How to use theHarvester to map your online footprint in just minutes
Your digital footprint is often larger than you think. It includes every email you've sent, every subdomain you've created, every service you've logged into, not to mention the alarming amount of information Google knows about you. In many cases, this data is visible, and mapping it out takes just minutes. Some data collection tools are public, revealing exactly what anyone can see about you online. This is called Open Source Intelligence (OSINT). The problem is, if you can do it, anyone can.
Setting up theHarvester
Install, configure, and get ready to explore your footprint
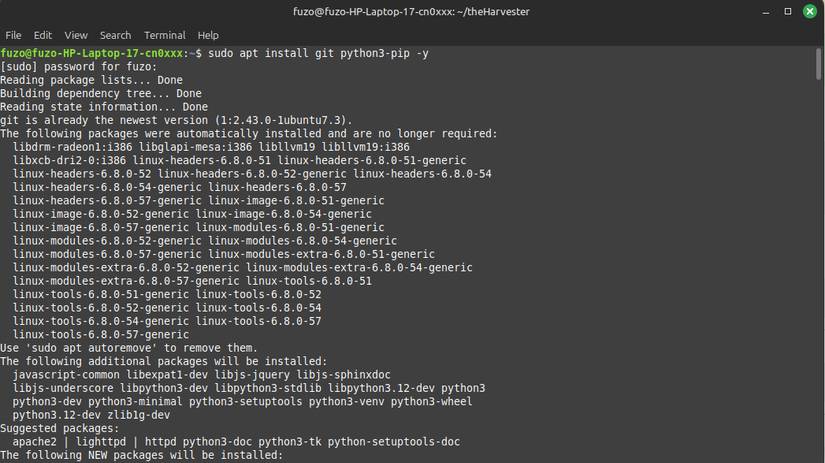
While theHarvester may sound like a dedicated cybersecurity tool (it comes pre-installed on the penetration testing-focused distribution Kali Linux ), installing it on Linux Mint is pretty straightforward. Just clone theHarvester from the GitHub repository to ensure you have the latest version with all the current APIs and modules.
1. Launch terminal and run the commands below:
sudo apt install git python3-venv -y git clone https://github.com/laramies/theHarvester.git cd theHarvester python3 -m venv venv source venv/bin/activate pip install .2. Once the installation is complete, run the command below to confirm that it worked:
theHarvester -hYou should see theHarvester menu confirming that it was installed correctly.
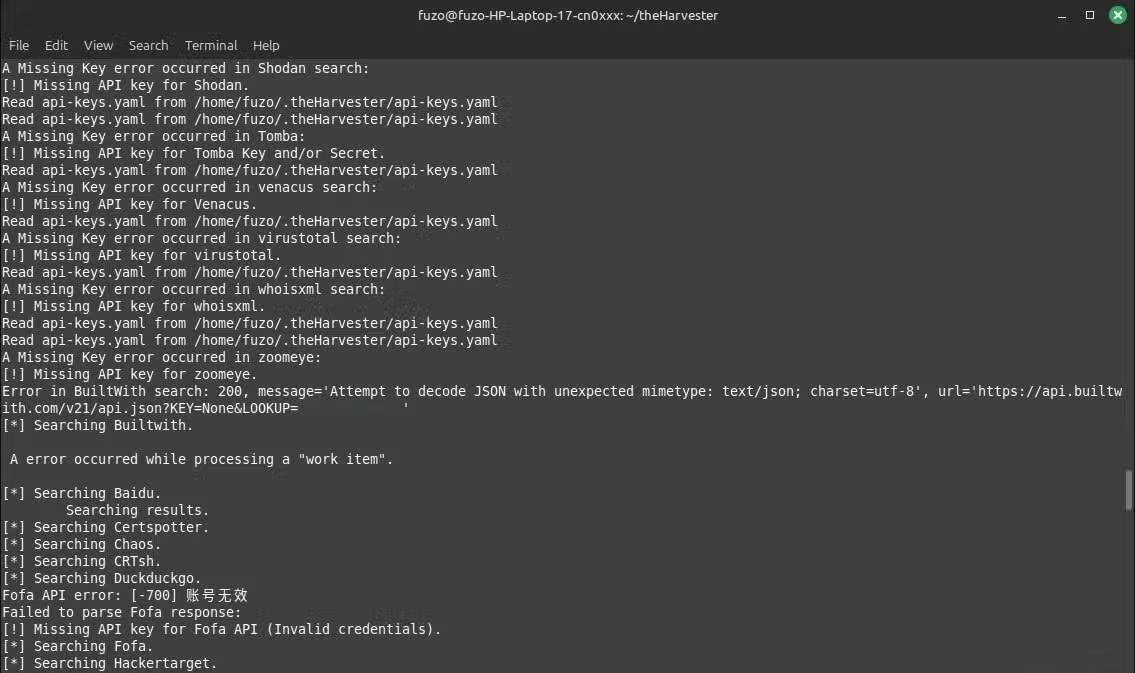
theHarvester crawls public information using DuckDuckGo, CRT.sh, CertSpotter, DNSDumpster, VirusTotal, and other certificate and threat feeds. You can integrate free API keys for Shodan or Hunter.io by adding them directly to theHarvester's api-keys.yaml file . This will improve results, although the tool still works very well without upgrading.
