Analyze DLL hijacking attacks
In this article, I will show you the errors in software architectures that could be hijacked by DLL hijacking, how to detect applications with vulnerabilities, and finally steps. done to ensure this type of attack is avoided .
By the end of August 2010, security researchers had disclosed detailed information about a class of security vulnerabilities that they said had a fairly wide range of influences. They have discovered hundreds of applications that are vulnerable to these attacks and are known as DLL hijacking. In this article we will introduce you to some of the software architecture errors that may be affected by these attacks, in addition to how to detect applications with vulnerabilities and ultimately Steps to be taken to ensure this type of attack is avoided.
How to attack
DLL hijacking can be done because all Windows applications rely on dynamic link libraries (DLLs) as part of their core functionality. DLLs are written by software developers and invoked within their applications to perform various functions. Windows itself is also based on this type of architecture and contains numerous DLLs to perform many different functions.
Hack Internet OS and security - Episode 1
Author: Vu Dinh Cuong (Editor), Phuong Lan (Proofread)
Price: 49,000 VND
Along with DLL files included in the Windows operating system, application developers often write their own DLLs to perform some functions by the program. When finished writing, the DLL files will be packaged and installed with the application. The problem arises in the way applications load these DLLs. By default, when an application does not have a fixed defined path to point to a certain DLL that it requires, the application will perform dynamic search. In the process of performing a search, the application will first search in the directory where it was previously executed, then search the system directory, 16-bit system directory, Windows directory, and directory. Current and then directories listed in the operating system's PATH environment variable. In searching for these paths, the application will use the DLL it finds first.
With these basic knowledge, imagine a scenario where we have executed an application that has to perform a dynamic search of a DLL. The application will immediately search for the path it was executed before and find a matching DLL. However for users, the actual DLL is related to the application located in the Windows system directory. The DLL placed in the directory with the application is the DLL that has been modified by an attacker to remotely access the system. Obviously, the application will not be able to find the actual DLL because it has found the matching DLL that it needs to find.
Identify vulnerable applications
The biggest problem with DLL hijacking attacks is that Microsoft cannot release patches to patch all vulnerable applications. This is because launching such a patch will cause some applications to be disabled. Therefore, fixing the problem will involve both parties. First, companies and software developers who have created vulnerable applications must fix their code and provide updates to users. Next, users (system administrators) must determine whether their networks are using vulnerable applications, find and install patches provided by vendors.
There are several ways to detect whether you are using a vulnerable application. The simplest method is to check public resources posted by security researchers and see if your application exists there. You can search for such resources here.

Figure 1: List of vulnerable applications
The second method requires some extra work because what needs to be done will happen in highly secure environments. You may think this method requires technical knowledge and is only for high-level security professionals. However, not so, HD Moore security expert knew the importance of this attack and developed an auditing kit, which can be used to find applications. There are vulnerabilities in a system.
This kit is called DllHijackAuditKitv2 and is provided here. Once the download is complete, you need to log in as the system administrator, extract the contents of the ZIP archive file and execute the file 01_StartAudit.bat. This script will download Sysinternals Process Monitor and start performing system checks to find vulnerable applications. During the run if download Process Monitor fails, you can download it directly from here. Once downloaded, make sure Process Monitor is in the same directory as the audit scripts. The initial validation script will take a long time to run. Depending on the number of applications on the system, the evaluation may take from 15 minutes to hours.
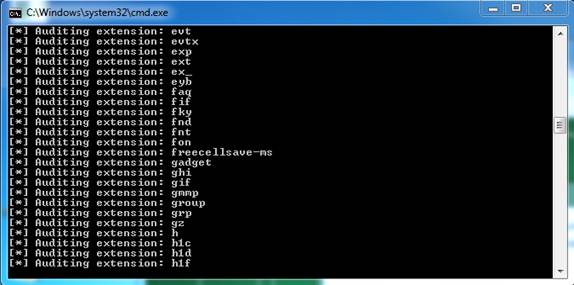
Figure 2: Application authentication test related to file extension
After the audit script completes its execution, you must go through the application to check the process that appeared by the script and save the report it created. Click File and Save to do that. Be sure to save the file in CSV format with the name Logfile.CSV in the audit kit folder.
Next, run the 02_Analyze.bat script. This scenario will analyze the CSV file and find potential vulnerabilities. If any vulnerabilities are discovered, the application will create an exploit code to demonstrate the vulnerability.
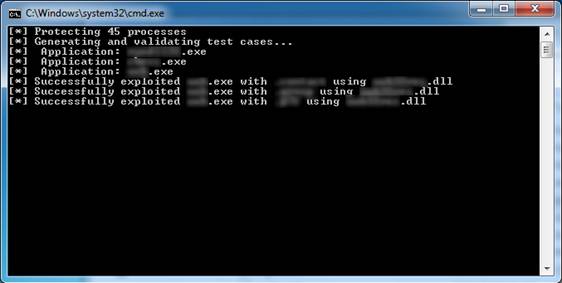
Figure 3: The second scenario tries to exploit potential vulnerabilities that have been discovered
Finally, the left command prompt opened by the script will list the applications that were successfully exploited. With an application that can be exploited, the script will create a subdirectory below the exploit directory. These subdirectories will contain working exploits for affected applications. Operators will do things like launch command shells and backdoor listeners. This is evidence of exploits because they launch calc.exe file.
This information will be very helpful for you to find out if you use vulnerable applications.
Prevent attacks
While waiting for software patches, there are a few things you can do to limit your exposure to DLL hijacking attacks.
Use the CWDIllegalInDllSearch patch
The initial response by Microsoft for this class of vulnerabilities is to change the registry by changing the way of loading DLLs to mitigate attacks. The patch has been implemented very carefully because it can disrupt the functionality of installed applications, but it is recommended to test if you are interested in this type of attack. You can read more about the patch here.
Outbound SMB belt lock
Most organizations have done this, but if you haven't done so, this is a good time to do so. This also helps you avoid some other types of attacks.
Remove installing software with vulnerabilities
This method is not always feasible, but if you are using a vulnerable and easily replaceable application then the work you need to do to ensure security is application switching. .
Deployment of intrusion detection software (IDS)
In some cases, it is not possible to mitigate the attack, it is best to find the attacker in the after exploitation. Using free intrusion detection tools like Snort, you can detect signs of an attack that someone has exploited on a vulnerable computer.
Conclude
The emergence of many DLL hijacking vulnerabilities has created an interesting scenario because in fact we cannot release a patch for the operating system to be able to patch a variety of applications. The best way you can do this is to make sure you know and have knowledge of how this type of attack works, know how to test whether it exists on the applications you are using on your network or not. No, then need to get the right information from those who can issue the patch to fix it.