Introduction to UAG DirectAccess - Part 2: IPv6 transition technology and NRPT
TipsMake.com - In this section we will show you some of the IPv6 transition techniques used by DirectAccess servers and clients to enable IPv6 data to be rotated across IPv4 networks.
We are currently using IPv4 networks and it is certain that these networks will remain in use for a long time. Although there are already some networks that have initially switched to IPv6, the deployment and upgrading of these protocols have been slow and sometimes not fully converted. In addition, very few computers can access IPv6 Internet, so it can be said that the transition to IPv6 will be very long.
Techniques to transition to IPv6
Because the DirectAccess client uses IPv6 to connect to the DirectAccess server and can go to a server within the corporate network, a method is needed to allow this IPv6 data to migrate across the IPv4 network. DirectAccess addresses this problem by using a number of different IPv6 transition techniques, helping IPv6 data to be encapsulated in IPv4 headers and thus being able to migrate in today's 'IPv4-only' networks. The techniques used here are:
- Intra-Site Automatic Tunnel Addressing Protocol (ISATAP)
ISATAP is used on local networks to communicate with each other by IPv6. The way to do this is to use an ISATAP tunnel adapter that has an IPv6 address assigned and then encapsulate the ISATAP communication data within the IPv4 header and send it in the intranet infrastructure. When these data reach its destination server, the IPv4 header will be removed and expose the IPv6 header and payload. ISATAP allows you to use all the advantages of IPv6 without requiring network upgrades and infrastructure. - 6to4 Protocol
6to4 protocol is used by DirectAccess client when this client is assigned public IP. Like ISATAP, a 6to4 tunnel adapter is automatically configured on the DirectAccess client with IPv6 address. The DirectAccess client's IPv6 data will be sent from this adapter and then packaged in an IPv4 header to move over the IPv4-only network to the DirectAccess server. The UAG DirectAccess Wizard automatically configures the UAG DirectAccess server as a 6to4 router for the organization so you don't need to know anything about 6to4. 6to4 requires that all devices be placed between the client and the DirectAccess server to allow the IPv4 protocol. - Teredo Protocol
The Teredo protocol is another IPv6 transition technique that the DirectAccess client uses to connect to the UAG DirectAccess server over an IPv4 Internet network. Teredo is used when the DirectAccess client is assigned a private IP address and has outbound access to UDP port 3544 on the UAG DirectAccess server. With Teredo, IPv6 data will be sent via the Teredo adapter (automatically configured on the DirectAccess client) and then packaged inside an IPv6 header, then further packaged in the UDP header. Two public IP addresses must be assigned to the external interface of the UAG DirectAccess server; They are used to determine the type of NAT device the DirectAccess client is behind. In addition, all devices need to allow pings so the Teredo client can connect to them. - IP-HTTPS Protocol
IP-HTTPS is a completely new protocol developed by Microsoft, which allows DirectAccess clients to connect to the UAG DirectAccess server only when the outbound TCP 443 port is allowed to communicate with the client. This method is used in case the firewall is set to a very limited level or when the organization that the DirectAccess client only allows outbound access through Web proxy device. With IP-HTTPS, the DirectAccess client will set up an IP-HTTPS tunnel adapter and send its data through it. This data is then encapsulated within the IPv4 header, then encapsulated in the HTTP header and encrypted using SSL (TLS). As you can imagine, the higher the overhead in each protocol, the greater the effect on performance.
Because of this, IP-HTTPS configuration should be avoided if possible. The DirectAccess client, when assigned a private IP (private IP) address, tries to use the Teredo protocol, which is a pretty good protocol. Only when Teredo cannot use it, the DirectAccess client will switch to using IP-HTTPS protocol.
At first glance, we can assume that IPv6 transition technologies are confusing and difficult to remember, but the UAG DirectAccess Wizard will do all the work for you. It will configure the UAG DirectAccess server as a 6to4 router, Teredo router and IP-HTTPS gateway without you knowing much about the protocols that make DirectAccess work. All of these techniques work at the bottom and allow for seamless connectivity to DirectAccess clients.
In organizations, the distribution of DirectAccess client connections is quite different. This distribution may vary depending on disabling split tunneling.
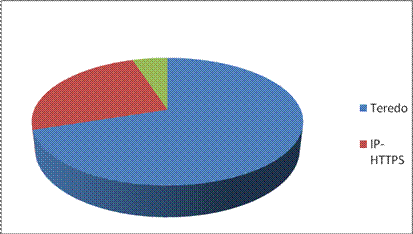
Figure 1
By default, the DirectAccess client uses split tunneling to allow users to access the Internet directly without forcing connections using the intranet gateway. We can use DirectAccess 'Force Tunneling', which can disable split tunneling for DirectAccess client connections and force them to use the Internet port on the corporate network to connect to the Internet. The downside of this Force Tunneling option is that the DirectAccess client must use IP-HTTPS, which results in poor performance. Force Tunneling and split tunneling will be discussed in more detail in the next section.
