Device security in 12 steps
 Network administration - To find a good security advice is indeed very difficult. As we all know, there are many experts who offer security advice, but not all of their tricks are accurate or timely. So if you follow their advice, you may experience more security holes than you know. That's what we want to introduce in this article. Here are 12 simple but really necessary tips that we gathered. These 12 security steps will help you protect your computer, mobile phone or other digital devices safely.
Network administration - To find a good security advice is indeed very difficult. As we all know, there are many experts who offer security advice, but not all of their tricks are accurate or timely. So if you follow their advice, you may experience more security holes than you know. That's what we want to introduce in this article. Here are 12 simple but really necessary tips that we gathered. These 12 security steps will help you protect your computer, mobile phone or other digital devices safely.
1. Use virtual credit card numbers to buy items online
Surely anyone has a reason to worry about using their credit card number to shop online. Chances are that you know little or nothing about the company that you buy their products, your credit card information will most likely be at risk by data vulnerabilities. In such a case, using a virtual credit card number is one way to ensure your online shopping is safer.
Basically, when using virtual card numbers, the bank providing it will be responsible for your shopping, hackers will never increase access to these credit card information.
Some financial institutions maintain many different types of virtual credit card programs. For example, Bank of America (Bank of America) uses ShopSafe service. Check your bank or credit card issuer for the options you have. Another way is to use the Shield Shop, a service that provides virtual card numbers for any credit card and allows you to check your account.
2. Wi-Fi security
Is your home wireless network protected by a secure password? If not, you need to set it up for an instant password protection. Although you may not care whether your neighbors use your wireless connection to surf the web, it is a lot of risk to open the network, for example, someone with a bad engine can take advantage of your loopholes to increase access to data stored on network computers.
The easiest way to avoid such intrusions is to encrypt the wireless network. Although you will have to enter the password every time you connect to your wireless network, it is just a small price that you have to pay in exchange for security. Most wireless routers support WEP, WPA and WPA2 encryption standards. However, it is better to use WPA or WPA2 encryption settings because these encryption standards will provide a much higher level of security than the WEP standard.
Another method is to set the router to not broadcast the SSID (network name). When SSID broadcast is disabled, your wireless network will be invisibly in front of nearby computers, only those who know your network name will be able to find it. The procedure to do this varies widely, depending on the model and router manufacturer. Please check the router's documentation for more specific instructions.
3. Encrypt the hard drive
Hard drives and USB drives are treasures that store a lot of anyone's personal data. If you lose a USB drive, an external hard drive, or a laptop containing sensitive personal information, you will probably encounter a lot of troubles. However, there is a way to protect you in this case, which is to encrypt the hard drive, by encrypting the hard drive, you will equip yourself with a layer of protection in addition to password protection. system. Encrypting the hard drive will make accessing the file virtually impossible for those who do not know your encryption password.

LaCie's Rugged Safe hard drive features fingerprint reader for internal data security.
Windows 7 and Windows Vista Ultimate and Business operating systems have very useful features called BitLocker, which will allow you to encrypt your entire hard drive. Without the Ultimate and Business versions, you can use another company's software to replace, such as TrueCrypt, this is a free, open-source tool and it is important that it can be encrypted. whole or part of the drive. Mac OS X users can use the included FileVault tool, which encrypts home computers of Mac computers; in which the Lion version allows full disk encryption.
Another option you can choose is to purchase an external hard drive or USB drive equipped with encryption tools. One of these drives can come with fingerprint recognition software to increase security.
4. Updating the software
One of the security precautions is simple but it is important to update the software on your computer. Software manufacturers often release patches as well as feature updates periodically. Meanwhile, cybercriminals often take advantage of known vulnerabilities, but users have not updated in a timely manner or know temporary instructions to prevent vulnerabilities.
Regularly updating computer software can bother you, but installing updates is an important step in protecting your computer safely.
Some new versions of software programs even introduce new features. For example, Adobe Reader X, the latest version of the PDF reader, uses features called Protected Mode to prevent malware attacks. Therefore, if you use the old features of Adobe Reader, you certainly won't get the many advanced security features that the new software has.
On the other hand, most major software upgrade packages have automatic upgrade features when new upgrades are available. You should not ignore the notifications; Please install the upgrade immediately when prompted to do so. Implementation of the upgrade can sometimes cause work interruption but is important in preventing future threats.
5. Upgrade the latest Antivirus software
If you're using an antivirus software two or three years ago, you should upgrade to the latest version available, even if you still get updated malware signature files for the old version. The reason here is that the technology below antivirus software has improved significantly in recent years.
To detect signs, current antivirus products rely not only on traditional sign recognition files. They also use self-discovery techniques to detect and prevent infection since nobody knows.
You can rely on the ranking of antivirus software from famous sites in the world to choose to buy. In case you do not want to lose money, you can choose some free options here .
6. Lock mobile phone
Mobile phones also contain a lot of sensitive personal information such as email addresses, photos, contact lists, Facebook and Twitter applications, etc. Due to a lot of valuable information, mobile phones show up. is the target of the attack on criminals, which is why people are increasingly concerned about the security of these devices.
