Veil: anonymous browser deletes all traces, safer than Tor
Those who want to delete their browsing history without leaving any trace, which most anonymous browsers are currently unable to do, Veil will be the perfect choice for that.
Researchers at CSAIL Laboratories at MIT and Harvard University have introduced Veil, a different method of hiding themselves. It not only hides the browsing history, but also protects the operating system from the curious.

The need for anonymity in the Internet environment is increasing.
When accessing a website in incognito mode, the browser still collects information and downloads them into memory, displaying and storing them at libraries or plugins that can be accessed or modified. After that, the browser tries to delete these traces again, but whether or not it is successful depends on how it is set up. If unsuccessful, a full backup of your activity may be hidden in RAM or anywhere else.
Researchers from MIT said that even if you use 'famous' software like Tor, it is impossible to completely erase those traces.
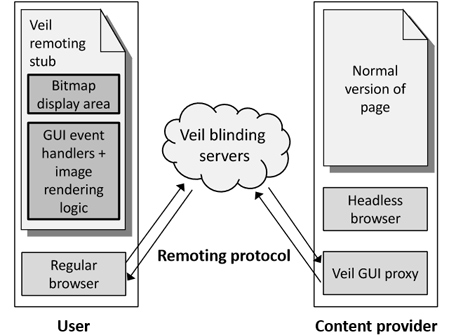
Veil uses its own server as an encrypted content transfer hub.
With Veil, it offers a new way of transferring web pages through a blind server called 'blinding server'. The user enters the URL, the page is retrieved from the encrypted special server to return the content to be viewed. Links and URLs are also encrypted, so there is no browsing history.
Even content changes. The code, the size that the computer measures, varies a thousand times even though the content displayed to the user is the same.
In addition, Veil has a very different mapping data browsing option. Veil can only capture the screen instead of displaying the actual code of the destination web. When the user clicks on the image, the system will record the click position to transfer the interaction to the actual page and return the corresponding results.
This week, Veil will be introduced at the System Dispersion and Security Symposium in San Diego, USA.
See more:
- Chrome's incognito mode is not as discreet as you think
- How to view and delete activity history on Windows 10
- How to automatically clear your browsing history when you exit Firefox
- How to automatically clear your browsing history when exiting the Edge browser Windows 10
- How to delete browsing history on Chrome 59 and Firefox
- How to delete Web browser history on iPad?
You should read it
- ★ Anonymous browsing: can protect your privacy
- ★ Guide to anonymous web on Android phones
- ★ Instructions on how to browse the web anonymously to keep your personal information private
- ★ Anonymous browsing has more uses than you think
- ★ How to browse common mode and anonymously with a window on Firefox