Windows Vista: Support users to use Remote Assistance
Remote Assistance (RA) in Windows Vista includes a number of improvements in connectivity, performance, usability and security, along with a number of other advanced features that will make it useful. more used in Windows XP. With Group Policy support, command line scripting capabilities, session logs, bandwidth optimization and a number of other things will make RA an essential tool for businesses to support users in drama. Help Desk version. Part 1 of this article will show you how RA works in Vista, how to use it to support users, how to manage it with Group Policy and how to script it.
Learn about Remote Assistance
 User support is an essential function of IT departments and Help Desk. However, the usual technical support provided on the phone system or 'chat' tools does not generally produce much efficiency. Therefore, supporting users is often time consuming and costly for large enterprises. For example, users often have difficulty describing the exact nature of the problem they are having. Because of the lack of experience and technical knowledge, users can try to describe their problem by non-technical, inaccurate language. Therefore, Help Desk is greatly reduced because it requires a series of simple questions to determine the problem that users are having. Doing many of these questions can sometimes cause a bad feeling for Help Desk, reduce the effectiveness of the experience they have, and sometimes make users tend to avoid contacting the team. Support when problems arise.
User support is an essential function of IT departments and Help Desk. However, the usual technical support provided on the phone system or 'chat' tools does not generally produce much efficiency. Therefore, supporting users is often time consuming and costly for large enterprises. For example, users often have difficulty describing the exact nature of the problem they are having. Because of the lack of experience and technical knowledge, users can try to describe their problem by non-technical, inaccurate language. Therefore, Help Desk is greatly reduced because it requires a series of simple questions to determine the problem that users are having. Doing many of these questions can sometimes cause a bad feeling for Help Desk, reduce the effectiveness of the experience they have, and sometimes make users tend to avoid contacting the team. Support when problems arise.
Users are also often challenged by instructions from Help Desk while they are being supported. Well-trained support team members will try to avoid using technical terms when communicating with users, but although using explaining language can improve the support experience, it can cause takes a lot of time and is tired. For example, telling a user how to use Disk Cleanup from the System Tools system tools in Accessories may require more explanation than usual, this way of communication may take a long time for the situation. support, make them feel costly for the company.
Remote Assistance (RA) helps you solve these problems by allowing support team members to view the user's desktop in real time. Users seeking assistance can demonstrate the nature of the problem for the support member. This will be faster and more efficient to exchange issues than using email. If necessary, users can also give members support access to acknowledge the shared control of the user's computer, thereby showing users how to solve problems easily. Therefore, Remote Assistance allows solving problems faster, improving the support experience and lowering the total cost of supporting users in a collaborative environment.
Remote Assistance and Remote Desktop
Remote Assistance and Remote Desktop are different features available in Windows Vista.Remote Desktop relies primarily on Microsoft terminal services and is a tool for remote login to remote computers.When you use Remote Desktop to connect to a remote computer, a new user session will be established.Remote Desktop can also establish sessions with a computer without an interactive session running (no users log on locally) like servers without a machine.
Remote Assistance is a tool that helps troubleshoot problems for users on their computers. To use Remote Assistance, both users and helpers must be present on their computers. Unlike Remote Desktop, Remote Assistance does not create a new session, but instead allows the Helper to work in the user's existing session. The user's desktop is remote controlled by a helper, the helper can view the user's desktop with the user's consent, sharing control on the desktop.
This is a completely different way to summarize the differences between these two features: In Remote Assistance, both the relevant user is searching at the same desktop using the same login information and can share permissions. control on that desktop;As for Remote Desktop, when the remote operator logs in, the logged-in user must log out.
RA improvements in Windows Vista
Windows Vista includes some new and advanced features of RA than in Windows XP:
- Improve connectivity by using Teredo and IPv6.
- Improved user interface, allowing easy launch and use.
- Independent executable file (msra.exe) applies command line arguments and can easily be scripted.
- Improve performance with faster startup and connection times, optimized bandwidth performance for screen upgrades.
- Improve security with passwords and mandatory integration with UAC (User Account Control).
- Offer RA new via IM (Instant Message) and an open API for integrating peer applications.
- Traditional Group Policy settings are improved to be easily managed.
