Learn about Pumas extortion software
This article will provide you with basic information about Pumas malware, as well as ways to help you completely remove this malware.Please follow the ransomware removal instructions mentioned at the end of the article.
Pumas is the name of a virus created for the purpose of encrypting your files, after being encrypted, the files will be appended with the .pumas extension at the back.Specifically, your files will be locked with both military-grade encryption algorithms, AES and RSA 1024 bits.Pumas malicious code will encrypt your data and after it is completed, it will require you to pay to restore those files.This is a form of extortion code that has been very popular in recent years.
- 5 popular encryption algorithms you should know
Pumas extortion software
- Basic information about Pumas malicious code
- Spreading method of Pumas spyware
- Details about spyware Pumas
- File encryption process of Pumas malicious code
- How to remove Pumas Ransomware virus and Restore .pumas files
Basic information about Pumas malicious code
Name
.pumas Files Virus
Species
Spyware, extortion software, Ransomware, Cryptovirus.
General description
This extortion software will encrypt files on your computer and require a ransom to recover encrypted files.
Symptom
This extortion software will encrypt your files with the help of two encryption algorithms, AES and RSA.All files after being encrypted will have the .pumas extension added to the file extension.
Method of spread
Spam emails, attachments in email.
Detection tool
Security software is paid for.
Spreading method of Pumas spyware
This Pumas spyware can spread in many different ways through the Internet, but mostly through email tools.When you accidentally execute files containing Pumas spyware, your computer system will be completely infected.
In addition, Pumas malicious codes can also be distributed on social media (social networks) and various file sharing services.The free software found on unorthodox websites is also a useful tool to spread malicious codes, including Pumas.In case after you download a file, don't open the file right away.First, you should scan them with a security tool, and check their size and signature to see if something is wrong.Please refer to the article 'How to identify computers infected with viruses with 10 specific signs' to get the information needed for this situation.
Details about spyware Pumas
As mentioned, Pumas is a file encryption virus and will display a window along with instructions on how to transfer money to hackers on your computer screen.In short, blackmailers want you to pay a ransom for recovering encrypted files.
More dangerous, Pumas malware can create entries in the Windows Registry to "parasitize" longer and more robustly in the system, as well as being able to boot or contain various processes in the Windows environment. .
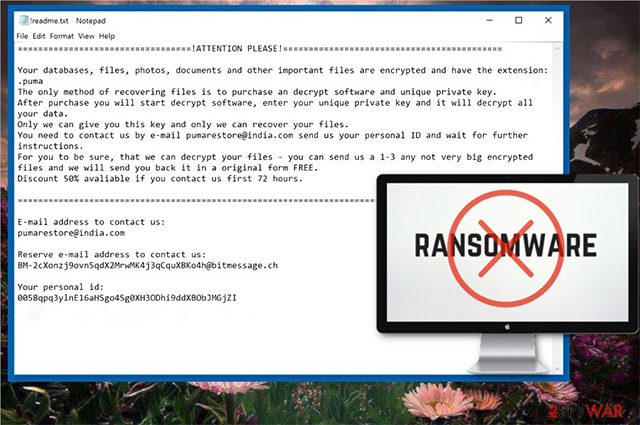
After encryption, the Pumas virus files will place a ransom notification inside a file called "! Readme.txt".You can view the content of the ransom notice from the screenshot given below:
Specifically the content of this notice is as follows:
Your database, files, photos, documents, and other important files have been encrypted and have an extension: .pumas. The only way to recover files is to buy decoding software and unique private keys.
After purchasing decoding software and private keys, you can decode the software yourself, enter the unique private key you just purchased and it will help decrypt all your data.
Only we can provide you with this key and only we can recover your files.
If necessary, you can contact us via pumarestore@india.com e-mail , please send us your personal ID and wait for further instructions.
If you still don't believe we can decrypt your files, you can send us 1 to 3 encrypted files (the size isn't too big) and we'll send it back to You have the files as intact as the original, completely FREE.
50% discount if you contact us within 72 hours after your file is encrypted.
Email address for you to contact us:
pumarestore@india.com
The second email address for you to contact us:
BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch
Your personal id:
0082h9uE76AxDjXNxBHGyUH4cnmWz8r5WOrN4VGu9eJ
As you can see, the email addresses of those blackmailers are:
BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch
pumarestore@india.com
In summary, the Pumas spy software notes that your files have been encrypted.You are required to pay a ransom to recover your files.In fact, most of the general psychology of people in this case is bewildered and willing to pay ransom, especially when the encrypted files contain important data.However, no matter how bad the situation is, remember that you should NOT pay any ransom.What do you get to make sure your files will be restored after paying the ransom, while the nature of those who cause these situations are professional scammers!Moreover, giving money to cybercriminals will only help facilitate them to create more malicious software or continue to commit other criminal acts.
File encryption process of Pumas malicious code
Until now, what we know about the encryption process of Pumas ransomware software is that every file after being successfully encrypted will have a .pumas extension.
Encryption algorithms are used to lock files that are AES and RSA 1024 bits.
Below is a list of the types of files that Pumas tends to use, the list will be updated as new reports are available on this issue:
- Audio file
- Video file
- Document file
- Image file
- Backup file
- File contains login information, banking, finance .
Pumas cryptovirus can be set up to delete all Volume Shadow copies from the Windows operating system with the help of the following command:
→ vssadmin.exe delete the shadows / all / Quiet
In case the above command is executed, the encryption process will be performed more efficiently.It is due to the fact that this command will remove your data recovery methods.If your computer device is infected with this extortion software and your files are locked, read the following section to find out how you can restore your files back to normal.
How to remove Pumas Ransomware virus and Restore .pumas files
If your computer is accidentally infected with the Pumas extortion virus, you should have some experience in removing malware.In short, you should remove this software as quickly as possible before it can have a chance to grow stronger and infect other computers.
Please refer to the article "Removing root malware (malware) on a Windows 10 computer" for specific instructions.
The above is the information you need to know about Pumas spyware.Wish you build a strong security system for yourself!
see more
- The shortcut virus removal has never been this simple
- How to use Trend Micro RansomBuster blocks ransomware
- How do I know if a file is mistakenly identified as containing malicious code?
- Why is the security tool only quarantined rather than deleting infected content?
- With the NMR's 15 free Ransomware decoding tools, you won't need to ransom the file anymore
You should read it
- How to delete malicious programs using Kaspersky Virus Removal Tool
- Theory - What is Ransomware?
- What to do to handle 'No Internet After Malware Removal' error?
- Top 5 best Malware removal software 2020
- Is it better to clean, isolate or delete viruses in malicious files?
- Download the malware removal tool and clean up Malware Hunter PRO computer for $ 49.95 for free
- Instructions to remove Malware on the computer
- 5 types of malware on Android
- 10 typical malware types
- The steps to clean up the virus 'Activate this edition of Windows' attack your Windows computer
- How to fix Facebook catch virus scan, tell the computer to be infected with malware
- Ako ransomware is raging all over the world, what do you know about this ransomware?
Maybe you are interested
Instructions to change Messenger color on phone, computer How to download the wallpaper of App Store on iPhone How to turn off Twitter Direct Message notifications on iPhone, Android, PC 10 important sayings should tell the opponent every day This is only 8 hotels with the world's most impressive on-site ice rink Water can 'cut sweet' concrete and steel. Do you believe that?
