
Microsoft patched a critical vulnerability in Windows
yesterday microsoft patched three vulnerabilities in windows, one of which could be exploited by attacks that trick users into accessing malicious websites.

yesterday microsoft patched three vulnerabilities in windows, one of which could be exploited by attacks that trick users into accessing malicious websites.

in this article, i will show you the vulnerabilities in software architectures that could be vulnerable to dll hijacking, how to detect applications with vulnerabilities and how to

an unpatched vulnerability in windows has been confirmed by microsoft that could be exploited by hackers to take control of the new 'favored' trojan system.
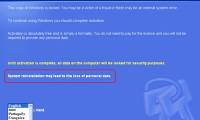
recently, a dangerous program appeared on the computer with the ability to hijack the system and give fake notifications to trick users.

security firm symantec said it found evidence that the stuxnet worm was intended to target uranium enrichment complexes at the bushehr reactor, iran. with the help of experts from

malware or malware can affect mobile devices as well as computers. a little bit of knowledge and proper precautions can protect you from threats like ransomware and sextortion

a series of popular plug-ins for wordpress are found to contain 'backdoor' in the source code, which can help hackers gain access and hijack the blog / website.

a vulnerability can be exploited by bad guys and gain complete control of android phones that install the viber application even though the device is locked.

according to viber, the company quickly released an update to fix lock screen errors on android phones.

according to bkav, hundreds of thousands of computers in vietnam are hijacked due to virus infection.