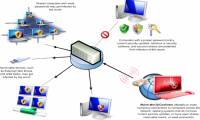
2011: malware transferred from computer to ... pocket pants
predictably spike mobile malware is becoming a reality due to the widespread use of new generation smartphones running advanced operating systems.

predictably spike mobile malware is becoming a reality due to the widespread use of new generation smartphones running advanced operating systems.

according to an article on the san jose mercury site, mobile phones are the target of 500 malware attacks.

in the end, a security vulnerability worm that microsoft had blocked with an emergency update 11 days ago appeared on the internet.

security experts have listed the top 10 attacks on the web and forecast online banking transactions at the highest risk of hackers. the discovery of duong ngoc thai, a vietnamese

sony suddenly was attacked by hackers. the cause is most likely due to the firm's strong intellectual property protection measures.

the type of attack technique iframe injection is still the most basic and popular form of cross-site scripting - xss model .

microsoft on october 28 has advised its customers that the vulnerabilities that attack the windows operating system are released by hackers.

lulz security's emerging hacking group challenges 'catch us if possible' and insists on knocking down as many websites as we did with sony, the us senate, cia ... until it was
outside of facebook, there will definitely be no more personal online space than your email inbox. currently, email has a huge number of users and is expected to reach 1.6 billion