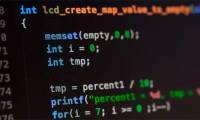
Vulnerabilities in Android allow malware to read device information even without permission
a vulnerability in android allows poisoned applications to pass the request to allow the right to read device information, thereby 'peeking out' more information than allowed,