Learn about Man-in-the-Middle attacks - DNS spoofing
 Learn about Man-in-the-Middle attacks - ARP Cache spoofing
Learn about Man-in-the-Middle attacks - ARP Cache spoofing
In this article we will continue the discussion of Man-in-the-Middle attacks, specifically focusing on introducing another type of MITM attack called DNS spoofing.
In the first part of this article series, I showed you how a device's ARP and ARP cache can be faked to redirect network traffic of computers to a different machine. bad purpose. In this article, we introduce you to another type of MITM attack, DNS spoofing. If you have not read the ARP Cache spoofing section, you should go back and read it first because this article will use some of the techniques that I have introduced in that article.
DNS spoofing
DNS spoofing is an MITM technique used to provide false DNS information to a host so that when a user browses to an address, for example, www.bankofamerica.com has IP XXX.XX.XX.XX , this attempt will be sent to a fake www.bankofamerica.com address located at the IP address YYY.YY.YY.YY, this is the address that the attacker created before to steal the information. Online bank account from users. This attack can be done quite easily and in this article we will look at how it works, how it does the attack and, finally, how to counteract it.
DNS communication
The Domain Naming System (DNS) protocol as defined in RFC 1034/1035 can be considered as one of the most important protocols used in the Internet. In short, easy to understand, whenever you type a web address such as http://www.google.com into your browser, DNS requests will be sent to the DNS server to find the same IP address. good value for the domain you just entered. Internet routers and devices will not understand what google.com is, they only understand addresses such as 74.125.95.103.
The DSN server works by saving a database of entries (called resource records) IP addresses to map DNS names, communicate those resource records to the client and to the DNS server. other. DNS server architecture throughout the enterprise and the Internet is a rather complicated thing. As a matter of fact, you can imagine them as dedicated notebooks for DNS architecture. We are not going to introduce aspects of architecture or even different types of DNS traffic, but only introduce a basic DNS session, you can see in Figure 1.

Figure 1: DNS query and response
DNS works in the form of queries and responses (query / response). A client that needs to resolve DNS for a certain IP address sends a query to the DNS server, which sends the requested information in its response packet. Standing on the client perspective, only the two packages that appear now are query and response.

Figure 2: DNS query and response packets
This scenario will be a bit complicated when considering DNS regression. Thanks to the Internet DNS hierarchical structure, DNS servers need to be able to communicate with each other to provide answers to queries submitted by the client. If all goes well as expected, our internal DNS server will know the name to map the IP address to the server within the local network, but cannot expect it to know the same address. between Google or Dell. This is where recursion plays an important role. Recursion occurs when a DNS server queries another DNS server as the client creates the request. In essence, this method will turn a DNS server into a client, see Figure 3.

Figure 3: DNS query and response by recursion
See page 2
DNS spoofing
There are many ways to make DNS spoofing possible. We will use a technique called DNS ID spoofing.
Each DNS query sent over the network contains a unique identifier, the purpose of this identifier is to distinguish queries and respond to them. This means that if one of our attacking computers can block certain DNS queries from being sent from a particular device, all we need to do is create a fake package. contains that identifier so that the packet is accepted by the target.
We will complete this process by taking two steps with a simple tool. First, we need to fake the ARP cache of the target device to reroute its traffic through our attacking host, which in turn can block DNS requests and send spoofed packets. The purpose of this scenario is to trick users in the target network from accessing malicious websites instead of the websites they are trying to access. For more clarity you can refer to the attack image below.

