8 Sophisticated Ways Hackers Use to Steal Your Security Answers
If you think your security questions are a reliable backup to your password, you might be in for a surprise. Hackers have clever ways to figure out those answers, and it's often easier than you think.
8. Social media monitoring
Social media is a goldmine for anyone trying to piece together your personal story—and hackers know it. Most people share important life events online, like birthdays, anniversaries, pet names, and where they went to school. But for someone trying to crack your security questions, it's not nostalgia, it's intelligence.
Let's say your security question is "What's your favorite movie?". Double-scrolling through account X will reveal your undying love for The Lion King. Or maybe your Instagram bio says "Max's dog mom," and that's the answer to the question "What was your first pet's name?".
This type of spying doesn't require fancy tools. All a hacker needs is your name, your profile, and a little patience. They'll dig through old posts, tagged photos, and even comments your friends leave. If your privacy settings are wide open, you're essentially handing the answers over to the bad guys.
Even private accounts aren't safe. If a hacker tracks you, perhaps through a fake profile, your posts will be accessible. A harmless post on your timeline can become a trail to your account.
7. Use fake "quiz"
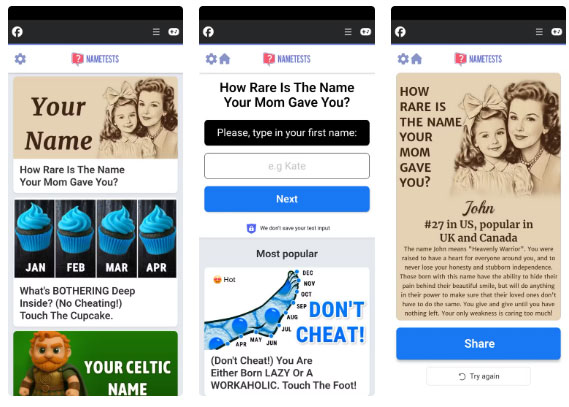
Chances are, you've seen a version of those fun quizzes on social media that ask questions like "Can we guess your age based on your favorite foods?" They're often considered harmless pranks, but they're one of the most common privacy mistakes you can make on social media.
Hackers, or at least shady data collectors, use these quizzes to collect exactly the kind of personal information usually associated with security questions. They lower your guard with humor and personalization so you forget that you're essentially handing over your digital identity to strangers.
6. Look up detailed information in public profile
Sometimes hackers don't need any tricks at all. They just use public profiles.
Marriage certificates, property records, voter registrations, and even old yearbooks can be rich sources of answers to security questions. Information like your mother's maiden name, childhood address, or place of birth can often be revealed with just a few searches.
For example, if your security question is 'What city were you born in?', an old birth certificate can easily reveal that. A determined hacker doesn't even need to know who you are. All they need is your name and a little persistence. A public profile can do the rest.
5. Search through old forum posts
You might think that old forum posts are safe because most forums are anonymous. But hackers know that anonymity isn't invincible—especially when people accidentally leave behind traces.
Maybe you used a forum username that was part of your email address. Maybe you posted about your hometown, your first pet, or your high school mascot. Even small details like the year you graduated or your favorite sports team can start to link back to you.
No hacking skills required either. A patient hacker can search old forums, cross-reference usernames, or Google a few keywords along with your name. Forums you barely remember participating in may still have public archives circulating, silently leaking bits of your personal history.
Anonymity is helpful, but if you leave enough of a trail, old posts can still betray you. And when hackers are hunting for the answers to your security questions, even the smallest clues can be useful.
