
5 types of data theft you should know to prevent
the truth is that data security is a complex and difficult issue. if you think your data is completely safe, there may be holes that you don't know. that is why it is important

the truth is that data security is a complex and difficult issue. if you think your data is completely safe, there may be holes that you don't know. that is why it is important

in technology terms, man-in-the-middle (mitm) is an attack that is intercepted by a third party (hackers) during communication between the server and the user. instead of the data

one advice is to be cautious when browsing the web. never let your curiosity be the cause of unworthy errors. on your browser, block and remove all tracking cookies. especially

dropbox storage service 'cloud' dropbox began adding two-layer security functionality to enhance the protection of the previous user account of the current wave of data theft.
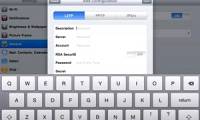
ipad devices also support ssl vpns, using the same ssl protocol that websites use whenever they want to secure the connection so you can send important data to them without having

recently, the famous security research organization of the united states, cert has discovered a series of devices with integrated bluetooth connectivity today (including iphone, a

reddrop is one of the most sophisticated android malware that researchers have ever seen spread widely.

hackers often try to hack into google accounts, so google researchers have spent a year to see how they can steal user accounts.