Remote Assistance in Vista does not have the following features already in XP:
- Not much support for MAILTO method of Remote Assistance
- Not much support for voice sessions.
How Remote Assistance works
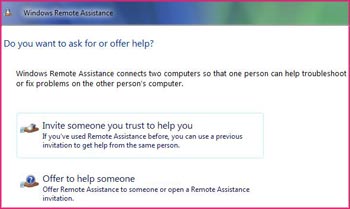
In Remote Assistance, the person who needs help is defined as a user ( User (or Novice )) and the support person provides support to the user ( Helper (or Expert )). RA is launched from the Start menu by selecting All Programs, clicking Maintenance, and then selecting Windows Remote Assistance. You can also launch it from the command prompt by typing msra.exe .
Remote Assistance has two basic operating modes:
1. Solicited RA . In Solicited RA (also known as Escalated RA) the user requests assistance from the Helper by initiating an RA session by email, IM or by providing the Helper with a copy of a saved file. (* .MsRcIncident). These methods use a different mechanism:
- Solicited RA Using E-mail (Solicited RA using Email) This method requires that the email client is being used by a simple mail client application interface - User support Simple Mail Application Programming Interface (SMAPI). One of the examples of email clients that supports SMAPI is Windows Mail included in Windows Vista. Other examples are Microsoft Outlook and third-party clients. In this method, the user launches the RA user interface to create an email message with an RA file (* .MsRcIncident) attached to the message. The user must enter a password for the RA session, which must be communicated to the Helper with another method (OOB) such as dialing a telephone number to the Helper. When the Helper receives the user's RA invitation, they will open the attached card, enter the password that the user has given, and the RA session starts. The Helper must respond to an invitation from a user within a certain time limit (default is 6 seconds) or the invitation will expire and a new invitation will be needed. In a domain environment, this card's lifetime can also be configured with Group Policy, and we will show you how to manage Remote Assistance using Group Policy in the following articles.
- Solicited RA Using File Transfer (Solicited RA uses File Transfer ) This method requires both users and helpers to access a shared directory (such as a shared network on a file server) or they use a number of other methods to transfer file information (for example, by using a USB key to transfer files or upload files to an FTP site). Users create an RA invitation file and save it in a shared folder. The user must provide a password, which is used to communicate with the helper using the same calling method. The Helper gets the card and must respond to the invitation within a specific time or the invitation will expire and must wait for the following invitation. (Time limit is configured in Group Policy).
- Solicited RA Using Instant Messaging (Solicited RA with IM) This method requires IM applications that are being used by both users and helpers that support Microsoft's new Rendezvous API. Windows Live Messenger is an example of an IM application that supports Rendezvous (exchange). Windows Live Messenger is available online for download. In this method, the user requests assistance from someone on his buddy list. To make sure that the remote driver is actually a close friend of this user (not someone pretending to be a friend to trick you), Remote Assistance requires a password that is relayed from the user to the helper by Different ways (such as calling) before helpers can connect. To learn more about the Rendezvous API, you can see the Windows SDK on MSDN at http://windowssdk.msdn.microsoft.com/en-us/library/default.aspx.
2. Unsolicited RA . In Unsolicited RA (also known as Offer RA), helpers help users by initiating an RA session.
- Offer RA using DCOM (Create RA using DCOM) This is a typical Help Desk scenario in which all users are in a domain. Helper enters the full name of the user (FQDN) or the computer's IP address to connect to the user's computer. This method requires the Helper to be authenticated with domain administrator rights to be able to provide RA to the user. This method also requires the Helper to know the name (server name on the local subnet; full name) or address (IPv4 or IPv6) of the user's computer.
- Offer RA using Instant Messaging This method requires instant messaging (IM) applications used by both users and assistants that support Rendezvous API. In this method, the helper supports someone on his buddy list. If this person agrees, he must enter a password for the helper to use. The password must be transferred by another method to ensure that the remote person is actually a close friend of the user (to avoid being a fake person). For more details about the Rendezvous API, you can see the URL at http://windowssdk.msdn.microsoft.com/en-us/library/default.aspx.