Name Resolution Policy Table (NRPT)
The Name Resolution Policy Table (NRPT) is used by the DirectAccess client to determine which DNS server to use, which is entirely dependent on the domain or FQDN of the destination it tries to connect to. With the help of the NRPT, the DirectAccess client sends DNS queries to the UAG DirectAccess server for name resolution when the domain is inside the intranet, and sends DNS queries to the domain outside the nest. function to the DNS server address configured on the DirectAccess client's NIC.
For example, suppose your organization has multiple subdomains within the contoso.com root domain. These domains may be in the same forest or different forests; In terms of domain name resolution, this has no problem. When configuring the NRPT, you set it up with an entry stating that all domain requests with the form * .contoso.com will be sent to the IP address of the UAG DirectAccess server. The reason the domain resolution requests are sent to the IP address of the UAG DirectAccess server is that the UAG takes the address of the intranet DNS server by installing its own DNS proxy. The DNS proxy on the UAG server will use the DNS servers configured on the external interface to resolve the domain name requested by the DirectAccess client.
So what happens to domains that are not in the NRPT? In this case, the DirectAccess client sends domain name query requests to the DNS server address configured on its NIC. When the DirectAccess client connects to the network, regardless of whether it is behind a NAT device or assigned a public IP, it receives from a DHCP server address. This is the address that the DirectAccess client will use to identify all domains that are not in the organization.
Conditional DNS routing or DNS forwarding leads to the default DirectAccess client configuration that enables split tunneling. The reason we choose split tunneling as the default configuration is because it significantly improves the performance for DirectAccess clients and hosts in the local network when they need to connect to Internet resources. If split tunneling is disabled ('Force Tunneling' in DirectAccess parlance) then all traffic will be routed through IPsec tunnels; including traffic for both intranet and Internet traffic.
Some people may be concerned about split tunneling because someone thinks that split tunneling is not good. This view may be true for VPN clients in the 1990s, and recent Windows operating systems do not allow attackers to route through VPN clients to connect to the corporate network. The situation is even more secure with DirectAccess, because if an attacker finds a way to route connections from the Internet through the DirectAccess client, the connections will fail because IPsec requires security in The tunnel must be based on the DirectAccess client's IP address, in addition to a computer certificate, computer account, user account, etc. smart card is also required to establish a connection. Security issues that exist with split tunneling do not apply to DirectAccess clients, so there is no reason to worry about this issue in the DirectAccess scenario.
NRPT is also used to prevent the DirectAccess client from resolving certain domain names to query DNS for domains that are never sent to the intranet DNS server (a UAG DirectAccess instance is DNS proxy on UAG DirectAccess server. An important example in this situation is the Domain Location Server (NLS) domain. The DirectAccess client uses NLS to determine if it is on the corporate network. If the DirectAccess client can connect to NLS, it knows it is in the corporate network and turns off the NRPT. If not, the NRPT is enabled.
If the NRPT has been configured so that the DirectAccess client can resolve the domain name of the NLS, the DirectAccess client on the Internet will think it is on the corporate network and will turn off the NRPT. If the DirectAccess client is on the Internet and has turned off the NRPT, it will not send DNS queries for the domain of the corporate network to the UAG DirectAccess server's DNS proxy and therefore will not be able to resolve the domain names of the network. internal. To solve this problem, the NRPT needs to be configured with an exception rule to avoid the DirectAccess client on the Internet resolving the NLS domain.
For example, if the NRPT is configured to send all queries matching the * .contoso.com string to the DNS proxy on the UAG DirectAccess server, it will have the domain name query nls.contoso.com, this is NLS domain name on the corporate network. However, if we create an exception to the domain nls.contoso.com in the NRPT, although this domain is still within the * .contoso.com range, the query will not be sent to the DNS proxy on the UAG server. DirectAccess will instead be sent to the DNS server configured on the UAG DirectAccess client's NIC. Since this domain cannot be resolved, the DirectAccess client on the Internet will assume that it is outside the corporate network and will activate the NRPT.
Conclude
In this section, we have introduced the IPv6 protocol conversion techniques used by the DirectAccess client and server to allow IPv6 data to be transmitted over the Internet or intranet. We will introduce the functions and values of the Name Resolution Policy Table, used by DirectAccess to identify the DNS server that will send a specific domain query request. In the third part of this series, we will talk about the NAT64 / DNS64 features that are included in the UAG DirectAccess server.