Modular Malware - New stealth attack method to steal data
Malware - malware - attacks in various forms and sizes. In addition, the sophistication of malware has grown significantly over the years. Attackers realize that trying to get a whole package of malware into the system once is not always the most effective way.
Over time, malware has become modules. Some malware variants can use different modules to change the way they affect the target system. So what is modular malware and how does it work? Let's find out through the following article!
Modular Malware - New stealth attack method to steal data
- What is Modular malware?
- Examples of malware modules
- VPNFilter
- T9000
- DanaBot
- Marap, AdvisorsBot and CobInt
- Mayhem
- DiamondFox
- How to prevent a Modular Malware attack
What is Modular malware?
Modular malware (malware module / malware module) is a dangerous threat, attacking the system at different stages. Instead of direct attacks, malware modules have a secondary approach.
It does that by only installing the first essential components. Then, instead of creating fanfare and warning users about its presence, the first module is geared towards network and network security; the main responsible parts, what kind of protection methods are being used, where malware can find vulnerabilities, what exploits have the highest chance of success, etc.
After successful detection of the local environment, the first stage malware module can contact its command and control server (C2). C2 can then respond by submitting additional instructions with additional malware modules to take advantage of the specific environment in which the malware is operating.
The malware module is more useful than malicious software that gathers all functions into a single payload, specifically:
- Malware creators can quickly change the identity of malware to avoid other antivirus and security programs.
- The malware module allows for extended functions for many different environments. In particular, malware creators can react to specific goals, or mark specific modules for use in specific environments.
- The modules were initially very small and easily changed.
- Combining multiple malware modules helps security researchers guess what will happen next.
Malware modules are not new threats. Malware developers have effectively used malware module programs for a long time. The difference is that security researchers are encountering more malware modules in many different situations. Researchers have also discovered the giant Necurs botnet (notorious for distributing ransomware variants of Dridex and Locky) that spread malware modules.
Example of malware module
There are some interesting examples of malware modules. Here are a few of them.
VPNFilter
VPNFilter is a recent malware version that attacks router and Internet of Things (IoT) devices. This malware works in three phases.
The first phase malware communicates with an ordered server and controls to download the second phase module. The second stage module collects data, executes commands and can interfere with device management (including the ability to "freeze" routers, IoT devices or NAS). The second stage can also download the third stage module, which acts as the plugin for the second stage. The three-stage module includes a SCADA traffic detection package, an infectious module and a module that allows phase 2 malware to communicate using the Tor network.
You can learn more about VPNFilter in the following article: How to detect VPNFilter malware before it destroys the router.
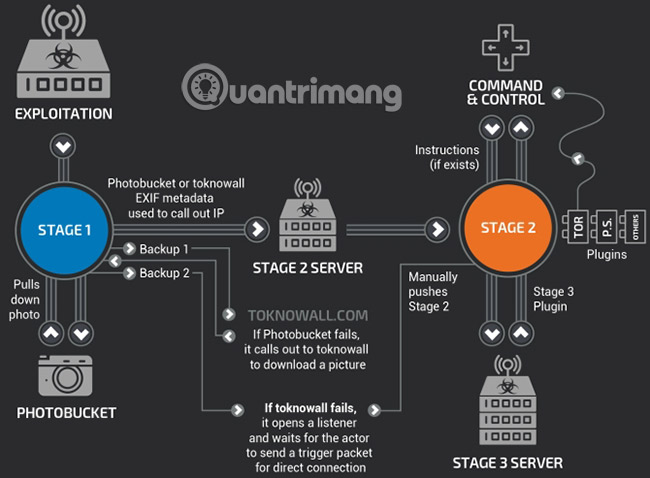
T9000
Palo Alto Networks security researchers have discovered malware T9000 (not related to the Terminator or Skynet).
T9000 is a data collection tool and data. After installation, the T9000 allows an attacker to "capture encrypted data, take screenshots of specific applications and specifically target Skype users" as well as Microsoft Office product files. The T9000 comes with various modules designed to avoid 24 different security products, changing its installation process to be undetected.
DanaBot
DanaBot is a multi-stage bank Trojan with various plugins that attackers use to extend its functionality. For example, in May 2018, DanaBot was discovered in a series of attacks on Australian banks. At that time, researchers discovered a package of infection detection plugins, a VNC remote plugin, a data collection plugin and a Tor plugin that allows secure communication.
