What is a botnet? How does a botnet work and what is its structure?
People are constantly using the Internet to run their lives and the digital devices they depend on. Along with the benefits of the Internet, there are also 'side effects' such as viruses, spam, hackers and online scams. The number of fraudulent websites, malicious emails, destructive viruses, etc. has increased not only in the United States but also globally. Among the various threats that individuals and businesses are facing today through the Internet, botnets are the most common. A botnet is a network of computers that are remotely controlled by hackers.
Botnets are used by hackers to spread ransomware to laptops, phones, tablets, computers, etc. They can go undetected and you may not even know if your device is part of a botnet.
What is a botnet?
The word 'botnet' is a combination of two words, 'robot' and 'network' . Here, a cybercriminal plays the role of a 'botmaster' using a Trojan virus to compromise the security of a number of computers and connect them to a network for malicious purposes. Each computer on the network acts as a 'bot', and is controlled by the bad guys to spread malware, spam or malicious content to launch the attack. Botnet is also called a zombie army because the computers involved are being controlled by someone other than their owner.
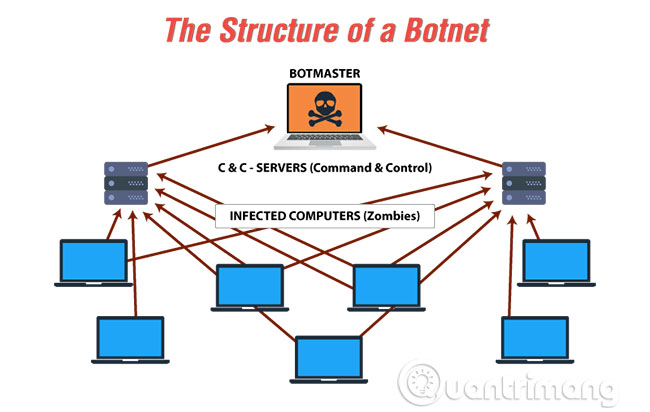
Botnets were originally created to serve as a tool in Internet Relay Chat (IRC) channels. Eventually, bad guys would exploit vulnerabilities in the IRC network and bots were developed. These were intentionally created to perform malicious activities such as logging keystrokes, stealing passwords, etc.
Structure of a botnet
Botnet structures typically take one of two forms: the client-server model or the peer-to-peer model.
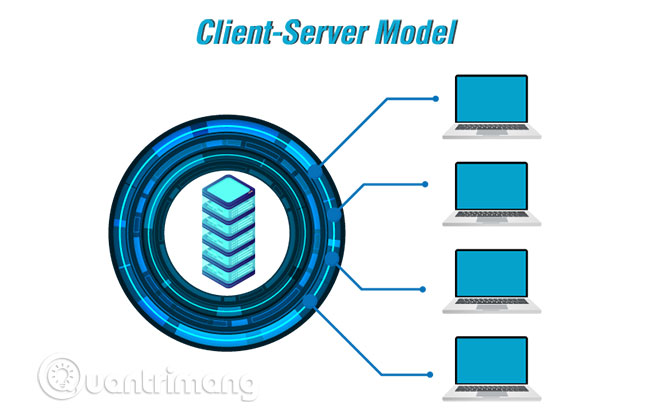
Client - server model
In the client-server architecture, a basic network is set up with a server, which acts as the botmaster. The botmaster controls the communication from each client to set up commands and control the client devices. The client-server model works with the help of special software and allows the botmaster to maintain control. This model has a few disadvantages such as it can be easily located and has only one point of control. In this model, if the server is destroyed, the botnet is 'dead'.
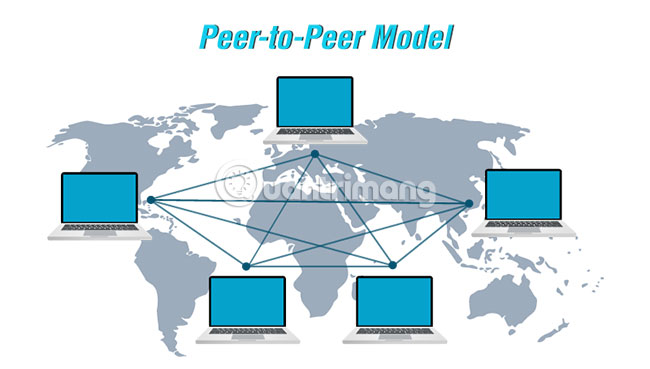
Peer-to-peer model
To overcome the drawbacks of relying on a centralized server, botnets have evolved. New botnets are connected to each other in a peer-to-peer structure. In the P2P botnet model, each connected device acts independently as a client and server, coordinating with each other to update and transmit information back and forth. The P2P botnet structure is more powerful because there is no single centralized control point.
Types of Botnet Attacks
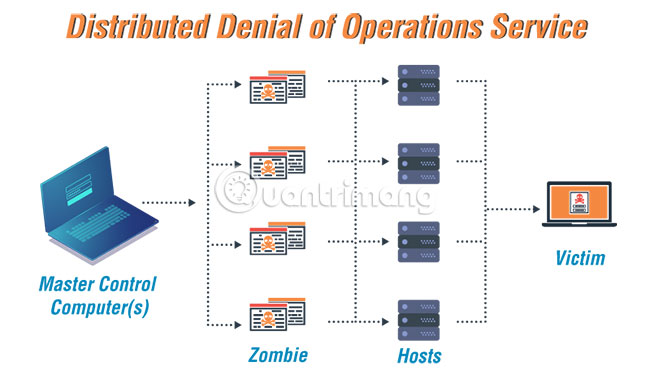
Distributed Denial of Operations Service (DDoS)
A botnet can be used for a Distributed Denial of Service (DDoS) attack to disrupt network connectivity and services. This is done by overloading the victim's computational resources or consuming bandwidth.
