Warning: Babuk Locker Ransomware is Active Again, Attacking the World
Babuk Locker is a ransomware operation born in early 2021, targeting companies, stealing their data and extorting money.
After carrying out an attack on Washington DC's Metropolitan Police Department (MPD), the ransomware gang ceased operations in April and switched to a model of non-encrypted data extortion under the name PayLoad Bin.
Last week, security researcher Kevin Beaumont discovered someone had uploaded the Babuk operation's ransomware generator to VirusTotal.
Creating custom ransomware is simple. All the threat agent has to do is modify the accompanying note, including contact information. Then run the executable to create a custom ransomware encoder and decoder that targets Windows, VMware ESXi, Network Attached Storage (NAS) x86, and an ARM NAS device.
Soon after this ransomware generator leaked online, a threat actor started using it to launch a ransomware campaign.
On June 29, on Reddit, a victim reported they were hacked by software claiming to be "Babuk Locker".
BleepingComputer quoted security researcher MalwareHunterTeam as saying, starting June 29, ID Ransomware received a spike in Babuk Locker.
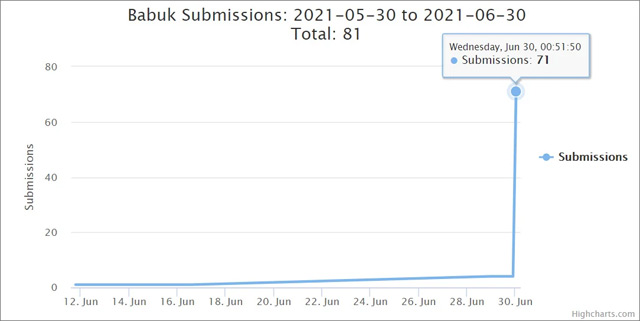
Victims come from all over the world, and ransom notes are all sent from the email address of the threater.
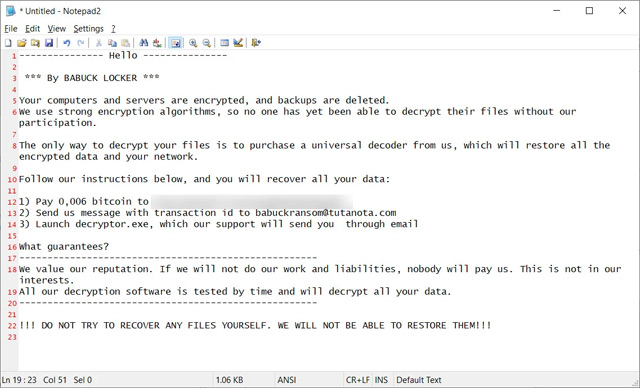
Like the original operation, this ransomware attack adds the .babyk extension to the encrypted file name and issues a ransom note called How To Restore Your Files.txt.
Compared to asking for hundreds of thousands and millions of USD in the first operation, this time they only demanded 210 USD from the victim.
Locker uses a dedicated Tor payment site to negotiate with victims. However, the new attacks are using email, specifically babukransom@tutanota.com, to communicate with victims.
It's not clear how the ransomware is being spread, but there is a thread where victims can share more information about the Babuk Locker attack.