Applications like Lookout Mobile Security provide basic security tools for mobile phones.
Android phones have encountered a Trojan horse attack or some other type of malware, but security experts say malware is for new mobile devices in the early days. For computer worms, many people don't think their phones are like a computer (they just think it is a mere device), so there are no necessary security precautions like Still used for computers. In case you have not downloaded the security application for your Android phone, this is the time to do so immediately. Be aware that most mobile security applications are available for free so you can easily choose a suitable product for yourself.
If you own a phone like Android, the first thing you need to do is install an antivirus program. In addition to scanning malware for the computer, these antivirus applications also support many other useful features such as allowing remote data deletion (using this feature you can delete all data stored on the phone when being lost device), GPS positioning, .
There are many popular applications in this category, one of which we can recommend here is Lookout Mobile Security. Lookout can scan the entire phone to find malware as well as automatically scan newly installed applications. Other relatively popular antivirus applications are provided free of charge such as Norton Mobile Security (beta version) of Symantec, Antivirus Pro of AVG and WaveSecure of McAfee.
Apple's App Store repository has been very well controlled for applications so iPhone users generally don't have to worry about malware. However, any application can be cracked and that is the problem you need to care about. Apple does not allow any antivirus applications in the App Store, but actively has some security options that are still the best.
The first is Apple's famous remote device data deletion and deletion service called Find My iPhone. This is part of Apple's MobileMe service ($ 99 per year), but Apple offers it free for iPhone, iPad or iPod Touch applications. With Find My iPhone, you can lock and delete data stored on iPhone remotely, track device by GPS, set remote password, display notification on screen with a warning sound ( so you can find it if you lose it somewhere in your home or office.)
Another tip: When choosing a mobile antivirus program, the safest thing is to choose old-name firms or you will encounter unnecessary risks as we often get with antivirus applications.
7. Install Plug-In Link-Checker
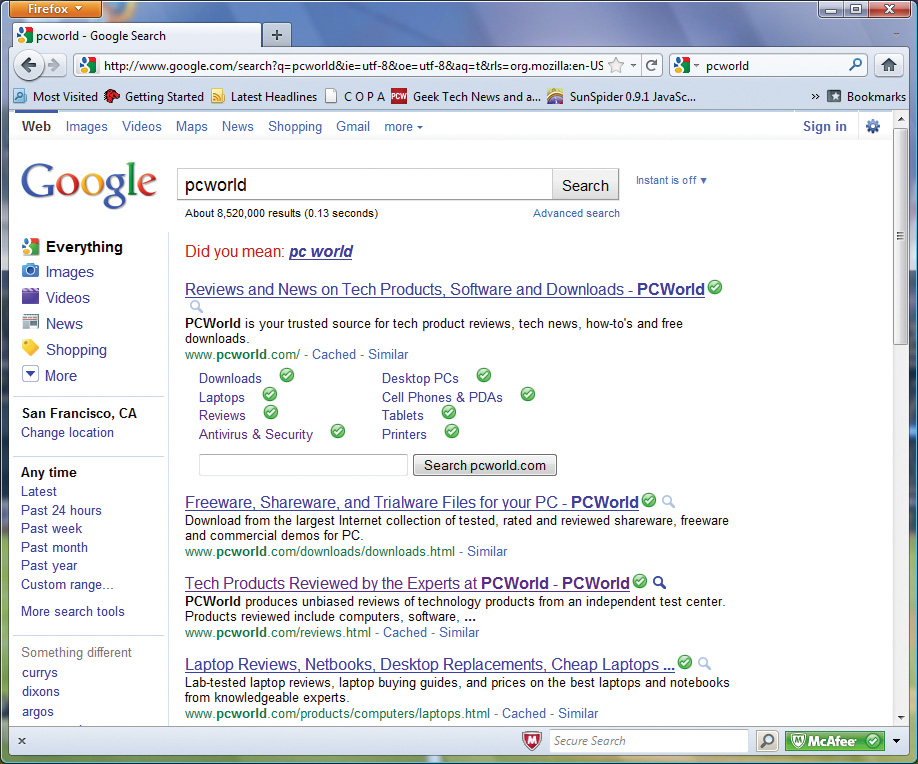
McAfee SiteAdvisor has a green icon (safety level), yellow (unclear) and red (unsafe level) for each page listed in the browser's search results.
Security threats often hide in seemingly harmless websites. Many mainstream sites can also be hacked, criminals in this field often do some operations to make sure that the sites that are infected with their malicious components can get into the top of the search results page. Search (this technique is known as 'search engine poisoning') and secure sites can be the home of malware of this type. Although there is no way to protect against such attacks, using a link checker can help you protect yourself a lot.
The Link-checker tool will display small signs next to the links in the search results page and tell you if a site is trustworthy, dangerous or suspicious. Many such tools also add status indicators to the browser bar to let you know if there are any problems with the site you are currently accessing.
