Neprodoor trojan warning appears in Vietnam
Users of domestic computers have been warned about a new dangerous trojan named Neprodoor originating from Russia, which has appeared and spread on computers in Vietnam .
Computer worms called Trojan.Neprodoor come from Russia, are sophisticatedly designed to bypass authentication systems, automatically register accounts of mail: hotmail, yahoo, gmail . and distribute mail messages. junk, which does not exclude hackers inserting malicious code. In Vietnam, Neprodoor has infected some computers and sent samples to CMC Infosec's virus analysis center.
Infection works on Neprodoor computers.
Trojan.Neprodoor was first discovered on March 2, 2009 and acts as a botnet. They use victim machines to distribute spam, and combine stealth rootkit technology so they can bypass most of the current security products.
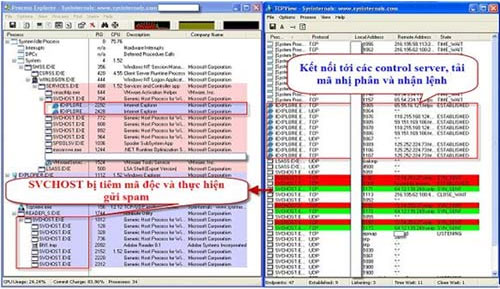
Through the Internet, Trojan.Neprodoor infects the ndis.sys file system and injects malicious code into svchost.exe file to perform spam distribution process. After successful infection, the trojan will communicate with the server and perform any actions that the server requires, such as providing confidential information of the victim machine, downloading the binary code and executing the attack. public remote.
Neprodoor is built with sophisticated techniques. Normally when registering an email account, the user needs an account name, password and CAPTCHA validation code (which is a system used at registration pages, which shows image files containing information from which the confirmation recognize that the user is operating, not the computer bot is automatically registered).
But with Neprodoor worms, mail accounts from Google, Yahoo or Hotmail can be registered automatically because Neprodoor can disable the captcha system by connecting to a server system that does this (by hackers). Russia holds). Therefore, spam sent from these accounts will automatically not be considered spam by mail systems.
Mr. Nguyen Hoang Giang - CMC Virus Analyst InfoSec commented: ' This is a dangerous type of Trojan, new variants are always updated from the attacker's server control system. The infected machine will become a zombie machine in their botnet system '
When infected Trojan.Neprodoor users can see the changes in the operation of the system such as memory consumption, affected bandwidth, appear svchost.exe, reader_s.exe processes created, expression The network connection icon is always on even though the user is not using Internet-related programs.
Most operating systems are capable of getting this Trojan: Windows 2000, Windows 95, Windows 98, Windows Me, Windows NT, Windows Server 2003, Windows Vista, Windows XP.
The object that Neprodoor hacker spreads towards is not just businesses but even individual users become targets. There are currently no specific statistics on the amount of computers infected with Neprodoor because in fact this Trojan works very quietly, it does not burst at a specific time and this is just a prelude to a Spam campaign in the near future.
Currently, CMC InfoSec recommends that users should avoid sensitive websites or strange websites and make sure that the Antivirus program is updated regularly to "prevent more than cure".
Currently, there is no anti-virus software, any malicious code in the world to thoroughly eliminate this worm when they infect the system. Users can perform removal of this Trojan manually as follows :
1. Disconnect the network
2. Disable System Restore
3. Use Process Explorer software from Microsoft kill processes: reader_s.exe and processes named svchost.exe in the explorer.exe branch.
4. Go to Registry, find key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
Delete the reader_s key containing the content C: WINDOWS system32reader_s.exe
5. Go to C: WINDOWS system32 -> delete the file reader_s.exe
6. Because it is infected with the ndis.sys file system, it is necessary to use the Windows installation disk to restore the original ndis.sys file in C: WINDOWSsystem32drivers
7. To make sure that the threat is completely removed, perform a full scan of the computer with antispam and antivirus software updated to the latest version.