How to Tell if You're Having Unauthorized Access
Recognize signs of suspicious unauthorized access
See if anything unusual is happening on the computer. You know the computer and how it works better than anyone else. If it used to run fine but then suddenly starts behaving strangely, it could be a sign of age or a malfunction. However, the following issues can also be signs of unauthorized access:
Some common programs and files do not open or work.
Files that you never deleted appear to have disappeared, been placed in the trash, or been deleted.
You cannot enter programs with commonly used passwords. You notice that the password on your computer has been changed.
One or more programs appear on your computer that you did not install.
Your computer often goes online when you're not using it.
File contents are changed and you are not the one who made those changes.
The printer may behave strangely. Maybe it won't print no matter what you do, or it will print pages that aren't in your print job.

Go online. Here, you can also find signs of suspected unauthorized access:
One or more sites deny you access because of an incorrect password. Try visiting multiple sites you usually visit: if password access continues to be denied, it's probably because you've been accessed without permission. Is it possible that you have responded to a phishing email (fake email asking you to change your password update/security details)?
Internet searches are redirected.
Additional browser screens may appear. They can turn on and off while you're doing nothing. They may be darker or the same color but either way, you will see them.
If you buy a domain name, you may not be able to get it even if you pay for it.
Look for other common malware, overwrites, etc. unauthorized access. Below are some other symptoms that may appear when there is unauthorized access:
Fake virus messages. Regardless of whether your device has virus detection software: If it doesn't, these messages will automatically alert you; If so, and assuming you know what your program's message looks like, also be wary of fake messages. Don't click on them: they're a scam, they're trying to get you to reveal your credit card information in a panic, trying to remove a virus from your computer. Be aware that the hacker now has control of your computer (see What to do below).
Additional toolbars appear on your browser. They may carry a "help" message. However, there should only be one toolbar and it would be suspicious if the browser has more than one.
Random and frequent windows appear on your computer. You will need to remove the program that is causing this.
Anti-virus and anti-malware software is not working and does not appear to be connected. Your Task Manager or Registry Editor may also not work.
People in your contacts receive fake emails from you.
Money in your bank account is lost or you receive a bill for online transactions you didn't make.
If you simply have no control over any activity, prioritize the possibility that you are the victim of unauthorized access. Specifically, if the mouse pointer is running around on the screen and performing actions that produce real results, someone on the other end is probably controlling it. If you've ever had to get remote support to fix a problem on your computer, you know what it's like when done with good intentions. If this control is done without your consent, then you are being hacked.
Check your personal information. Google yourself. Does Google return personal information that you did not disclose yourself? It is unlikely that they will appear immediately, but being alert to this risk can be important in the event that personal information is disclosed.
Things need to do
Disconnect from the network immediately . The best thing to do while continuing your investigation is to disconnect from the network and disable online connectivity. If the hacker is still on the computer, by doing so, you have eliminated the source of the connection.
Unplug the router from the outlet to be absolutely sure there are no longer any connections!
Print this page on paper or PDF before turning off the power so you can continue following these instructions offline. Or, read it on another unauthorized device.
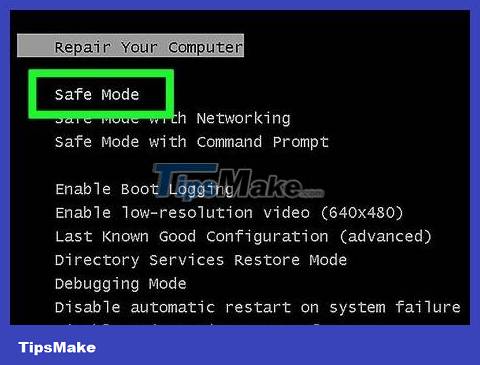
Start the computer in safe mode. Stay completely disconnected and use your computer's safe mode to turn it back on (check your computer's manual if you're not sure what to do).
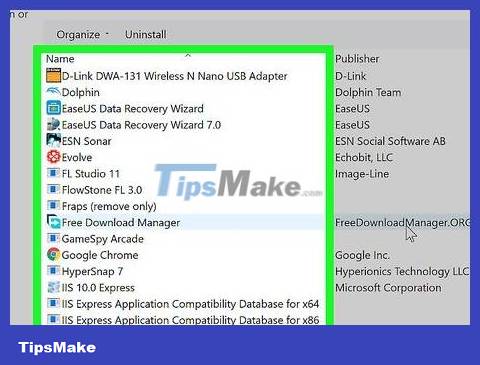
Looks up whether there are any "new programs" (such as anti-virus, anti-spyware, etc.) OR whether programs and files are inactive or not opening. If you find any, do your best to remove it. If you don't know what to do, ask for help from someone who knows computers or call a computer repair service to come and do it for you.
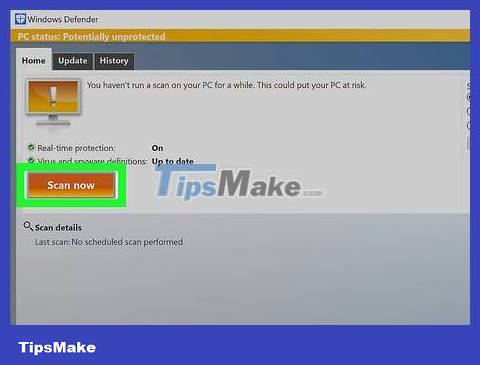
Scan your computer with virus/spyware scanning software you trust (such as Avast Home Edition, AVG Free edition, Avira AntiVirus, etc. ). Again, ask someone knowledgeable for help if you're not sure what to do.
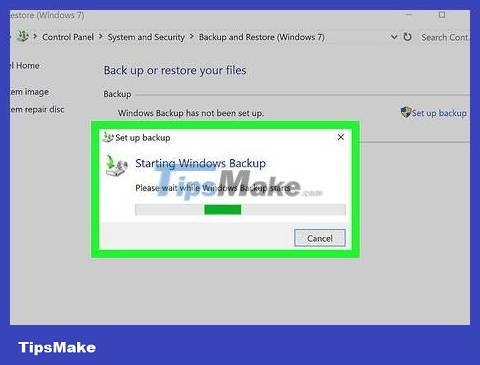
If you can't find anything, back up important files. Next, restore the entire system and update the computer.
Contact your bank and any purchase accounts you have to alert them to a suspicious problem. Ask for their advice on what to do next to protect your finances.
Warn your friends that they may receive potentially dangerous emails from you. Tell them to delete the email and not to follow any links if they accidentally open them.