Why hackers switch to phishing attacks beyond email and how to prevent them
Email used to be the primary way for hackers to launch phishing attacks, but the trend has changed. More and more phishing links are being sent through channels other than email, such as social media, messaging apps, SMS, and even malicious search engine ads. This poses a new challenge for cybersecurity teams that have become accustomed to blocking everything right from the inbox.
The reason for this shift comes from the modern work environment itself. Employees today not only work via email but also connect, share documents, and communicate using a variety of other distributed applications. This change makes the scope of exposure to malicious content much wider. While email used to be the only 'gateway' for hackers to find, now any platform that has messaging, chat, or link sharing features can be exploited.
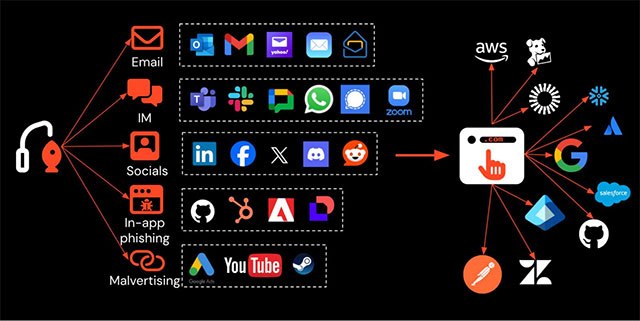
It is worth noting that attacks outside of email are often overlooked, simply because the majority of cybersecurity data today comes from email security service providers. With email no longer central, attacks via social media or instant messaging are easily overlooked. Even when businesses have additional measures such as web proxies, modern phishing toolkits with sophisticated source code obfuscation techniques can easily bypass them.
In reality, when a phishing incident is detected on social media, there is almost no way for businesses to handle it thoroughly. It is impossible to recall sent messages like emails, nor can it create rules to block the sender. At most, you can only report the offending account, but often by the time the platform handles it, the attacker has achieved his goal and moved on to another 'prey'.
More worryingly, the line between personal and business is increasingly blurred. Employees frequently use company devices to log into personal accounts like LinkedIn, WhatsApp, or even Google. This means that a seemingly harmless social media scam can become the starting point for a serious incident. The 2023 Okta attack is a testament to this, where hackers exploited login data synced from an employee's personal Google account, leading to widespread consequences for corporate systems.
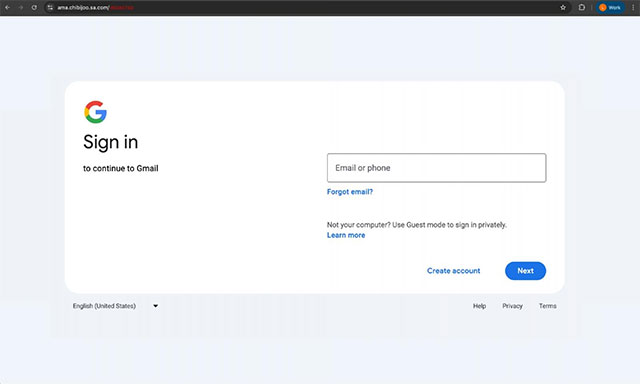
Modern phishing campaigns are even more sophisticated thanks to personalization. Malicious ads can be tailored to the victim's geographic location, device type, or even email domain. Phishing pages are also designed to only be shown to specific audiences, making detection even more difficult.
The consequences of a compromised account can be far more serious than you might think. Hackers can not only compromise data in the native app, but also use single sign-on (SSO) to extend their access to a range of other services. From there, they can easily launch internal attacks, using Slack, Teams, or other enterprise apps as a springboard for infection.
It can be seen that traditional anti-phishing solutions that focus on email are no longer enough. To cope, businesses need a new layer of defense that can directly monitor web interactions in real time, detect and block attacks as soon as users load the page. Browser-based security platforms with the ability to identify AiTM attacks, session hijacking or malicious extensions will be a necessary direction in the fight against increasingly sophisticated forms of phishing outside of email.