The most commonly performed attacks are TCP SYN and UDP flood attacks. DDoS attacks are not limited to web servers, but can target any service connected to the Internet. The severity of the attack can be increased by using HTTP floods on the victim's website. This form of spidering is performed to effectively increase the load.
One of the largest DDoS botnet attacks involved IoT and used the Mirai botnet virus. The virus targeted and took control of tens of thousands of poorly protected internet devices, then turned them into bots to launch a DDoS attack. Mirai continued to expand, making the attack more complex.
Spamming and traffic monitoring
A bot can be used to identify the presence of sensitive data in zombies or infected computers. It can also locate rival botnets, if installed on the same machine. Some bots can open a SOCKS v4/v5 proxy (a common proxy protocol for TCP/IP-based networks). When a SOCKS proxy is enabled on a compromised machine, it can be used for various purposes such as spamming. Bots use packet sniffers to monitor information or data transmitted by the compromised machine. Sniffers can retrieve sensitive information such as usernames and passwords.
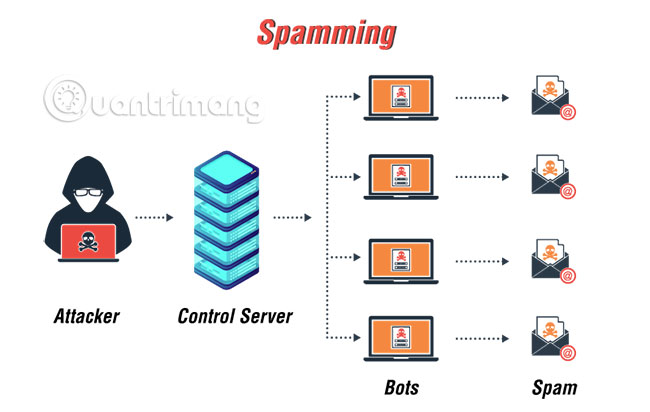
Grum is a type of spam that is difficult to detect because it infects files used by the Autorun registry. The botnet has attracted research because it is relatively small, with only 600,000 members, but accounts for 40 billion spam emails per day, or about 25% of all spam emails.
Keylogging
With the help of keyloggers , it becomes easy for botmasters to get sensitive information and steal data. Using keylogger programs, attackers can collect the keys entered in PayPal, Yahoo, etc.
A type of spyware identified as OSX/XSLCmd, which can migrate from Windows to OS X, includes keylogging and screenshot capabilities.
Mass identity theft
Different types of bots can be combined to commit large-scale identity theft, which is one of the fastest growing crimes. Spam emails are sent by bots to direct traffic to fake websites that represent bots to collect personal data. Bots can be used to appear as legitimate companies and ask users to submit personal information, such as bank account passwords, credit card details, tax details, etc. Mass identity theft occurs by using phishing emails to trick victims into entering login credentials on websites such as eBay, Amazon, or even banks.
Pay-per-click abuse
Google's AdSense program allows websites to display Google ads and earn money from them. Google pays website owners based on the number of clicks their ads receive. Infected machines are used to automatically click on a website, increasing the number of clicks sent to the company by the ad.
Botnet spread
Botnets are also used to propagate other botnets by convincing users to download a specific program and executing it via email, HTTP, or FTP. Often, viruses using this botnet are spread via email. Two security researchers in January 2017 discovered the 'Star Wars' Twitter botnet, which consisted of 350,000 bot accounts that tweeted random quotes from the movie series. Such bots, if allowed to persist, could create fake trending topics, send unwanted spam, launch cyber attacks, and more.
Adware
Adware is used to attract users by displaying advertisements on websites or applications. They appear without the user's permission, with the original advertisement replaced by fraudulent adware that infects the system of any user who clicks on it.
Adware looks like harmless ads, but it uses spyware to collect browsing data. To get rid of adware, you need ad blocking software . While there are many free and paid versions of ad blocking software available, it's best to use a licensed option. Many antivirus packages also come with an anti-malware program.
Botnets can be banished or stopped from infiltrating a computer by using anti-malware programs that can detect infections on hard drives or network traffic and deal with them immediately. Otherwise, the most effective approach would be to learn to be fully aware of how to combat botnets.
Botnet prevention

As we all know, prevention is always better than cure, users can prevent their systems from being infected by following some steps. Preventive measures can be taken at the individual user level and at the network level.
Personal level
- Install anti-virus or anti-spam software and keep it updated regularly.
- Turn on firewall settings and restrict unwanted access.
- Make sure the operating system is updated from time to time.
- Do not download illegal content such as music, games, pirated files, etc. from the Internet.
- Do not click on attachments or links from unknown emails.
Network level
- Has firewall, IDS/IPS system and content filtering features.
- Monitor for unusual traffic spikes.
- Features DDoS protection in place.
- If a personal user system is suspected of being infected with a botnet, try to remove the malware immediately. If this is not done promptly, other systems on the network may also be infected.
- Make sure that all individuals in the company have the updated software on their systems.
- Monitor firewall logs to identify botnet command and control centers.
- If any infection is identified, notify your anti-virus software vendor immediately.