The most basic insights to becoming a Hacker - Part 1
Many of you Newbie have asked me 'What is a hack? How to hack? ' But you have forgotten that you need to have a general knowledge, understand the terms that people who are familiar with the web or use. Personally, I have not been very good, but through research, I have also synthesized some basic knowledge, want to share it with all of you, to study with you.
I will not be responsible if you use it to disrupt others. You can copy or post on other websites but please fill in the author below the post, respecting this article is also respect for me and my effort, and also respect yourself. I also have some basic hacking, cracking and basic examples here, so you can try it and study it to understand it, then when you see a word that you don't understand, read it. To know, I have used some of the ideas in this article that I find very interesting from the HVA Web site and other Web sites I have visited. Thanks to the authors who wrote those articles. Now is the main problem.
1. What we need to start is Hacker
Maybe many of you disagree with me, but the best way to practice is to use the Windows operating system and then the more powerful ones are Linux or Unix, below are the ones you need:
- An OS
- A good Web site
- A good network browser
- A good chat tool
- Telnet
- The most important thing anyone wants to be a hacker is to have a bit of programming knowledge ( C, C ++, Visual Basic, Pert . )
2. What is an IP address?
The IP address is divided into 4 numbers limited from 0 - 255 . Each number is stored by 1 byte, so IP is 4 bytes in size, divided into address classes.
There are 3 classes A, B and C. If in Class A, we will be able to have 16 million addresses, in Class B there are 65536 addresses. For example : In class B with 132.25 , we have all addresses from 132.25.0.0 to 132.25.255.255 . The majority of A class addresses are owned by companies or organizations.
An ISP usually has several class B or C addresses. For example: If your IP address is 132.25.23.24 , you can determine who your ISP is.

IP is an acronym for Internet Protocol , on the Internet, each person's IP address is unique and it represents the person themselves, the IP address used by different computers to identify connected computers. between them. This is why you are banned by IRC and the way people find your IP.
IP addresses can be easily detected, people can get through the following ways:
- When you browse a web page, your IP is recorded
- On IRC, anyone can have your IP
- On ICQ, people can know your IP, even if you choose Do not show ip, people still get it
- If you connect with someone, they can type systat -n and know who is connecting to them
- If someone sends you an email with an IP-encoded java code, they can also catch your IP
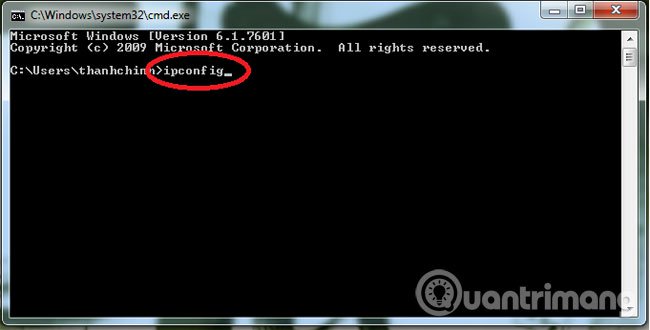
3. How do I know my IP address?
- In Windows : go to cmd , type ipconfig
- In mIRC : connect to the server then type the command / dns
- Through some Web sites with IP display
4. What is IP Spoofing?
Some IPs are intended to identify a single device in the world. So on a network a server can allow another device to exchange data back and forth without checking the server.
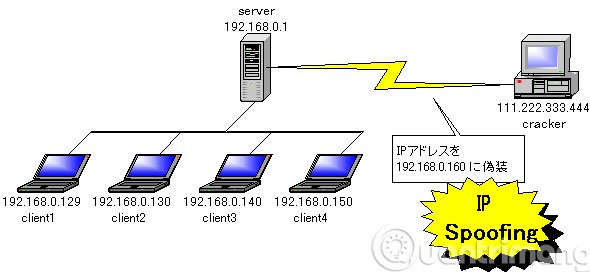
However, it is possible to change your IP, which means you can send a fake information to another computer that will believe that the information received comes from a certain machine (of course not yours). ). You can pass the server without having to control the server. The drawback is that the feedback from the server will be sent to the IP-enabled device that we forged. So you probably won't get the feedback you want. Perhaps the only thing that spoof IPs is effective is when you need to pass a firewall, steal your account and need to hide your personal information.
5. What are Trojans, worms, viruses, logicbomb?
- Trojan : It is easy to understand, this is a spy program installed on someone else's computer to steal the documents on the computer and send it to its owner. What it steals can be a password, an accourt or a cookie . depending on who wants it installed.
- Virus : It is easy to understand that this is a program with special codes installed ( or spread from another device ) on the victim's machine and performing the requirements of that code, most viruses are used to destroy data or computer.
- Worm : This is a standalone program that can replicate itself and spread throughout the network. Just like a virus, it can also damage data or it can destroy inside the network, even cracking that network.
- Logicbomb : A program that sends a lot of data packets to the same address at the same time, flooding the system, blocking traffic lines (on the server) or using it as a tool to ' terrorize ' the enemy.

