1.9 million records of suspected terrorists managed by the FBI were leaked on the internet over a three-week period, from July 19 to August 9, 2021.

Here are some of the biggest ransomware attacks of 2021 so far, helping you identify trends and provide the insights you need to stay protected.

Security firm Zimperium has discovered a malicious campaign spreading through social media hijacking, third-party app stores, and externally installed apps.

Recently, Poly Network's official Twitter account posted a notice about this cross-chain protocol being hacked by hackers, taking away more than 600 million USD. It also urges

APT targeted attack is really complex but not as scary as we think, Zero-day vulnerabilities (Unknown and unpatched) used in APT are dangerous but not hard to find.

Recently, the cybersecurity agencies of Australia, the UK and the US have issued a joint report detailing the most exploited vulnerabilities in 2020 and 2021.

PetitPotam is a new attack method with the ability to take control of a domain controller and then take over the entire Windows domain.

Security researchers at Check Point Research (CPR) have just warned about the extremely dangerous XLLoader malware that is attacking both Windows and Mac users.

Microsoft helped Defender for Identity detect the PrintNightmare exploit to help the Security Operations team detect hacker attacks.

The HelloKitty ransomware uses a Linux variant that targets VMware's ESXi virtual machine platform for maximum damage.

Cybersecurity researchers are warning of a new malware - BIOPASS RAT - attacking online gambling companies in China.

RARLAB, the developer of WinRAR, has just released an urgent update to patch a dangerous vulnerability in their software.

The success of the MacBook M1 became a favorite technology product, and this also attracted the attention of hackers.

A ransomware attack against the international information technology company Kaseya appears to have infected hundreds of small businesses involved.

Although Microsoft releases patches for Windows vulnerabilities on a monthly basis, there are still security issues that remain. Recently, the US Cybersecurity and Infrastructure

After a 3-month hiatus under the name Babuk Locker, it has returned to creating custom ransomware executables that now target victims around the world.

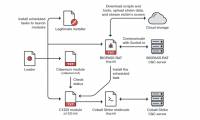
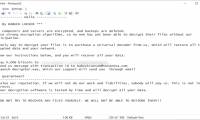
Supply Chain attack is a very dangerous type of attack and often has serious consequences.

A series of new critical security vulnerabilities have been found in the Jetson chip framework (NVIDIA) that could affect millions of active graphics cards worldwide.

APK file containing malicious code is a method that hackers often use to attack Android users. Unlike iOS, Android users can download and install apps from third-party app stores

The entire source code of the Paradise ransomware has been shared on a hacker forum called XSS.is. Based on this source code, even novice cybercriminals can create their own custom
 1.9 million records of suspected terrorists managed by the FBI were leaked on the internet over a three-week period, from July 19 to August 9, 2021.
1.9 million records of suspected terrorists managed by the FBI were leaked on the internet over a three-week period, from July 19 to August 9, 2021. Here are some of the biggest ransomware attacks of 2021 so far, helping you identify trends and provide the insights you need to stay protected.
Here are some of the biggest ransomware attacks of 2021 so far, helping you identify trends and provide the insights you need to stay protected. Security firm Zimperium has discovered a malicious campaign spreading through social media hijacking, third-party app stores, and externally installed apps.
Security firm Zimperium has discovered a malicious campaign spreading through social media hijacking, third-party app stores, and externally installed apps. Recently, Poly Network's official Twitter account posted a notice about this cross-chain protocol being hacked by hackers, taking away more than 600 million USD. It also urges
Recently, Poly Network's official Twitter account posted a notice about this cross-chain protocol being hacked by hackers, taking away more than 600 million USD. It also urges APT targeted attack is really complex but not as scary as we think, Zero-day vulnerabilities (Unknown and unpatched) used in APT are dangerous but not hard to find.
APT targeted attack is really complex but not as scary as we think, Zero-day vulnerabilities (Unknown and unpatched) used in APT are dangerous but not hard to find. Recently, the cybersecurity agencies of Australia, the UK and the US have issued a joint report detailing the most exploited vulnerabilities in 2020 and 2021.
Recently, the cybersecurity agencies of Australia, the UK and the US have issued a joint report detailing the most exploited vulnerabilities in 2020 and 2021. PetitPotam is a new attack method with the ability to take control of a domain controller and then take over the entire Windows domain.
PetitPotam is a new attack method with the ability to take control of a domain controller and then take over the entire Windows domain. Security researchers at Check Point Research (CPR) have just warned about the extremely dangerous XLLoader malware that is attacking both Windows and Mac users.
Security researchers at Check Point Research (CPR) have just warned about the extremely dangerous XLLoader malware that is attacking both Windows and Mac users. Microsoft helped Defender for Identity detect the PrintNightmare exploit to help the Security Operations team detect hacker attacks.
Microsoft helped Defender for Identity detect the PrintNightmare exploit to help the Security Operations team detect hacker attacks. The HelloKitty ransomware uses a Linux variant that targets VMware's ESXi virtual machine platform for maximum damage.
The HelloKitty ransomware uses a Linux variant that targets VMware's ESXi virtual machine platform for maximum damage. Cybersecurity researchers are warning of a new malware - BIOPASS RAT - attacking online gambling companies in China.
Cybersecurity researchers are warning of a new malware - BIOPASS RAT - attacking online gambling companies in China. RARLAB, the developer of WinRAR, has just released an urgent update to patch a dangerous vulnerability in their software.
RARLAB, the developer of WinRAR, has just released an urgent update to patch a dangerous vulnerability in their software. The success of the MacBook M1 became a favorite technology product, and this also attracted the attention of hackers.
The success of the MacBook M1 became a favorite technology product, and this also attracted the attention of hackers. A ransomware attack against the international information technology company Kaseya appears to have infected hundreds of small businesses involved.
A ransomware attack against the international information technology company Kaseya appears to have infected hundreds of small businesses involved. Although Microsoft releases patches for Windows vulnerabilities on a monthly basis, there are still security issues that remain. Recently, the US Cybersecurity and Infrastructure
Although Microsoft releases patches for Windows vulnerabilities on a monthly basis, there are still security issues that remain. Recently, the US Cybersecurity and Infrastructure After a 3-month hiatus under the name Babuk Locker, it has returned to creating custom ransomware executables that now target victims around the world.
After a 3-month hiatus under the name Babuk Locker, it has returned to creating custom ransomware executables that now target victims around the world. Supply Chain attack is a very dangerous type of attack and often has serious consequences.
Supply Chain attack is a very dangerous type of attack and often has serious consequences. A series of new critical security vulnerabilities have been found in the Jetson chip framework (NVIDIA) that could affect millions of active graphics cards worldwide.
A series of new critical security vulnerabilities have been found in the Jetson chip framework (NVIDIA) that could affect millions of active graphics cards worldwide. APK file containing malicious code is a method that hackers often use to attack Android users. Unlike iOS, Android users can download and install apps from third-party app stores
APK file containing malicious code is a method that hackers often use to attack Android users. Unlike iOS, Android users can download and install apps from third-party app stores The entire source code of the Paradise ransomware has been shared on a hacker forum called XSS.is. Based on this source code, even novice cybercriminals can create their own custom
The entire source code of the Paradise ransomware has been shared on a hacker forum called XSS.is. Based on this source code, even novice cybercriminals can create their own custom