What do you know about the first 'cyber attack' in the world?
If you are interested in the field of technology, network security, you certainly are no stranger to the name WannaCry. WannaCry, also known as WannaDecryptor 2.0, is a malicious computer virus that encrypts data and ransom money, infecting more than 230,000 computers in 150 countries around the world, causing heavy damage, even causing some organizations to close. WannaCry is just one of many examples of dangers as well as incalculable transformations of cyberattacks in the present era. No day has passed without news of some big company voicing its claim that its data has been violated. Not to mention that these cyberattacks are now considered an 'inevitable' part of the internet world, they touch every country, region, business, and even every household.

- Deep Learning - new cybersecurity tool?
Temporarily restraining the 'contemplative' reality of today's global cyber security situation, we try to go back to the past, returning to the early days of the concept of 'cyber attack'. Do you know when the world's first cyber attack occurred? Many would have thought of the cult incident that was made by Robert Morris in 1988. At that time, Robert Morris was a 20-year-old male student, studying at Cornell University. The student spread a total of 99 malicious code lines known as the infectious Morris Worm and caused a large number of PCs in various countries to stop working. The goal of this hacker is to count the number of PCs connected to the Internet and thereby know how big the Internet is. This action caused Morris to be arrested in 1989, becoming the first person to be convicted under the Law on Computer Abuse and using computer for fraudulent purposes passed by the US Congress in 1986. In addition Morris also had to pay a fine of up to $ 10,000.

- The list of the 10 most famous hackers in the world
However, in fact, the first cyberattack occurred a long time ago, when the optical cable called the semaphore is still in widespread use long before the internet and computer systems. Which we are using now comes into being. The first cyberattack occurred in 1834, when Vietnam was still in the feudal dynasty of the Nguyen Dynasty under the rule of King Minh Mang.
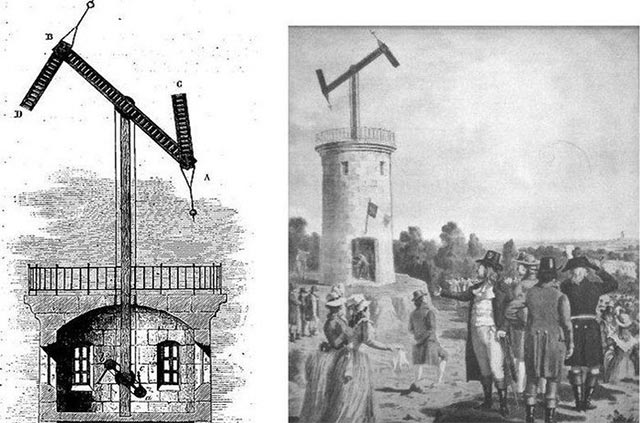
Talk a little bit about the semaphore. Basically, the semaphore (or so-called visual communication) is a tool used to transmit information through a signal vehicle visible to the high tower along with the rotary axis (pivoting blades) or the rotor blades ( paddles), shutters in a matrix shape (matrix), or hand-held flags . Information is encoded according to the position of the mechanical components, and read when the slabs or flags are in a specified location. More specifically, Semaphore consists of a series of towers, in which each tower is attached with a mobile wooden arm in the upper part to form a branch. Various configurations of these branches have been used to represent a variety of symbols, letters and numbers. Experts responsible for operating each tower will use the viewfinder to verify the configuration of the adjacent tower and then simulate and reconstruct them in their own towers, which will enable them to Send messages through towers located in different regions much faster. At that time, the semaphore network was reserved for government use, however in 1834, brothers François and Joseph Blanc devised a way to "hack" into this system to serve personal interests. mine.

- Young people are too confident when talking about online security!
At that time, François and Joseph Blanc were two investors, trading government bonds on the Bordeaux stock exchange, and did not forget to closely monitor the situation of the Paris stock exchange. The Paris Stock Exchange was then a major market, while secondary markets such as Bordeaux were always lagging behind the main market due to the time it took for information to be transmitted by post. Thus, if traders foresee information transmitted between exchanges, they can earn a lot of money by 'predicting' the market's dynamics.
Capturing this reality, the brothers François and Joseph Blanc have come up with the idea of 'hacking' the semaphore communication system being used by the French government. The Blanc brothers bribed a telegraph operator to transmit information about the stock market, and this person also had an accomplice in Paris, whose task was to help him get detailed information in the market. This important transaction. The telegraph operator will then send information to the operator of the intermediate station in Tours, then transfer from Bordeaux to the semaphore system. This person deliberately hid the message by adding the codes used for government messages. This message was then deciphered by another executive who was brother Blanc, 'stationed' near the line of the Bordeaux trading market. As such, François and Joseph Blanc obtained information from the Paris trading floor faster than other investors, helping them earn significant profits.
- McAfee expert explained how deepfake and AI are drilling through the cyber security wall
The incident lasted for about 2 years until one day the sick Tours operator was unable to continue his work. He tried to persuade one of his friends to continue this wrongful work in the hope that the line of 'hack information' of brothers Blanc was still maintained. However, this friend declined the offer and reported the case to the authorities. The Blanc brothers were arrested with the "attack the network", or rather, illegally infiltrating the government's communications system for personal purposes. But then it was released and only had to pay a little fine because the law at that time still had no specific provisions for this crime.
The story of the Blanc brothers, though it happened nearly 200 years ago, is still a reminder of the current nature of any new invention. New technologies, however advanced, advanced, people will always find ways to use them for bad purposes. This can be considered a timeless story because it is related to human nature and not a problem that technology can or should be designed to solve. It can be said that network security is a fiery battlefield in which confrontations still take place every hour and every minute, seemingly not ending.

- Kevin Mitnick shares tips and tricks that hackers often use
You should read it
- ★ Cyber-Attack attacked the US military network
- ★ Keysight's security expert warns against the new cyber attack process
- ★ CMC InfoSec provides malware removal tool for online DDoS attack
- ★ Most cyber attacks focused on these 3 TCP ports only
- ★ Mysterious cyber attack paralyzes the world's largest meat supplier