
DDoS is ranked as the top threat for businesses in 2018
ddos attacks are considered to be the top high threats for global organizations and businesses.

ddos attacks are considered to be the top high threats for global organizations and businesses.

as governments, businesses and individual users increasingly trust and use the internet for their daily activities, maintaining cybersecurity will still be an essential task for

scientists have developed a new algorithm that can help detect and prevent cyberattacks on gps-enabled devices in real time.

a 21-year-old was jailed for two years after being accused of conducting ddos attacks on high-tech companies such as skype and google.

researcher mathy vanhoef from leuven university discovered a serious security flaw on wi-fi protected access ii (wpa2) network security protocol.

due to the low income and inability to pay ransom, a victim sent an email to the hacker and received unexpected results.
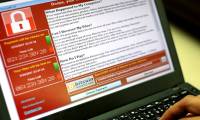
despite being stopped by a 22-year-old hero, the wannacry 2.0 version will be a new challenge for heroes.

microsoft has released an emergency patch for windows versions to prevent further attacks by wannacry ransomware (microsoft flagged as ransom: win32 / wannacrypt).

the hacker who spreads the most dangerous virus in 2017 also tries to make a joke in his ransom notice with a joke.

'hundred listeners are not equal to one', this proverb might not be accurate when it comes to cyber security.