
How to Become a Hacker
in computer security, a hacker is someone who focuses on security mechanisms of computer and network systems. there are communities and shared cultures of expert programmers and

in computer security, a hacker is someone who focuses on security mechanisms of computer and network systems. there are communities and shared cultures of expert programmers and

i recently introduced you to a remote connection to windows 7 desktop from a linux computer, and in this article we will show you how to do the opposite.

today, networks increasingly contain many different types of computers (including many types of hardware, software and operating systems) that are no longer new.
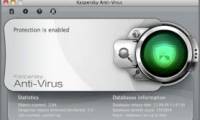
kaspersky has just released a version of the antivirus software of the same name for apple's mac os x operating system.

sun microsystems solaris 10 os is being attacked by a new worm called 'turkey' from the end of last month thanks to taking advantage of the flaw in this operating system. the new

many of you newbie have asked me 'what is a hack? how to hack? ' but you have forgotten that you need to have a general knowledge, understand the terms that people who are

grub (grand unified bootloader) is a bootloader that allows users to install multiple distributions on the system and select one when the system starts up.

most of the current operating systems can be grouped into two different branches. besides operating systems based on microsoft windows nt, nearly every other operating system is a

if using a unix or unix-style operating system, we need to understand the most basic file-level security management methods.

the most important point of the file-level security process on unix systems is to limit the file access license as much as possible.