Run the first scan
Mapping What the Internet Knows About You
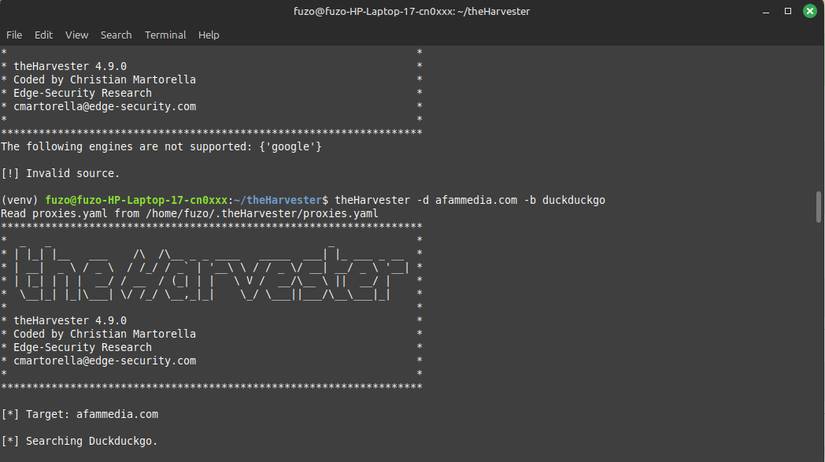
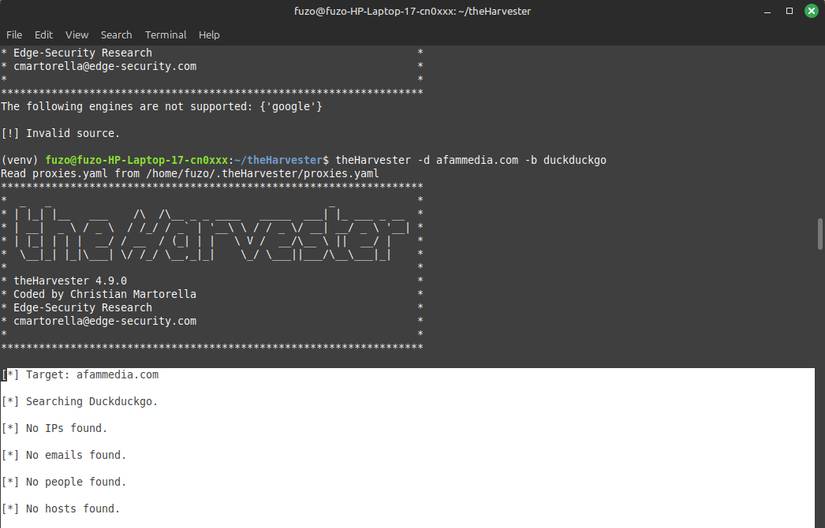
Now that you're set up, it's time to explore what your online footprint looks like. To get started, launch a terminal in theHarvester directory and run the command below, replacing example.com with your test or actual domain.
theHarvester.py -d example.com -b all -l 100You can also run the command below from a common terminal to launch theHarvester.
Using the -b all flag in the above command allows Harvester to search through all available data sources, and -l 100 will limit the results for readability.
