- The client is 'bolted-in' inside the corporate network
- Roaming remote access VPN client
- DirectAccess client
The difference between DirectAccess and VPN
In this article we will discuss the difference between DirectAccess and VPN.
DirectAccess has a lot of features that make many users confused with VPNs, but the fact that DirectAccess is not the same as VPN. So how to distinguish the differences between them. In this article we will introduce you to this difference by placing them in scenes with different client types on the network, then observing important connectivity and security issues for each type. this client.
Client types
To begin this discussion, we acknowledge that there are three general types of clients that are:
The client is 'bolted-in' inside the corporate network
'Bolted-in' clients inside a corporate network are systems that may or may not be 'bolted in' properly but will never separate from the company's internal network (which can be interpreted as machines). Guests are tied to the corporate network. This system is a domain member, a managed system and never exposed to other networks. Internet access of this network is always controlled by the application layer inspection firewall, such as the TMG firewall. USB and other communication slots are physically blocked or managed strictly, access to the building where these computers reside is only allowed for trusted employees and passengers. These systems are installed with anti-malware software, configured via Group Policy or some other management system to maintain the desired security configuration, Network Access Protection (NAP) is enabled on the network to Prevent fake systems from connecting to the network and accessing company resources. Windows Firewall with Advanced Security is enabled and configured to reduce the risk of threats emerging from the network worm.
The concept of 'bolted-in' clients in the corporate network is nearly as ideal as the idea of secure clients:
- The system is never exposed to untrusted networks.
- Always managed.
- Always under the control of the IT group in the company.
- Access is restricted to trusted employees and guests.
- External access to the system will be limited by external ports that are managed or disabled physically.
- Internet firewalls that examine application layers such as TMG will prevent users from downloading exploits from the Internet.
- NAP reduces the risk of unmanaged clients connecting to the network and disseminating malware obtained from other networks.
- No system phenomenon will be stolen due to the use of physical ways to 'bolt in' clients with physical infrastructure.
You can imagine this is an ideal system in the form of network security, so how is this feature realistic? How many guest systems have you never left your corporate intranet? And even if there is proper control, how do they avoid attacks? We need to consider the following aspects:
- Social engineering is a common attack method, this attack method allows an attacker to increase physical access to certain computers that have been digested to install malware and Trojans on machines. 'bolted-in' calculation in the intranet.
- Even when physical ports are disabled, users can still get access to some optical drives - in case malware has been obtained from some external area, it can find a way to break in. on 'bolted-in' clients in the local network.
- Although the application layer inspection firewall can prevent malware and Trojans from entering the local network, but if the firewall does not perform SSL (HTTPS) checks, it will no longer be valid because Trojans can use it. Use secure SSL channels (not inspected) to reach their control workstations. In addition, users can take advantage of anonymous proxies over an unexpected SSL connection.
- If the Trojan has been installed on a 'bolted-in' client in the corporate network, a sophisticated Trojan will use HTTP or SSL to connect to its controllers and will almost connect to the site that is not listed. into 'dangerous' form. Even if an organization has used the whitelist method for security, an attacker can still take control (DNS poisoning) and instruct the Trojan to connect to that site so that it has Can receive control commands.
- Many users can bypass your control if they cannot access sites or access their desired Internet resources. If your users are using wireless connections, they can easily disconnect from the corporate wireless network and connect back to the network with another system to access locked resources according to the policy. company and then connect back to the company network after they have what they want. Users with wireless or wired connections can also plug in a wireless adapter to connect to an unfiltered network and compromise the computer through another port. In this scenario, the corporate 'bolted-in' client network accidentally received some roaming remote client features.
Implementing security thanks to diligence is an ineffective lesson. What is clear here is that, even in an ideal situation for 'bolted in' clients in the corporate network, there are still many things that may not be expected and lead to Serious accidents of security. You still need to do everything to make sure your computers are safe, keep them updated and manage them best - but need to put yourself in the perspective of computers. How to isolate and cannot move clients in the corporate network compared to other types of client systems.
