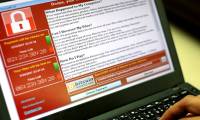
There were 12,449 serious data breaches recorded in 2018, an increase of 424% compared to 2017
a recent statistical report showed alarming facts. specifically, the number of confirmed data violations in 2018 has reached 12,449 cases, an increase of 424% compared to 2017.