How RA invitation files work
RA invitation files (.MsRcIncident) are XML-formatted files that contain information used by the Helper's computer, the computer will make a connection.This card information is encrypted to prevent unauthorized users from accessing, using email or transferring files used to send invitations on unsecured networks.
If the email method is used to send the invitation file to the helper, the invitation file is sent as an email attachment with a file name of RATicket.MsRcIncident.If the file transfer method is used, the invitation file will be created by default on the desktop of the user's computer and the file name of this invitation file is Invitation.MsRcIncident.
Operation status of RA
Remote Assistance has the following three operating states:
- Waiting For Connect (Waiting for connection) This status appears when:
- The Helper has provided RA to the user but the user has not yet agreed to allow the Helper to connect to his computer.
- The user has sent an invite to the Helper but the Helper has not responded by opening it or opening the invitation file and the user has not yet agreed to allow the Helper to connect to his computer.
In the state of waiting for the connection, the Helper cannot view or control the user's computer screen until an RA connection is established and both computers have entered the shared screen state. When the RA application is started and running in connection waiting state, the application will not be closed until another group responds and establishes a connection. For example, if the user uses the Solicit RA Using E-mail method and sends an invitation file to the Helper, the RA application opens on the user's computer and waits until the Helper accepts the invitation. If the user closes the RA on his computer before the Helper accepts the invitation, the Helper will not be able to connect to the user and the user needs to send a new invitation.
- Screen Sharing This status appears when the user has agreed to allow the helper to connect to his computer - after the user has sent to the helper an invitation or support file. Help has provided RA to users. In the shared screen state, the RA session is set and the Helper can view but cannot control the screen of the user's computer. When the user is prompted to allow the Helper to connect to his computer, a message will appear on the user's computer, indicating that the Helper wants to connect to the computer. he. This message can be customized using Group Policy.
- Control Sharing This status appears after the sharing screen state, when the Helper has requested control of the user's computer and the user has agreed to allow the Helper to control computer. In this mode, the Helper has the same access level for the computer the user has and the Helper can use his own mouse and keyboard to perform actions on the user's computer. Special:
- If the user is a standard user on the computer, the Helper can only perform actions on the user's computer as a standard user.
- If the user is a local administrator on the computer, the Helper can perform actions on the user's computer as an administrator.
For more detailed information about the level of control a Helper has on a user's computer, you can follow in the following articles.
Functions of users and helpers
Once the RA connection has been established and both computers have entered the shared screen state, users and helpers can perform the tasks listed in the table below:
Describe the Helper User tasks
Chat
Yes Yes
Send file
Yes Yes
Save the session action record
Yes (default) Yes (default)
Configure bandwidth usage
Yes No
Stop (temporarily hidden screen)
Yes No
Request shared control
No Yes
Give up control of sharing
Yes Yes
Cancel the connection
Yes Yes
Disconnect with Esc key
Yes No Table 1: Tasks can be performed by the user and the assistant during an RA session
Remote Assistance and NAT Traversal
Remote Assistance works by setting up peer connections between the user's computer and the helper's computer. One difficulty in this connection is that it is very difficult to establish peer connectivity if one or both of these computers are behind the gateway or router that uses Network Address Translation (NAT). NAT is a routing technology described by RFC 1631, used to translate IP addresses and TCP / UDP port numbers in forwarded packets. NAT is typically used to map a set of private IP addresses to a public IP address (or to multiple public addresses). Home networks that are using wired or wireless routers also use this NAT technology.
To overcome this difficulty, Vista was built with Teredo support, an IPv6 transition technique described in RFC 4380, which provides address assignment and automatic tunneling. for unicast IPv6 connection via IPv4 Internet. The NAT traversal capability provided by Teredo in Vista allows RA connectivity when one or both users in an RA session are hidden behind NAT. The perception of RA is transparent based on the user's perspective, regardless of which NAT is being used on the user's network. For most small businesses and home user environments, Vista's RA will seamlessly follow NAT-enabled routers without additional router configuration.
Note: Providing RA by using DCOM is not always a Teredo script because business users are always behind the company's firewall and cannot be distinguished by NATs. RA will not connect in certain configurations. Special:
- Teredo cannot follow a symmetric NAT. RA can only connect through restricted NATs and cone NATs. In some cases, this is not an important limitation because most of the deployed NATs are restricted or conical.
