Detects code execution vulnerabilities in WinRAR, noting more than 100 infringement cases
A code execution vulnerability in WinRAR has been exploited more than 100 times separately by hackers in the first week since it was revealed, and it is expected that this number will continue to increase in the future.
So what makes hackers interested in exploiting this vulnerability so much? According to security researchers, the number of more than 500 million users and at the same time the vulnerability (CVE-2018-20250) is available on all versions released in the last 19 years of the data compression platform. These are two attractive factors for attackers. Not only that, the full control of the victim's system is also a lucrative piece of cake that no hacker does not want.
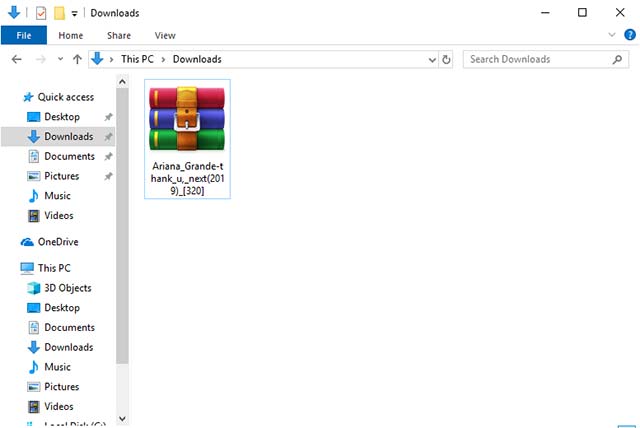
McAfee senior security researcher Craig Schmugar reported on Thursday last week that during a recent attack, his team had observed hackers to lure victims into a trap with one. Edited copy of the album Ariana Grande "Thank U, Next".
- Counter-Strike 1.6 features new Zero-Day, allowing malicious servers to hack gamers' computers
Specifically, music files will be sent in an archive named "Ariana_Grande-thank_u, _next (2019) _ [320] .rar". If users use a version of WinRAR that contains errors to extract these files, malicious code will spread to the Windows Startup folder on their system.
Craig Schmugar's team said that up to now, more than 100 CVE-2018-20250 cases have been identified, and most cases have been recorded as victims of this vulnerability. All IDs in the United States.
"User Access Control (UAC) has been omitted, so there are absolutely no warnings displayed to users. Next time their system starts up, the section Malware will also start working, "explains Craig Schmugar.

- Intel has overcome serious vulnerabilities in graphics drivers for Windows
The first mining case occurred 2 days after the security error was announced
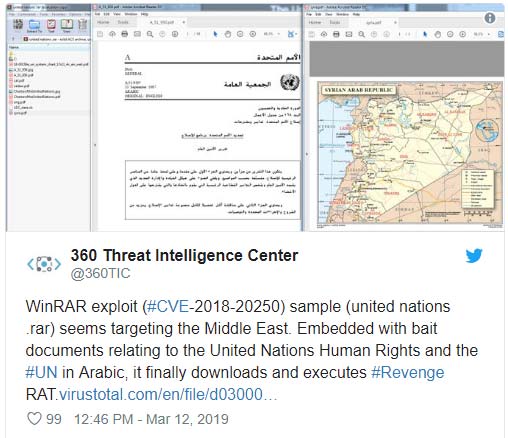
Security researchers from Microsoft's 360 (360 Threat Intelligence Center) Intelligence Intelligence Center have discovered exploits of this WinRAR vulnerability in nature on February 20, just two days later. when the vulnerability is made public. They are used in phishing attacks through images or archives.
Recently, Chinese security researchers have also discovered a campaign to use UN Human Rights-related documents to deceive and seduce victims in the Middle East. The main 'kernel' used in this attack is a remote access tool (RAT), currently detected by at least 28 antivirus software.
- There were 12,449 serious data breaches recorded in 2018, an increase of 424% compared to 2017
CVE-2018-20250 was discovered by Checker Nadav Grossman from Check Point using WinAFL. This is a logical error that conveys the path of the ACE in the 'unacev2.dll' library added to WinRAR to extract the old archive format, rarely used at the present time.
This library code has remained unchanged since 2005. Meanwhile, its source code has been lost, so those responsible for maintaining WinRAR can no longer fix the vulnerability of the platform. this too. The most feasible solution today is to remove support for ACE's repository in the first beta of WinRAR 5.70.
However, users can still get ACE support in WinRAR by applying specific created micropatch to solve the problem. This solution is available through the 0Patch platform from ACROS Security.
In general, WinRAR users should use one of two solutions to be able to combat these CVE-2018-20250 vulnerability exploitation methods.
You should read it
- ★ Detecting new malware on WinRAR can infiltrate computers and steal data
- ★ Microsoft expert discovered a series of serious code execution errors in IoT, OT devices
- ★ The malicious video file causes users to lose control of the device 'storming' in the Android world
- ★ Find bug in Emotet malware, prevent it from spreading for 6 months
- ★ ProFTPD remote code execution vulnerability affects more than 1 million servers worldwide