
Learn about Man-in-the-Middle attacks - Obtain SSL control
in the next part of this series, we will introduce you to ssl spoofing attacks, besides some theories under ssl connections and what is safe.

in the next part of this series, we will introduce you to ssl spoofing attacks, besides some theories under ssl connections and what is safe.

in the first part of the series introducing some of the most commonly used mitm attacks, we will introduce you to arp cache spoofing, dns spoofing, hijacking (hijacking) attacks.

in this section, i will show you how to attack session hijacking, along with some theory and how to perform attacks, as well as how to detect and prevent them.

in the first part of this article series, i showed you how a device's arp and arp cache can be faked to redirect network traffic of computers to a different machine. bad purpose.
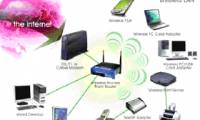
if you start to see connectivity problems for your network, then clearing the arp cache is the first thing you need to do.