Figure 4: DNS spoofing attack using DNS ID spoofing method
There are a number of other tools that can be used to perform DNS spoofing. We will use one of them, Ettercap, which can be used for both Windows and Linux. You can download Ettercap to your device here. If you learn a little more about this website, you will probably find that Ettercap has many other great functions besides DNS spoofing and can be used to perform many types of MITM attacks.
If you install Ettercap on a Windows computer, you will find it has a great graphical user interface (GUI), but in this example, we will use the command line interface.
Before executing Ettercap, you need to make a little configuration. Ettercap at its core level is a data sniffer, which uses plug-ins to perform various attacks.The dns_spoof plug-in is what we will do in this example, so we must adjust the configuration file associated with that plug-in. On Windows systems, this file can be downloaded at C: Program Files (x86) EttercapNGshareetter.dns , and at /usr/share/ettercap/etter.dns . This is a pretty simple file and contains the DNS records you want to fake. For testing purposes, we want any user trying to access yahoo.com to be directed to a host on the local network, add an entry highlighted in Figure 5.

Figure 5: Add a fake DNS record to the etter.dns
These entries will instruct the dns_spoof plug-in that when you see a DNS query for yahoo.com or www.yahoo.com (with a type A resource record), it will use the IP address 172.16.16.100 to respond. pay. In the real scenario, the device at 172.16.16.100 IP address will run a web server software and display it to fake website users.
See page 3
When this file is configured and saved, it is possible to execute the command string used to launch the attack. The command string uses the following options:
- -T - Specify use of text interface
- -q - Run commands in 'silent' mode so that captured packets are not displayed on the screen.
- -P dns_spoof - Specifies the use of dns_spoof plug-in
- -M arp - Initiate an ARP spoofing ARP attack to block packets between hosts.
- // // - Specify the entire network as the target of attack.
The final command sequence for our purpose is:
Ettercap.exe –T –q –P dns_spoof –M arp // //
When you run the above command, you will start a two-stage attack, first spoofing the device's ARP cache on the network, then issuing fake DNS query responses.

Figure 6: Ettercap is listening actively to DNS queries
When launched, anyone trying to access www.yahoo.com will be redirected to our malicious website.
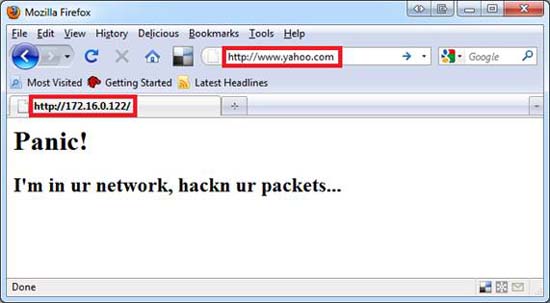
Figure 7: Results of trying to fake DNS from the user perspective
Prevent DNS spoofing
It is quite difficult to prevent DNS spoofing because there are few signs of attack. Usually, you don't know your DNS has been tampered with until that happens. What you get is a completely different website than what you expected. In large-scale attacks, you probably won't know that you've been tricked into importing your important information into a fake website until you get a call from the bank asking why you're Withdraw so much money. Although it is difficult, not all measures can prevent these types of attacks, here are some things you need to do:
- Protect your internal computers : The same attacks are usually executed from within your network. If the network devices are secure, you will reduce the chances of the hosts being compromised and used to launch a phishing attack.
- Do not rely on DNS for secure systems : On highly sensitive and secure systems, not browsing the Internet on it is the best way to not use DNS. If you have software that uses hostnames to perform some of its tasks, they need to be adjusted to what is needed in the device configuration file.
- Use IDS : An intrusion detection system, when properly placed and deployed, can unmask ARP cache spoofing and DNS spoofing.
- Using DNSSEC: DNSSEC is a new alternative to DNS, using signed DNS records to ensure the validity of query responses. Although DNSSEC has not been widely deployed, it has been approved as 'the future of DNS'.
DNS spoofing is a dangerous form of MITM attack when paired with malicious intentions. Using this technology attackers can take advantage of phishing techniques to steal important user information, or install malware on a exploited drive, or cause a denial attack. service. In the next part of this article series, I will continue the discussion of how to ' pass the hash ' attacks and how this attack can be used to log on to Windows computers without to user passwords.