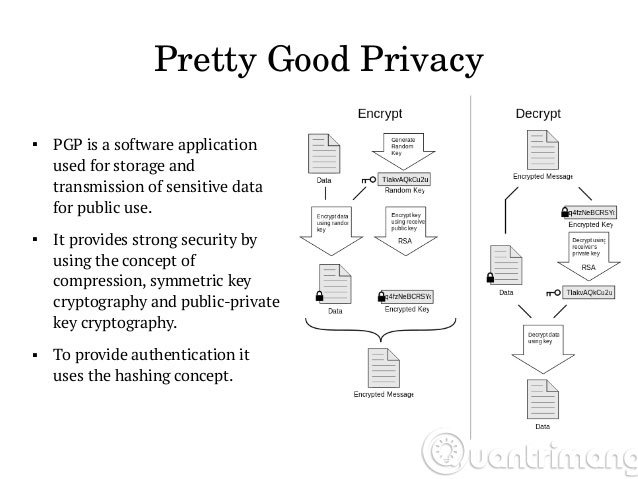
6. What is PGP?
PGP stands for ' Pretty Good Privacy ', which is a tool that uses public key encryption to protect email and data records, which is a highly secure form of encryption using MS_DOS, Unix, VAX / VMS and others.
7. What is a proxy?
Proxy, Proxy Server or Proxy Server (also 1), we can understand that another computer has the task of processing data, like an information converter of Internet signals. By connecting via one or more of the above servers, initially the user's computer - you will send request-request signals through the proxy server, where that information will be processed and returned. What you see every time you access the Internet.
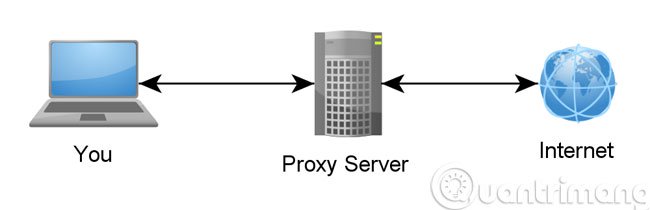
Under this interpretation, the proxy acts as an intermediary between the computer you are using and the entire external Internet environment. Besides, Proxy is also used to filter, block websites, or more accurately, website content according to the needs of the government, service providers .
Read on to find out more about what Proxy is!
8. What is Unix?
Unix is an operating system (like Windows). It is currently a strong and intimate operating system with the most Hacker. If you have become a true hacker, this OS is indispensable for you. It is used for support for C language programming.

9. What is Telnet?
Telnet is a program that allows you to connect to another computer via a port. All computers or servers (servers) have ports, here are some common ports:
- Port 21: FTP
- Port 23: Telnet
- Port 25: SMTP (Mail)
- Port 37: Time
- Port 43: Whois
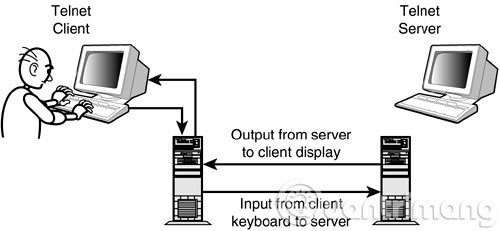
For example: You can call Telnet to connect to mail.virgin.net on port 25.
10. How do I know if I have Telnet to Unix system?
First, when you call Unix, it will usually have a prompt: 'Log in:' , (however, only with this is not sure if it is Unix except that it appears in the previous message. 'log in:' as an example: Welcome to SHUnix. Please log in .).
Now that we are at the ' log in ' prompt, you need to enter a valid account. A normal account consists of 8 or more features, after you enter your account, you will see a password, try to enter Default Password and try the following table:
Account / Default Password
Root / Root
Sys / Sys / System / Bin
Bin / Sys / Bin
Mountfsy / Mountfsys
NuucAnon
Anon / Anon
User / User
Games / Games
InstallInstall
DemoDemo
GuestGuest
- How to retrieve a hacked Facebook account
- Why is Facebook account hacked?
- Instructions to "hack" into Administrator account on Windows 7
The most basic insights to becoming a Hacker - Part 2
Having fun!