8. Use security lock
 Using a security lock is a very simple way to do it, but it can help you avoid losing your laptop.
Using a security lock is a very simple way to do it, but it can help you avoid losing your laptop. It is very easy to lose a laptop if it is not physically protected because it only takes a very short time, the thief can sneak in and steal your laptop. Then the thief can use the laptop and access files and personal information in the laptop. A notebook lock will not be able to prevent a thief from using dedicated devices to cut the cable, but more or less it also makes the theft process take longer.
Kensington is a well-known name for producing locks for laptops and desktops. There are also other names such as Targus, which makes anti-theft locks for laptops as well as locks that can sound a warning when someone steals your computer or cuts the cable.
 A simple laptop lock that is very effective in avoiding theft.
A simple laptop lock that is very effective in avoiding theft. The nosy eyes are the general security risks. To avoid viewing data theft when leaving the desk, always lock the screen before leaving the computer. To do so, simply press and hold the Windows key and type in the letter L. This will bring up your login screen. To return to the working window, simply press Ctrl-Alt-Delete and enter the login password.
Another way to cover the screen is to set up the screen cover. This program will cover the screen directly so that the person behind can not peek over your shoulder and see what is on the screen. Screen coverers can be a useful way if you work in an 'open' office, with no shielding walls. Companies that provide such filters include: Targus, 3M and Fellowes.
9. Use HTTPS encryption
When browsing the web, protect yourself by using HTTPS (Hypertext Transfer Protocol Secure) whenever possible. HTTPS will encrypt the connection between the computer and the website you are visiting. However, HTTPS cannot guarantee that a website is secure, it only helps prevent some hacking components from accessing the network and increasing access to your account.
Many default sites use HTTPS: For example, when you buy something online or log in to an online account, the browser will connect to these sites via HTTPS automatically. However, you can also protect yourself one step ahead by using HTTPS for social networking sites like Facebook, Twitter or Gmail.
To use the HTTPS feature of Facebook, log into Facebook and click Account in the upper right corner of the screen. Select Account Settings from the drop-down menu and find the 'Account Security' component in the page that appears later. Under Account Security, click Change , check the box next to Browse Facebook on a secure connection (https) whenever possible , then click Save .
You can easily enable HTTPS on sites like Twitter and Facebook and on services like Gmail to create an extra layer of protection.
With Twitter, first log into your account. If you are using the new Twitter interface, click on the account name at the top right of the screen, select settings . (If you still use the old interface, click the Settings link in the upper right corner of the window). From here, look in the lower part of the results page, check the box next to Always use HTTPS and click Save .
To enable HTTPS on Gmail, log in to your account, click the tool icon in the upper right corner, select Mail Settings from the drop-down menu. Next, under Browser Connection, select the button labeled Always use https . Once all is done, navigate to the lower part of the page and click Save Changes . You can visit here to learn more about Gmail security.
10. Avoid public computers and Wi-Fi
Free Wi-Fi hotspots or public computers can be very handy, but they are also places to reveal your personal information. The reason is that the public computer can be infected with spyware or other types of malware designed to track your online actions and thereby collect the password you entered.
Similar to open Wi-Fi networks. Attackers here can set up fraudulent Wi-Fi networks that look like valid Wi-Fi networks (for example, they can name the network like the name of the cafe you're sit there) but activate spy programs to collect personal information. Even valid Wi-Fi networks can have many holes.
Indeed sometimes we may have no choice but to use a public computer or a public Wi-Fi network. However, when using, you should not check email or social networking accounts, bank accounts or perform other actions that require you to log into a site. If you have a VPN, use it to ensure your data security.
11. Set a smart password
We all know that using a password that's easy to detect or too simple, such as "password" or someone's name in your home is a bad idea. However, how does your password become more secure?
1Password program, priced at $ 40, allows you to create secure passwords and manage them for you.
First you need to create a password of a certain length for each account. Hackers often break into accounts using the 'dictionary' attack, which is basically the way to use words in the dictionary to guess a password. To avoid that, you should not use the words 'standard' as a password but instead create a password that is composed of characters, numbers and symbols. Do not simply replace the word character with a symbol (for example, using the @ symbol instead of A). You can also increase the security of your passwords by using both uppercase and lowercase characters.
Basically, the more complex the password, the better. However, you also need to create a password so you can remember to prevent you from locking yourself out of your account.
It is very difficult to remember multiple passwords at the same time, which is why people often want a password manager to help them do this. KeePass is a product you can consult, a free password management option that can work on Windows and Mac OS X systems. Another option is 1Password ($ 40), which also allows creation and administration. Manage passwords to help you.
12. Check annual credit reports
Obviously you can do everything right but the attacker can still succeed in stealing your identity. The problem is, you can control access to your personal information, but it is impossible to control how a certain company you work with will secure your records. How is their personal data.
In this case, you can limit your risk by checking your credit reports on a regular basis. Regular checking of credit reports is a great way to ensure that no one opens a credit card or bank account with your name.