4. Using leaked data from other websites
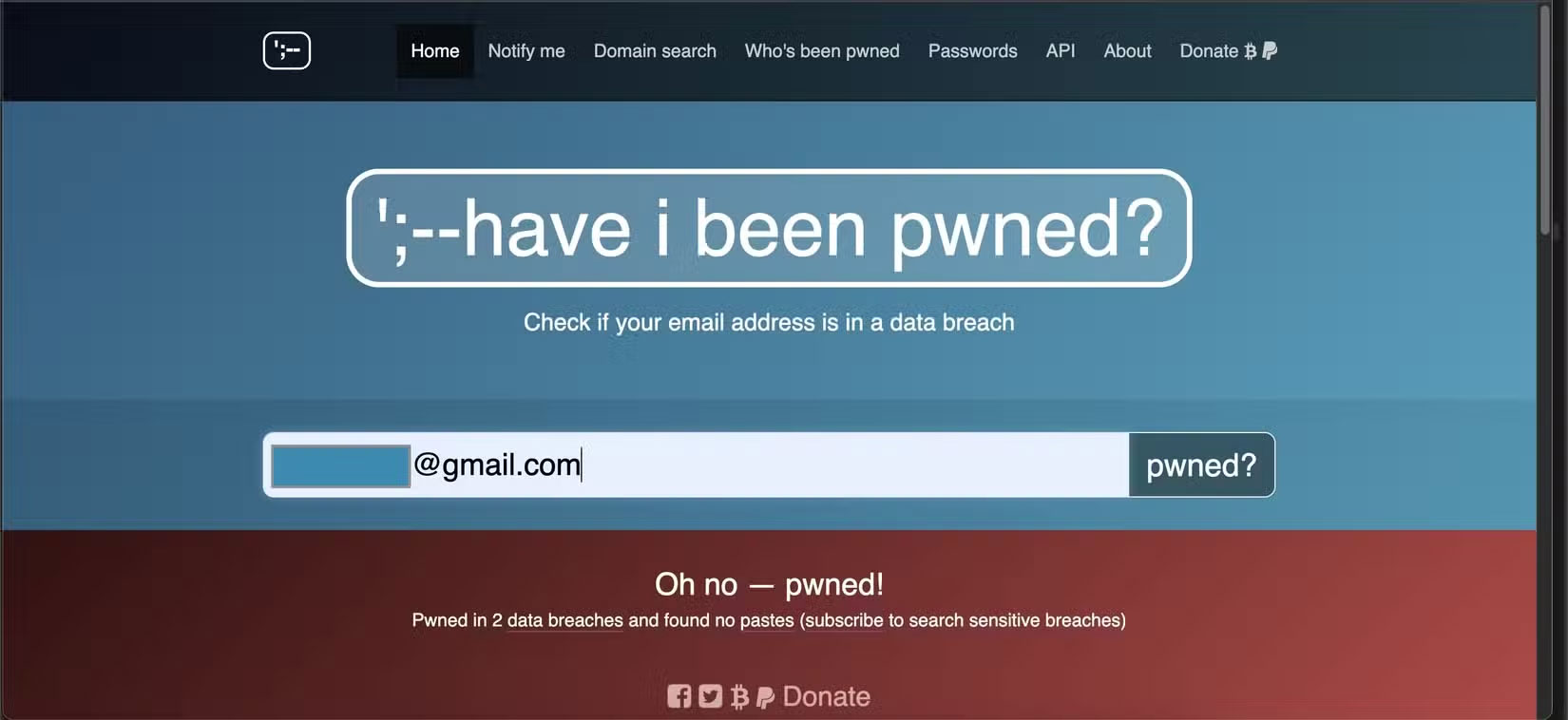
A data breach is like a jackpot for hackers. When a website is hacked, it's not just usernames and passwords that are leaked. Sometimes the answers to users' security questions are also exposed.
For example, let's say you set up an account on a forum years ago. You used "Arsenal" as the answer to the question "What's your favorite sports team?" and forgot about it. If that site were compromised and your answer was unencrypted, hackers could use that answer to access your existing important accounts.
Reusing security answers across multiple sites is just as dangerous as reusing passwords. When your information is exposed, hackers use specialized tools to cross-reference it. Use a tool like Have I Been Pwned to see if your data has been exposed. And always treat security answers like one-time passwords: Unique for every account.
