How to Unauthorized Access (Hack) a website
Use XSS
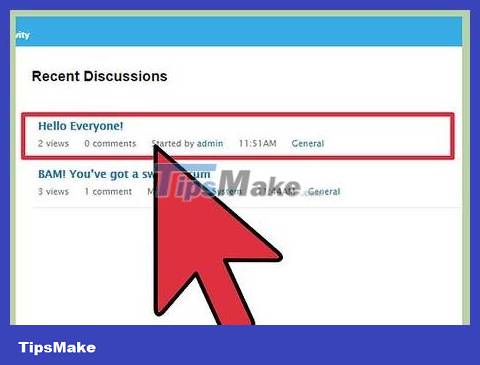
Find a vulnerable site that allows you to post content, such as a forum. Note that this method does not work on secure sites.
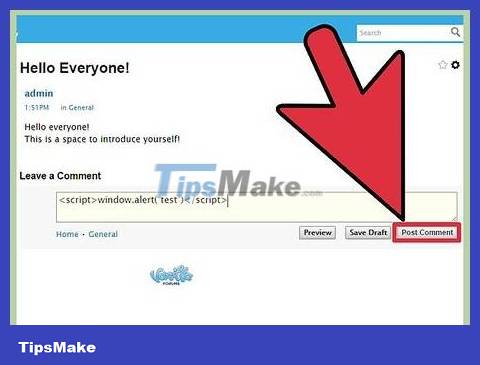
Go in and post content. You will have to enter some special code in the 'post' section to collect all the data of people who click on it.
You should check to see if this code is filtered by the system or not. Please post
If a warning box appears when you click on a post, the website is not safe.

Create and load your cookie interceptor. The purpose of this attack is to capture users' cookies, thereby accessing accounts on websites with insecure login processes. At this point, you need a cookie interception program to capture and redirect the target audience's cookies. Please upload this program to the php support website that you can access and see more about the code of the interceptor programs.

Post your cookie interceptor. Entering the appropriate code into the post is used to capture cookies and send them back to your site. You should enter some text after the code to make the post less suspicious and prevent it from being deleted.
For example, you can use
Use of cookies collected. At this point, you can freely use the cookie information saved on your website.
Attack by inserting malicious code
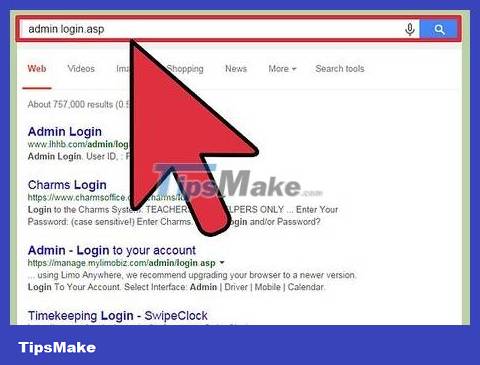
Find vulnerable sites. You should look for sites that have vulnerabilities in the administrative login process. Try searching for the keyword admin login.asp on Google.
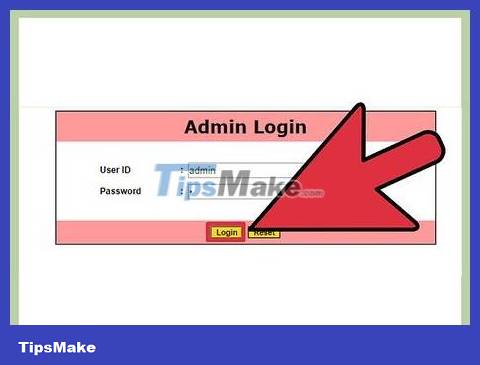
Log in with administrator rights. Use admin for the login name and try a few different character strings for the password. It can be any string, commonly 1', '1'='1 or 2'='2.

Please be patient. Most likely you will have to try multiple times.
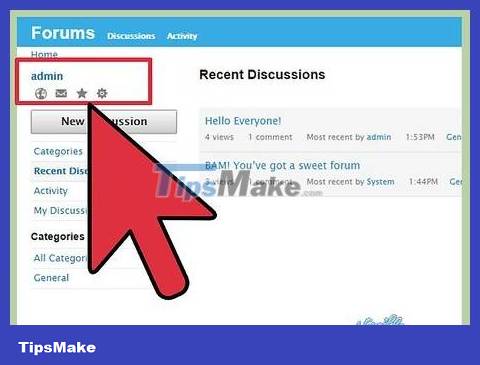
Access website. For sites that are easy to attack, you will also find a string of characters that allows you access with administrative rights.
Create the foundation for success
Learn a few programming languages. To truly hack, you need to understand how computers and other technologies work. Learning to use programming languages like Python or SQL will help you gain better control over your computer and identify security weaknesses in systems.
Equipped with basic HTML knowledge. You also need a deep understanding of html and javascript, especially in case you want to hack websites. Although learning takes time, there are countless ways you can learn for free on the internet. As long as you want, the opportunity is still yours.
Consult 'whitehat' - computer security experts. They are hackers who use their abilities for good purposes, exploiting security holes and improving the internet environment for everyone. If you want to learn hacking and use your abilities properly or simply to protect your website, you should contact and ask for advice from these experts.
Learn about hacking. If you want to learn how to hack or protect yourself, you will have to do quite a bit of research. Websites can be attacked in countless different ways, and the list changes every day. Therefore, you will have to constantly learn.
Update. Because hacking techniques are constantly changing, you need to constantly update them. Just because you're protected from certain types of hacks now doesn't mean you'll still be safe in the future!