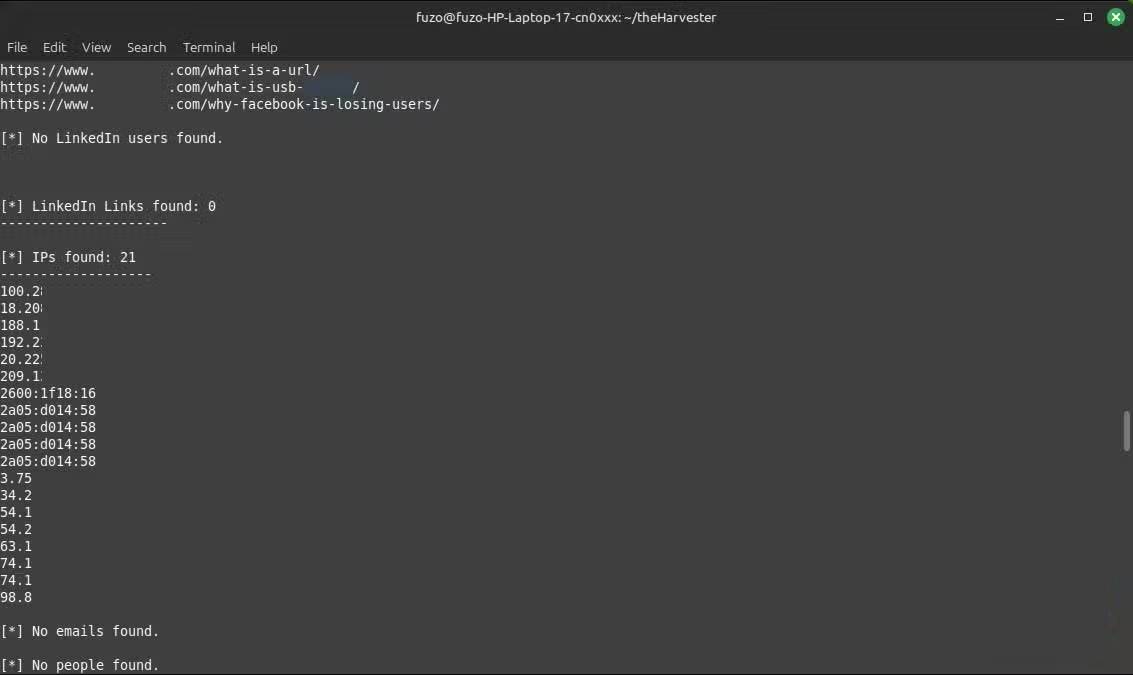
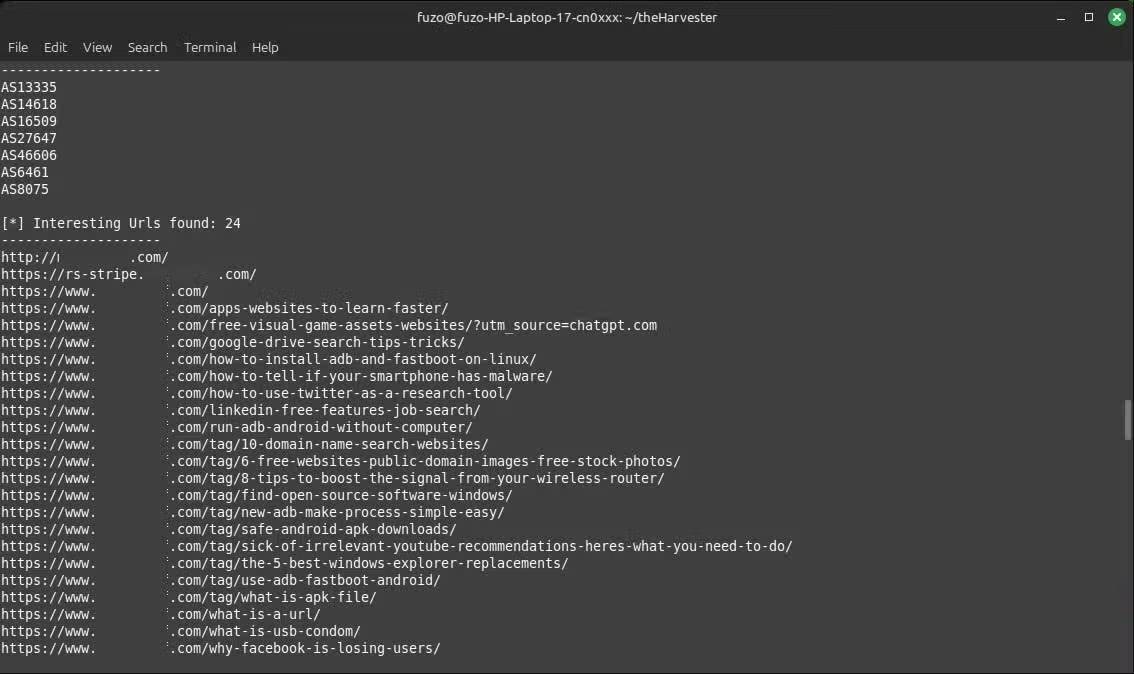
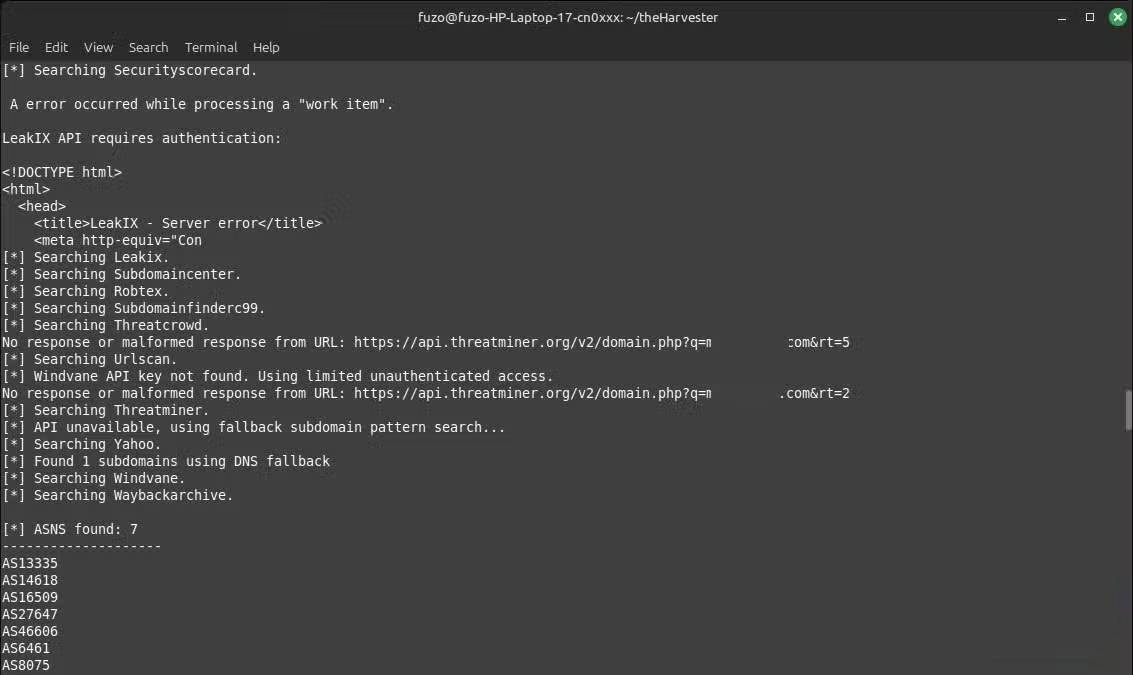
The results will then appear in the terminal. They usually include email, subdomain, hostname, IP address , and source. When running this search on a personal domain, many people are surprised to see how much personal information about themselves is floating around the internet – information that anyone can find from public sources.
Running this search on domains you manage can reveal old emails connected to accounts you forgot about and subdomains for test environments you no longer use. It does all this without compromising privacy or bypassing security.
Understand the results
Understanding email, subdomains, and digital exposure
The amount of information in the results can be intimidating; once you know what to look for, interpreting it is simple. They are different sections of your digital map. The Emails section appears first, showing publicly exposed points of contact. For a company, you might see addresses like support@domain.com, info@domain.com , or individual employee names. This information can be used by attackers to send phishing emails or determine hierarchy within an organization. For an individual, if the results show old emails, this should be seen as a wake-up call to close those accounts or take steps to limit their online visibility.
Subdomains are another factor to watch out for. If results return entries like test.example.com or oldblog.example.com, they may indicate abandoned servers or outdated sites. Unmonitored subdomains run on separate endpoints and can serve as entry points for attackers. You should clean them up or redirect them to minimize the risk of exposure.