- RA will not work if the NAT-enabled router is configured to block certain ports used by RA.
- RA will not work if the user's NAT-enabled router is configured to block all UDP traffic.
Note : To determine the type of NAT that a network is using, open a command prompt and type netsh interface teredo show state.
Remote Assistance and IP ports are used
The ports used by the RA session depend on the session between Vista computers or between a Vista computer and an XP computer. Specifically:
- Vista with Vista : Dynamic ports are located by the system in the TCP / UDP range 49152–65535
- Vista with XP : 3389 TCP Port (local / remote)
In addition, the Offer RA script via DCOM uses port 135 (TCP).
Remote Assistance and Windows Firewall
Windows Firewall is configured with a group exception for RA. The exception of this group has many attributes that are included as part of the RA exception. RA exception attributes will vary depending on the computer's network location (private, public, or domain). For example, the default RA exception when the computer is in public places will be more accurate when the computer is in its own location. In public points (such as airports), the RA exception is disabled by default, does not open Universal Plug-and-Play ports (UpnP) and the Simple Service Discovery Protocol (SSDP) traffic. In a private network (home network, for example) the RA exception will be enabled by default and the uPnP and SSDP traffic will be allowed.
Table 2 summarizes the status of the RA firewall's access exceptions for each network location. However, the RA exception also has outbound properties, Windows Firewall is not configured by default to enable properties.
Network location
Status of RA exception
Default properties of the RA exception
Private network (family or workplace)
Activated by default
- Exception Msra.exe application
- uPnP is enabled for communication with uPnP NATs
- Edge traversal is activated to support Teredo
Public
Disabled by default - must be enabled by administrator privileges
- Exception Msra.exe application
- Edge traversal is activated to support Teredo
Domain
Disabled by default - enabled by Group Policy
- Exception Msra.exe application
- Exception RAServer.exe application (RA COM server)
- DCOM port 135
- uPnP is enabled for communication with uPnP NATs
Table 2: Default state of the Remote Assistance Firewall input exception for each network location type
In the Windows Firewall profile, the default configuration of the RA exception is as follows:
- Private profile Exception RA in Windows Firewall is enabled by default when the computer location is set to 'private.' It is configured with NAT traversal by using Teredo by default so that users in a private network environment (for example, a home environment) can get help from other users who may be on the same side. after NAT. Private files include appropriate exceptions needed for communication with uPnP NAT devices. If there is a uPnP NAT in this environment, the RA will use uPnP for NAT traversal. Offer RA via DCOM is not configured in this profile.
- Public profile Exception RA is disabled by default and does not allow RA traffic. Windows Firewall is configured in this way by default to better protect users in public network environments (such as cafes or airports). When the RA exception is enabled, NAT traversal using Teredo is enabled. However, traffic to uPnP devices is not enabled and Offer RA via DCOM is not enabled.
- Domain Profile . The RA exception when the computer is in a domain environment is relayed to the Offer RA script. This exception is disabled by default and enabled via Group Policy. Teredo is not enabled in this profile because the corporate network usually has a firewall to block Teredo UDP traffic. However, uPnP is enabled so that the NAT uPnP can communicate.
Remote Assistance and Secure Desktop
When the user agrees that the Helper can share control on his computer during an RA session, the user has the option to allow the Helper to respond to UAC prompts (Figure 1). . Typically, User Account Control (UAC) prompts appear on the Secure Desktop (the remote control component) and so the Helper cannot see or respond to Secure Desktop prompts. Secure Desktop mode is similar to the mode that users see when they log on to the computer or press the key combination (Ctrl + Alt + Delete). UAC prompts are displayed on the Secure Desktop instead of the user's normal desktop to protect them from malware threats. Users must follow UAC prompts to return to their regular desktop and continue working. This consent requires either clicking Continue (if the user is a local administrator on the computer) or by entering local administrative information (if he is a standard user).
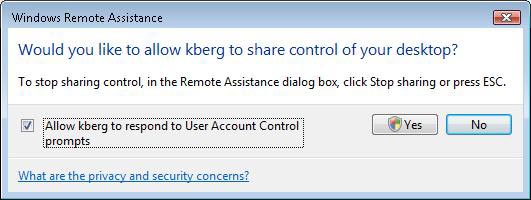
Figure 1: Users have the option to allow helpers to respond to reminders
UAC when the RA session is in the control sharing state.
