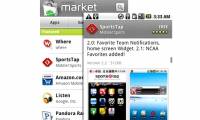
Dozens of applications on Android Market have been deleted because of malicious code. Users who have downloaded these infectious applications may lose data.

On March 3, a German cyber security expert, Ralph Langner, said he believed the US and Israel's Mossad intelligence agency had used the Stuxnet computer worm to attack Iran's

According to new research by Kaspersky Lab, the most frequently infected mobile devices are those using the most popular platforms, J2ME and Symbian. And the most popular mobile

An Iranian hacker claimed to take revenge for the nation after the Stuxnet 'worm' attacked the Islamic Republic's nuclear reactors.

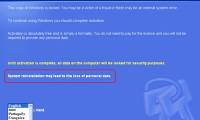
Hackers design fake websites to scare Internet users to download and install fake antivirus software.

Recently, a dangerous program appeared on the computer with the ability to hijack the system and give fake notifications to trick users.

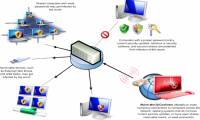
Classified as Rootkits, they are created to 'focus' on the main objects and activities of the Windows system, such as files, folders and processes stored in the memory of the

Security firm Symantec said it found evidence that the Stuxnet worm was intended to target uranium enrichment complexes at the Bushehr reactor, Iran. With the help of experts from

When it comes to Trojans, we are referring to a very malicious and dangerous type of computer program that can prevent, modify, back up or delete all user data, cause The main

Norton Internet Security (NIS) 2011 still maintains its inherent strength as fast installation and scanning speed, many impressive features but an inherent limitation is not yet

Security manufacturer Sophos said Facebook users can relax and stop warning each other about a virus with a Christmas tree theme, as this is all a hoax.

With a reasonable price, many useful features and high customization capabilities are what impress the security application AVG Internet Security 2011. However, this version is

Surveys with nearly 70,000 .vn websites using McAfee's website security assessment tool show that only 2.33% of websites contain malicious code, a very small percentage of the

Malware is a term that describes a relatively broad category of malicious software including viruses, worms, trojan horses, rootkits, spyware and adware.

According to Symantec Depository Service (Symantec Hosted Services), spam distribution containing shortened URL has peaked 23.4 billion spam in one day

Mr. Nguyen Minh Duc, director of network security department of Bkav, has just sent a warning: 'Christmas and New Year 2011 are approaching. Hackers will definitely take advantage

Atul Alex, an Indian hacker recently added a backdoor to the firmware of smartphones running Symbian S60.

If you receive an email saying 'Osama Bin Laden has been arrested' or 'Osama has been hanged', do not open the attachment.

Highly skilled hackers can use public information about code known as the Stuxnet virus to develop attack variants in many industries.

