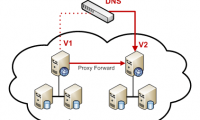
Users of Google search engines may complain about their search being redirected to unwanted pages, no matter which browser you use.

Yesterday (April 12), Microsoft provided a record patch package, up to 64 patches for Windows, Office, Internet Explorer (IE), and other software, including 30 bugs in Windows and

Security risks are increasing in large and small business environments. Here are 10 simple tips that may help you.

ScanPack's word processing system is able to identify documents from specially damaged originals that can easily peel off the print layers of seals, signatures ...

Today (April 15), the world's leading security solutions provider - Symantec has officially announced its strategy to help businesses solve data recovery and system challenges in

Today April 15, 2011, HP Group announced the integration of 3PAR utility storage system into the product portfolio under HP's converged infrastructure solution, the integration to

Cybercrime attacked the information system of state agencies (state agencies) took place. Currently, the Information and Communication Department of the provinces and cities are

On April 21, 2011, IBM held at the IBM 2011 Security Security Symposium in Hanoi. During the conference, IBM mentioned ways to integrate security and security features ...

In the life and work of most of us today requires the use of the Internet, so equipping ourselves with knowledge and security software is essential. Today, we will introduce you

In this series, I will show you some issues in DNS security and how to secure compromised DNS servers.

In the morning of April 23, 2011 in Hanoi, karROX International IT Academy held a meeting with the theme 'White hat hacker - attack & defense'.

If, in the past, the use of Wi-Fi stealing only took up bandwidth to surf the Web, but now with the support of other sophisticated software and eavesdropping methods, bad guys can

On April 25, Trend Micro, the security vendor, launched the latest Vietnamese security version. Worry-Free Business Security 7 has a data loss feature aimed at small and medium

Information about the file 'consolidated.db' on the iPhone records the geographical location and the length of time the user is staying, which worries many people. However, you

These 12 security steps will help you protect your computer, mobile phone or other digital devices safely.

Although USB has become an indispensable thing in anyone's life, these devices also pose a significant challenge to network security.

The hackers' attack on Sony's PlayStation Network (PSN) and Sony Online Entertainment (SOE) has affected a total of over 100 million accounts.

Today, security requirements and requirements, especially for personal data, are becoming more rigorous and demanding. What methods do you usually use to protect the amount of

First of all, to monitor someone's computer means that they can see everything you are doing on your computer at a certain time. It is dangerous if you reveal information about

Viruses, malware, worms, ... are malicious software with your computer. Anyone who has been using a computer knows them or at least has heard about them.
 Users of Google search engines may complain about their search being redirected to unwanted pages, no matter which browser you use.
Users of Google search engines may complain about their search being redirected to unwanted pages, no matter which browser you use. Yesterday (April 12), Microsoft provided a record patch package, up to 64 patches for Windows, Office, Internet Explorer (IE), and other software, including 30 bugs in Windows and
Yesterday (April 12), Microsoft provided a record patch package, up to 64 patches for Windows, Office, Internet Explorer (IE), and other software, including 30 bugs in Windows and Security risks are increasing in large and small business environments. Here are 10 simple tips that may help you.
Security risks are increasing in large and small business environments. Here are 10 simple tips that may help you. ScanPack's word processing system is able to identify documents from specially damaged originals that can easily peel off the print layers of seals, signatures ...
ScanPack's word processing system is able to identify documents from specially damaged originals that can easily peel off the print layers of seals, signatures ... Today (April 15), the world's leading security solutions provider - Symantec has officially announced its strategy to help businesses solve data recovery and system challenges in
Today (April 15), the world's leading security solutions provider - Symantec has officially announced its strategy to help businesses solve data recovery and system challenges in Today April 15, 2011, HP Group announced the integration of 3PAR utility storage system into the product portfolio under HP's converged infrastructure solution, the integration to
Today April 15, 2011, HP Group announced the integration of 3PAR utility storage system into the product portfolio under HP's converged infrastructure solution, the integration to Cybercrime attacked the information system of state agencies (state agencies) took place. Currently, the Information and Communication Department of the provinces and cities are
Cybercrime attacked the information system of state agencies (state agencies) took place. Currently, the Information and Communication Department of the provinces and cities are On April 21, 2011, IBM held at the IBM 2011 Security Security Symposium in Hanoi. During the conference, IBM mentioned ways to integrate security and security features ...
On April 21, 2011, IBM held at the IBM 2011 Security Security Symposium in Hanoi. During the conference, IBM mentioned ways to integrate security and security features ... In the life and work of most of us today requires the use of the Internet, so equipping ourselves with knowledge and security software is essential. Today, we will introduce you
In the life and work of most of us today requires the use of the Internet, so equipping ourselves with knowledge and security software is essential. Today, we will introduce you In this series, I will show you some issues in DNS security and how to secure compromised DNS servers.
In this series, I will show you some issues in DNS security and how to secure compromised DNS servers. In the morning of April 23, 2011 in Hanoi, karROX International IT Academy held a meeting with the theme 'White hat hacker - attack & defense'.
In the morning of April 23, 2011 in Hanoi, karROX International IT Academy held a meeting with the theme 'White hat hacker - attack & defense'. If, in the past, the use of Wi-Fi stealing only took up bandwidth to surf the Web, but now with the support of other sophisticated software and eavesdropping methods, bad guys can
If, in the past, the use of Wi-Fi stealing only took up bandwidth to surf the Web, but now with the support of other sophisticated software and eavesdropping methods, bad guys can On April 25, Trend Micro, the security vendor, launched the latest Vietnamese security version. Worry-Free Business Security 7 has a data loss feature aimed at small and medium
On April 25, Trend Micro, the security vendor, launched the latest Vietnamese security version. Worry-Free Business Security 7 has a data loss feature aimed at small and medium Information about the file 'consolidated.db' on the iPhone records the geographical location and the length of time the user is staying, which worries many people. However, you
Information about the file 'consolidated.db' on the iPhone records the geographical location and the length of time the user is staying, which worries many people. However, you These 12 security steps will help you protect your computer, mobile phone or other digital devices safely.
These 12 security steps will help you protect your computer, mobile phone or other digital devices safely. Although USB has become an indispensable thing in anyone's life, these devices also pose a significant challenge to network security.
Although USB has become an indispensable thing in anyone's life, these devices also pose a significant challenge to network security. The hackers' attack on Sony's PlayStation Network (PSN) and Sony Online Entertainment (SOE) has affected a total of over 100 million accounts.
The hackers' attack on Sony's PlayStation Network (PSN) and Sony Online Entertainment (SOE) has affected a total of over 100 million accounts. Today, security requirements and requirements, especially for personal data, are becoming more rigorous and demanding. What methods do you usually use to protect the amount of
Today, security requirements and requirements, especially for personal data, are becoming more rigorous and demanding. What methods do you usually use to protect the amount of First of all, to monitor someone's computer means that they can see everything you are doing on your computer at a certain time. It is dangerous if you reveal information about
First of all, to monitor someone's computer means that they can see everything you are doing on your computer at a certain time. It is dangerous if you reveal information about Viruses, malware, worms, ... are malicious software with your computer. Anyone who has been using a computer knows them or at least has heard about them.
Viruses, malware, worms, ... are malicious software with your computer. Anyone who has been using a computer knows them or at least has heard about them.