3. Create a fake support chat
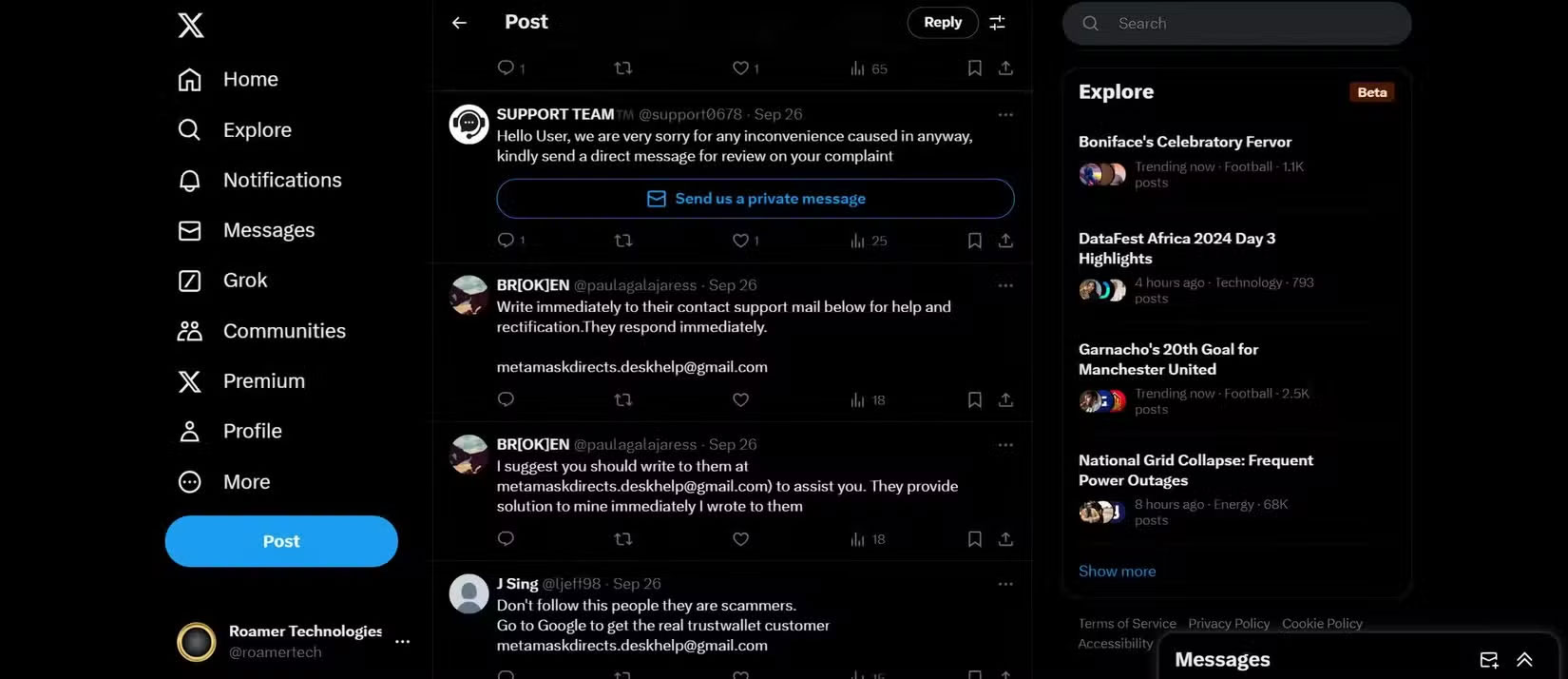
This one is more subtle but incredibly effective: fake customer support chat.
It usually starts with an email, DM, or pop-up window that mimics your bank, email provider, or favorite store. The fake support agent will ask you to confirm your identity by answering security questions.
These fake chats often replicate branding, language, and even times, like when a real site is down. And because they're personal, you're more likely to comply quickly without thinking. Once you provide those answers, hackers can gain access to your account by resetting your login information.
The golden rule here is simple. Legitimate support representatives will never ask you for your security questions via chat, email, or direct message. If you receive such a request, close the chat and verify directly through the official website.
2. Trick your friends into sharing details
Hackers know that even if you're careful, your friends may not be. It's surprising how easy it can be to get personal information by tricking people you trust.
Sometimes, hackers start with a profile posing as an old classmate or mutual friend. They engage in conversation, asking about 'old times,' or starting a seemingly harmless game. Before your friend knows it, they've casually mentioned where you grew up, the name of your childhood pet, or even your favorite teacher.
Even something as simple as a Facebook anniversary post can be revealing. Someone tagging you in an old yearbook photo or joking about your first car can give hackers exactly what they need without you having to type a word.
This is a sneaky tactic because it seems so natural. Friends trust each other. Hackers take advantage of that trust to dig up their information. If you're serious about security, remind those close to you to be vigilant, too.
1. Guess the popular answer

Sometimes hackers don't even need to spy. They just guess.
Questions like 'What's your favorite color?' lead to predictable answers like blue. Pet names often involve Max, Bella, or Lucky. Even things like 'Mom's maiden name' often lead to common last names like Smith, Johnson, or Garcia. Other answers are similarly predictable: Many people answer 'dream vacation' with 'Paris,' for example.
Sometimes hackers automatically guess, repeating the most common answers until they get it right. Without strong site protections like locking out after a certain number of failed attempts, they may only need a few tries.
The bottom line is simple. Think of the answer to your security question as your password. Don't tell the truth if it's too easy to guess, make it a passphrase, something meaningless, or better yet, use a password manager to store random answers.
Security questions may seem like harmless backups, but to hackers, they're an unlocked side door. Hackers don't always need to brute force their way in. Sometimes, they can just use the details you leave lying around to break in.