Finally and perhaps most importantly, you need to know whether or not the 'bolted-in' client concept in a corporate network is probably just a concern. How many of these clients exist in corporate networks today - especially those in which the majority of employees are knowledgeable? In such an environment, you can assume that VDI is a feasible solution, because the tasks they perform do not require many functions provided by the full computer environment, but the employees knowledgeable need the flexibility and power provided by a complete computer platform. In addition, more and more companies realize the advantage of remote communication and more and more employees work from home or connect to the corporate network while on the road. These problems have arisen for us:
Roaming remote access VPN client
In the 1990s, it was common to use 'bolted-in' clients in the corporate network. However, by the second decade of the 21st century, employees need to work more and more on a mobile basis, which has resulted in roaming remote access VPN clients. Knowledgeable computer personnel can hold high-profile laptop computers to work, home, to customer locations, to hotels, seminars, airports, etc. is anywhere in the world where there is an Internet connection. In many cases, after accessing the Internet in many different locations, they brought their laptops back to the corporate network.
Roaming remote access VPN clients again pose a very different way of security than 'bolted-in' clients in the corporate network. A point like 'bolted-in' clients in the corporate network, these computers are domain members, installed with anti-malware software, activated Windows Firewall with Advanced Security and fully configured with consensus with company privacy policy. Initially roaming VPN computers provided to users are as secure as 'bolted-in' clients in the corporate network.
However, that security status and configuration did not last long. Users may not connect to the company intranet via VPN connection for days or weeks. Or they can connect daily for a week or two, then not connect for a few months. During the transition period, roaming VPN clients gradually lose their consent. Group Policy Group Policy is not updated, antivirus updates, and malware are not updated in time. Security policies and controls applied to clients located on the corporate intranet may not be feasible for roaming remote access VPN clients because they cannot connect via VPN with them. way.
The fact that roaming clients are not catching up with the company's configuration and security policies is becoming more and more serious because this computer is often connected to many untrusted and unsecured networks. all. These unreliable and insecure networks can have many network worms as well as other threats.
What happens when users bring their computers back to the corporate network? What happens if their computers are compromised by worms, viruses, Trojans or some other type of malware? The danger can be limited if you enable Network Access Protection on the network, but how many networks have enabled NAP, even though this feature has been available for years as part of Windows Server 2008?
Obviously users should not bring compromised computers back to the network. Suppose a certain user connected their computer to a number of different networks and eventually the computer was compromised. After three months he needs to change his password so he made a connection via VPN to change the password. In this case the disastrous security consequences will be similar to the case where this computer is physically connected to the corporate network.
As you can see, roaming has generated a lot of security issues compared to 'bolted in' clients in the corporate network:
- Roaming clients are often intermittently connected to the corporate network - or sometimes not connected - so will not keep up with security policies and other management systems.
- Be exposed to unmanaged or unmanaged networks, increase the potential 'attack surface' compared to clients that do not leave the intranet.
- Internet access is available and users can do whatever they want while connecting to the Internet because these clients are not checked and filtered for Internet connections.
- If the VPN client is configured to disable split tunneling, it may be required to use corporate Internet access ports while the client is connected. However, when the VPN connection is dropped, users can do what they want - can share any malware or trojan that the computer is infected while disconnecting from the VPN and connecting again.
- Users can avoid connecting to VPNs because of short logon times, inconsistent connectivity, and an overall less-than-optimal VPN experience, many risks in failing to keep up with company security policies and increasing risks. compromise.
- Group policy may or may not be updated promptly.
- Anti-virus software may or may not be updated promptly.
- Anti-malware software may or may not be updated promptly.
- Other management and control methods may or may not be reconfigured in a timely manner.
- The number of people with physical access to VPN computers is often greater than the number of people who can access 'bolted-in' computers in the corporate network, not just family members of users and friends. and those who steal computers.
The main difference between roaming VPN clients and 'bolted-in' clients in the corporate network is that VPN clients are often out of control and exposed to a large number of threats. However, there are many ways to mitigate some of these threats and many companies have introduced such implementation methods, such as:
- Use disk encryption (such as BitLocker) so that if a computer is lost, the thief will not be able to read the data in the drive. Disk encryption can also use the access method by 'locking' the disk so that when the computer is turned off users will not be able to boot when there is no key.
