internet traffic. With Split Tunneling, you have the ability to route Internet traffic through a VPN or a local network. UPnP is a network protocol (or set of network protocols). These protocols outline a specific communication method that all kinds of devices can use to instantly communicate with
UPnP is a network protocol (or set of network protocols). These protocols outline a specific communication method that all kinds of devices can use to instantly communicate with When you use a virtual private network (VPN), your Internet activity becomes more private, but not all of your online traces disappear.
When you use a virtual private network (VPN), your Internet activity becomes more private, but not all of your online traces disappear.