The more dangerous WannaCry version 2.0 has appeared
There have been predictions that WannaCry (or WannaCrypt) will soon have a variant to get rid of the "kill switch" command based on its domain, and this prediction has come true. Network security researchers have discovered this variant of ransomware or have another kill switch or no command at all.
Starting to attack from Friday afternoon, the ransomware has led many organizations to struggle, including big names like the British National Health Agency, FedEx, Telefonica or the German railway system.
Hidden behind the code is a website that has not been registered and the virus used to infiltrate the computer. If it receives a response, it will retreat, otherwise it will perform an attack. A 22-year-old security analyst is known by the name of Malware Tech blog, which registered the website, thereby activating the virus invasion process.
However, Mr. Costin Raiu from Kaspersky Lab said the new version of the malware does not contain the domain name used to prevent the attack.

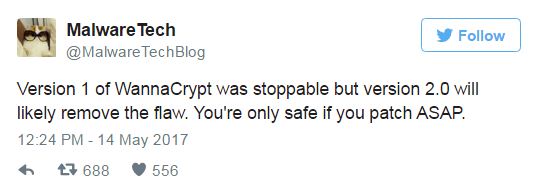
Malware Tech said they only prevented WannaCry 1.0 version. " WannaCry has spread widely and it will have a long-term impact. What we stop is just a variant using the SWB worm." On Twitter, he said " WannaCrypt 1.0 version has been blocked but version 2.0 is not yet. You will only be safe when updating the patch as quickly as possible ." He also said that anyone who cannot patch the computer can disable SMB version 1 (Server Message Block v1).
Since Friday, WannaCry 's attack has affected more than 10,000 organizations and 200,000 individuals in more than 150 countries , including Vietnam. Rob Wainwright, director of Europol, said the attack was " largely unintended " and said it would continue to influence. Microsoft has made a rare decision to release a patch for Windows, authorities warned businesses should update immediately to ensure system safety. He also said Europol is working with the FBI to find out who is behind the attack.
The National Information Security Bureau also immediately launched measures to deal with ransomware, readers should soon take the necessary security steps.
Related articles:
- How to handle the emergency WannaCry malicious code from the National Information Security Department
- How to remove / fix ransomware WannaCry
You should read it
- ★ Network security researcher claims to find a way to decode WannaCry
- ★ The hacker group threatened to spread the network attack tool behind WannaCry
- ★ Warning with 4 dangerous variants of WannaCry malware
- ★ How to handle the emergency WannaCry malicious code from the National Information Security Department
- ★ 2 effective and free ways to check WannaCry