"DanaBot is a bank Trojan, which means it must necessarily be geographically targeted at some point," says Proofpoint DanaBot. 'Although there are many preventive measures applied as we have seen in the US campaign, it is easy to see the positive, expanding geography and sophistication of malicious software. Harm is increasing. The malware itself contains a number of anti-analysis features, as well as regularly updated information and remote control modules, adding to its threat to targets. '
Marap, AdvisorsBot and CobInt
The article is incorporating three malware module variants into one because of the great security researchers at Proofpoint who discovered all three types at the same time. These malware variants are similar but have different uses. Moreover, CobInt is part of the Cobalt Group campaign, a criminal organization that is associated with a long list of cybercrime in the banking and financial sector.
Marap and AdvisorsBot are designed to aim at the entire target system for network defense and mapping, then determine whether the malware should download the entire payload. If the target system meets the needs (for example, valuable), the malware will continue the second phase of the attack.
Like other malware module versions, Marap, AdvisorsBot and CobInt follow the three-step process. The first stage is usually an email with an attachment infected with malware for the purpose of initial exploitation. If the extraction task is done, the malware immediately requests the second phase. The second stage carries a reconnaissance module to assess the network security and landscape measures of the target system. If the malware says everything is appropriate, the final stage will download the third module, including the main payload.
Mayhem
Mayhem is a slightly older version of malware module. It first appeared in 2014. However, Mayhem is still an excellent example of malware module. Malware, discovered by security researchers at Yandex, targets Linux and Unix web servers. It installs via a malicious PHP script.
After installation, the script can call some plugins that determine the optimal use of malware.
Plugins include a brute force password cracking program that targets FTP, WordPress and Joomla accounts, a web crawler to search for other vulnerable servers and a Heartbleed vulnerability extraction tool. OpenSLL.
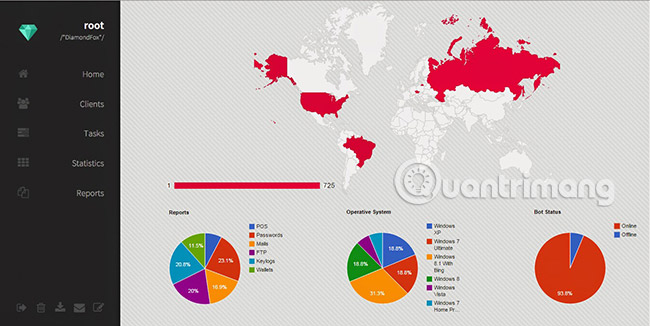
DiamondFox
The last module of the malware module in today's article is also one of the most complete versions. This is also one of the most worrisome things, for several reasons.
The first reason, DiamondFox is a semi-modular botnet on various underground forums. Potential cybercriminals can purchase DiamondFox modular botnet packages to access a range of advanced attack capabilities. This tool is updated regularly and, like all other online services, has individual customer support. (It even has a change log!)
The second reason, DiamondFox botnet module comes with a variety of plugins. These features are turned on and off via the dashboard, suitable for a smart home application. Plugins include appropriate spy tools, authentication information stealing tools, DDoS tools, keyloggers, spam mail, and even a RAM scanner.
How to prevent a Modular Malware attack?
At the moment, there are no specific tools that can protect users against a malware module variant. In addition, some malware module variants have limited geographical scope. For example, Marap, AdvisorsBot and CobInt are mainly found in Russia and CIS countries.
Proofpoint researchers have shown that despite the current geographical limitations, if other criminals see an established criminal organization using malware modules, they will definitely follow. .
Awareness about how malware modules reach your system is very important. The majority of cases have been reported to use malware-infected email attachments, often containing Microsoft Office documents with malicious VBA scripts. Attackers use this method because it's easy to send malware-infected emails to millions of potential targets. Moreover, the initial exploit is very small and easily disguised as a normal Office file.
As always, make sure you keep your system up to date and consider investing in a quality antivirus software. That is worth it!
See more:
- How many types of malware do you know and how to prevent them?
- Differentiate types of malware
- Risks from malware and how to prevent it