- Requires two-factor authentication to log on to the computer, along with requiring two coefficients to unlock the computer as well as wake them up.
- Use NAP or similar techniques to test security before the computer is allowed to access the corporate network. If the computer cannot fix it, it will not be allowed to access the corporate network.
- Do not use admin accounts to log on to the network, this is to prevent malicious attacks.
- Set the data center physically as well as logically with the entire client.
Using some of these measures will greatly reduce potential threats to remote access VPN clients. While it is not levelable compared to 'bolted-in' clients in the corporate network, there are some scenarios where roaming remote access VPN clients can reduce the risks. . We will look at one of the methods in this section.
DirectAccess client
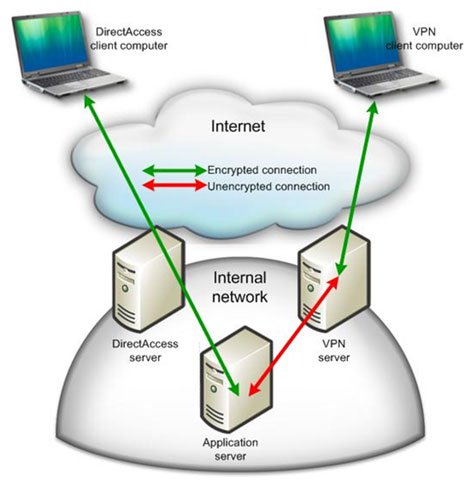
We are talking about the DirectAccess client theme. Like VPN clients, this computer can be moved from the corporate network, to a room in a hotel, conference center, airport, or anywhere a remote access VPN computer. via roaming can exist. The DirectAccess client will be connected to both a trusted and untrusted network, just like a remote access VPN client, and the risk of a computer's physical compromise is similar to that seen for the machine. VPN guests. So if you compare, the DirectAccess client and VPN are basically the same as before the security perspective.
However, there are still some significant differences between roaming and DirectAccess:
- The DirectAccess client is always managed. As long as it is enabled and connected to the Internet, the DirectAccess client will be connected to management servers to promptly update corporate security configurations.
- The DirectAccess client is always in the service state. If the IT group needs to connect to any DirectAccess client to perform some configuration software or troubleshoot the problem on this client, they will not experience any problems because of the connection between the DirectAccess client and the IT management station is always a two-way connection.
- The DirectAccess client uses two separate tunnels to connect. However, it only has access to the configuration and management infrastructure through the first tunnel. Network access is generally not available until the user logs in and creates an infrastructure tunnel.
When comparing the DirectAccess client to the remote access VPN client, you will see that the DirectAccess client appears less secure than VPN, this is because the DirectAccess client is always in the control of the group. IT company. Different from VPN clients, they may or may not connect to the corporate network for a long time, which can easily lead to failing to keep up with common security configurations and increasing the risk of security compromise. In addition, the above mentioned mitigation methods applied to remote access VPN clients can also be brought to use with the DirectAccess client.
So far we have achieved our goal of comparing roaming remote access VPN clients and DirectAccess clients, evidently all that is demonstrated in this article shows the DirectAccess client showing the safer in the general security of the company compared to roaming implementation.
You should read it
- Free Wi-Fi security tools
- Introduction to UAG DirectAccess - Part 3: NAT64 / DNS64
- Introduction to UAG DirectAccess - Part 1
- Introduction to UAG DirectAccess - Part 2: IPv6 transition technology and NRPT
- 10 things you need to know about DirectAccess
- Guidelines for securing computer network systems
- The basic steps in dealing with network security issues that you need to understand
- How to fix Appstore roaming error but cannot download
- Configure Forefront TMG as the DirectAccess server
- SECURITY SECURITY II: Security Policy Account for Computer Security Account Policies
- Security in difficult economic times
- Alarming statistics on the situation of network security in our country in the first half of 2019
Maybe you are interested
How to prevent harms when using a long-term laptop 8 user habits 'kill' the laptop faster What kind of intelligence do you own? Guidance on procedures for quick passport registration online What to do to ensure life in situations of bad guys attacking? New discovery: 5 types of personality that can 'extend life expectancy'