It is also important to understand the Secure Desktop on a user's computer that is not remotely controlled. In other words, the helper can only respond to UAC reminders on the user's computer using the user's credentials. That means, if the user is a standard user on the computer while the helper is a local administrator on the user's computer, the helper can only have administrative rights on the user's computer. If the user gives him the necessary information.
The introduction of this limitation is necessary to ensure the security of Vista computers. The reason behind the decision to design this is that if the RA is designed to allow remote control helpers with user rights, the user may stop the RA session and so can take management information. local treatment from the helper.
Logging of RA
Remote Assistance can record sessions of RA-related actions. This session logging is enabled by default and includes time-stamped records to identify RA-related actions on each computer. Session logs include information about RA-related actions, such as who initiated the session, . These session logs do not have information about the current task that the user and the helper have actually done. show up during a session. For example, if the Helper receives sharing control, start an administrative command prompt and perform steps to reconfigure TCP / IP on the user's computer during an RA session, the logs session sẽ không có bản ghi của hành động này.
Các bản ghi session gồm có cả các hành động chat được trao đổi trong suốt một session RA. Bản ghi đã tạo ra trong suốt một session cũng được hiển thị bên trong cửa sổ chat để cả người dùng và người trợ giúp có thể nhìn thấy những gì đã được ghi trong suốt session. Các bản ghi này cũng gồm có hành động trao đổi file xảy ra trong suốt session, và cũng ghi lại khi session bị dừng.
Mục đích của việc ghi session RA
Các bản ghi session cho RA được dự định chính cho hoạt động kinh doanh yêu cầu duy trì các bản ghi hệ thống và hành động người dùng cho mục đích ghi chép. Chúng không được dự định để ghi các hành động được thực hiện bởi cá nhân trợ giúp khi các vấn đề khắc phục sự cố với máy tính của người dùng. Một môi trường điển hình trong việc ghi chép session là ở các ngân hàng, tại đây các tình huống tài chính bị yêu cầu bằng luật là phải giữ các bản ghi của những người đã truy cập vào máy tính và thời điểm nào.
Vì ACL tên các bản ghi session này cho phép toàn quyền điều khiển của người dùng trên các bản ghi đã được lưu trên máy tính của chính họ, mặc định các bản ghi session được tạo ra trên cả máy tính của người dùng và người trợ giúp để người trợ giúp có thể bảo vệ và thực hiện chúng khi bị xáo trộn.
Trong môi trường doanh nghiệp, Group Policy có thể được sử dụng để kích hoạt hoặc vô hiệu hóa việc ghi session. Nếu việc ghi chép này không được cấu hình bằng Group Policy, thì cả người dùng và người trợ giúp hoàn toàn vô hiệu hóa việc ghi chép session trên máy tính của chính họ.
Đường dẫn bản ghi session và việc đặt tên thông thường
Bản ghi session là các tài liệu XML để chúng có thể dễ dàng tích hợp vào các kiểu dữ liệu khác – ví dụ, bằng cách import chúng thành một cơ sở dữ liệu được quản lý bởi Microsoft SQL Server 2005. Tất cả các bản ghi session đều được lưu trong thư mục Documents của người dùng bên trong đường dẫn sau:
Users user_name DocumentsRemote Assistance Logs
File bản ghi session duy nhất này được tạo cho mỗi session RA trên máy tính. Các file bản ghi đã lưu bên trong thư mục này được định dạng XML và được đặt tên với đuôi thông thường YYYYMMDDHHMMSS.xml. Nội dung bên trong của một file bản ghi session điển hình được cho dưới đây:
fe80::2856:e5b0:fc18:143b%10
jdow
jdow: test
jchen: ok
 Windows Vista: Supporting users using Remote Assistance (Part 2)
Windows Vista: Supporting users using Remote Assistance (Part 2)
 Windows Vista: Supporting users using Remote Assistance (Part 3)
Windows Vista: Supporting users using Remote Assistance (Part 3)