Predictably spike mobile malware is becoming a reality due to the widespread use of new generation smartphones running advanced operating systems.
 Dozens of applications on Android Market have been deleted because of malicious code. Users who have downloaded these infectious applications may lose data.
Dozens of applications on Android Market have been deleted because of malicious code. Users who have downloaded these infectious applications may lose data. On March 3, a German cyber security expert, Ralph Langner, said he believed the US and Israel's Mossad intelligence agency had used the Stuxnet computer worm to attack Iran's
On March 3, a German cyber security expert, Ralph Langner, said he believed the US and Israel's Mossad intelligence agency had used the Stuxnet computer worm to attack Iran's According to new research by Kaspersky Lab, the most frequently infected mobile devices are those using the most popular platforms, J2ME and Symbian. And the most popular mobile
According to new research by Kaspersky Lab, the most frequently infected mobile devices are those using the most popular platforms, J2ME and Symbian. And the most popular mobile An Iranian hacker claimed to take revenge for the nation after the Stuxnet 'worm' attacked the Islamic Republic's nuclear reactors.
An Iranian hacker claimed to take revenge for the nation after the Stuxnet 'worm' attacked the Islamic Republic's nuclear reactors. Hackers design fake websites to scare Internet users to download and install fake antivirus software.
Hackers design fake websites to scare Internet users to download and install fake antivirus software. Recently, a dangerous program appeared on the computer with the ability to hijack the system and give fake notifications to trick users.
Recently, a dangerous program appeared on the computer with the ability to hijack the system and give fake notifications to trick users. Classified as Rootkits, they are created to 'focus' on the main objects and activities of the Windows system, such as files, folders and processes stored in the memory of the
Classified as Rootkits, they are created to 'focus' on the main objects and activities of the Windows system, such as files, folders and processes stored in the memory of the Security firm Symantec said it found evidence that the Stuxnet worm was intended to target uranium enrichment complexes at the Bushehr reactor, Iran. With the help of experts from
Security firm Symantec said it found evidence that the Stuxnet worm was intended to target uranium enrichment complexes at the Bushehr reactor, Iran. With the help of experts from When it comes to Trojans, we are referring to a very malicious and dangerous type of computer program that can prevent, modify, back up or delete all user data, cause The main
When it comes to Trojans, we are referring to a very malicious and dangerous type of computer program that can prevent, modify, back up or delete all user data, cause The main Norton Internet Security (NIS) 2011 still maintains its inherent strength as fast installation and scanning speed, many impressive features but an inherent limitation is not yet
Norton Internet Security (NIS) 2011 still maintains its inherent strength as fast installation and scanning speed, many impressive features but an inherent limitation is not yet Security manufacturer Sophos said Facebook users can relax and stop warning each other about a virus with a Christmas tree theme, as this is all a hoax.
Security manufacturer Sophos said Facebook users can relax and stop warning each other about a virus with a Christmas tree theme, as this is all a hoax. With a reasonable price, many useful features and high customization capabilities are what impress the security application AVG Internet Security 2011. However, this version is
With a reasonable price, many useful features and high customization capabilities are what impress the security application AVG Internet Security 2011. However, this version is Surveys with nearly 70,000 .vn websites using McAfee's website security assessment tool show that only 2.33% of websites contain malicious code, a very small percentage of the
Surveys with nearly 70,000 .vn websites using McAfee's website security assessment tool show that only 2.33% of websites contain malicious code, a very small percentage of the Malware is a term that describes a relatively broad category of malicious software including viruses, worms, trojan horses, rootkits, spyware and adware.
Malware is a term that describes a relatively broad category of malicious software including viruses, worms, trojan horses, rootkits, spyware and adware. According to Symantec Depository Service (Symantec Hosted Services), spam distribution containing shortened URL has peaked 23.4 billion spam in one day
According to Symantec Depository Service (Symantec Hosted Services), spam distribution containing shortened URL has peaked 23.4 billion spam in one day Mr. Nguyen Minh Duc, director of network security department of Bkav, has just sent a warning: 'Christmas and New Year 2011 are approaching. Hackers will definitely take advantage
Mr. Nguyen Minh Duc, director of network security department of Bkav, has just sent a warning: 'Christmas and New Year 2011 are approaching. Hackers will definitely take advantage Atul Alex, an Indian hacker recently added a backdoor to the firmware of smartphones running Symbian S60.
Atul Alex, an Indian hacker recently added a backdoor to the firmware of smartphones running Symbian S60. If you receive an email saying 'Osama Bin Laden has been arrested' or 'Osama has been hanged', do not open the attachment.
If you receive an email saying 'Osama Bin Laden has been arrested' or 'Osama has been hanged', do not open the attachment. Highly skilled hackers can use public information about code known as the Stuxnet virus to develop attack variants in many industries.
Highly skilled hackers can use public information about code known as the Stuxnet virus to develop attack variants in many industries. Predictably spike mobile malware is becoming a reality due to the widespread use of new generation smartphones running advanced operating systems.
Predictably spike mobile malware is becoming a reality due to the widespread use of new generation smartphones running advanced operating systems.