The Hosts and IP Addresses section lists IP addresses and servers. They can reveal outdated infrastructure and show where domains are hosted. However, in all of this, the big picture is that what you think is hidden is actually publicly available and not difficult to access.
Minimize your online footprint
Simple ways to boost digital security right now
It's unsettling to see your digital footprint show up in theHarvester's results, but it's good to be aware of it. It helps you know what actions to take to narrow your footprint. A more drastic approach might be to remove yourself from the internet entirely.
A less drastic starting point, however, is subdomain cleanup. Disable or delete unused accounts, and deactivate or secure unused subdomains/staging environments. Each disabled subdomain is one less risk.
Also, address email leaks. Use email aliases for searchable addresses. Many people use aliases for just about everything, especially online shopping. So instead of afam@yourdomain.com, use newsletter@yourdomain.com. This will keep your primary inbox from being listed in public databases.
Last but not least, hide your domain registration details. A WHOIS lookup service can tell you if your personal information is publicly visible; if so, enable domain privacy protection through your domain registrar.
You should read it
- ★ How can dead cells create 'footprints of death', helping viruses spread?
- ★ How to play Among Us Online, download Among Us Online
- ★ Guidance on registration of cars, granting of license plates via the Internet
- ★ What security measures should be used when paying bills online?
- ★ How to speed up playing FIFA Online 4