Security features of OWA (P.3)
In the next part of this article series, I will show you the security features available in Outlook Web Access in Exchange 2007, specifically about OWA authentication and OWA segmentation.
>> Security features of OWA (Part 1)
>> Security features of OWA (Part 2)
In the previous two articles of this series, we introduced the authentication methods included in OWA 2007. The third part of this series will begin by completing the authentication topic through the introduction of the The main point about which assessment method should be used. When this is done, we will introduce you to a new issue, which is the OWA segmentation feature.
OWA Authentication (OWA Authentication) - Which method?
The question is whether to use form validation or standard authentication for your infrastructure and requirements. For example, ISA Server 2006 is equipped with form authentication and can be enabled if needed. If your internal Exchange 2007 organization is protected by ISA Server 2006, you can implement Integrated Windows authentication on the Client Access Server instead of form-based authentication to avoid user will see two forms, one for ISA Server and one for Client Access Server. When the form authentication mechanism is configured on ISA Server and Integrated Windows authentication is configured on the Client Access Server, the user will only see the form once. When users enter their account information into the form and are authenticated by ISA Server, the connection to the Client Access Server, and OWA, is set automatically through Integrated Windows authentication.
The topic of user experiences also needs to be noticed here. For example, users who are connecting outside to OWA will see the formality screen of ISA Server, and if they are connected internally, they will be logged in automatically through Integrated Windows authentication. Some organizations have opted for additional implementations of internal Client Access Servers, or even added ISA Servers and configuration auditing to form them to ensure a consistent experience when users connect. connect to OWA inside or out.
In addition, consider the requirements in other important Client Access Server techniques, such as CAS-to-CAS credentials. Take a scenario where, for example, a certain user connects via OWA to a Client Access Server located in another Active Directory site with the Active Directory site with the mailbox server hosting the user's mailbox. In this case, the Client Access Server that the user connects to can locate the Client Access Server located in the same Active Directory site with the user's mailbox server and can proxy the user to Client Access. That server. This credential request is known as CAS-to-CAS credentials. However, in order for this process to work, the Client Access Server in the same Active Directory site with the user's mailbox must be set to Integrated Windows authentication on the virtual directory being accessed.
When considering the choice between two different standard authentication methods, one of the main concerns is that important data can cause security risks for the organization if OWA is used from public place or not. This is a concern if the user does not close the browser after accessing OWA; If the browser is not completely closed, there is a risk that other users can access the OWA session because the login credentials are still stored inside the browser.
It takes time to study the authentication requirements before selecting the most appropriate one, especially when using security products such as ISA Server 2006.
OWA Segmentation
OWA segmentation is another feature available in some earlier versions of Exchange, not a new feature in Exchange 2007. In essence, OWA segmentation is a feature that allows you to block access by Some users have some specific features of OWA. For example, suppose you are making a transition from your Exchange 2003 environment to Exchange 2007 and deciding to transfer your public folder information to Microsoft SharePoint. If you have deployed an Outlook 2007 client, it is not necessary to use public folders inside the environment and so you can lock access to this folder from within OWA. Figures 9 and 10 show you the difference between an OWA client when public folders are activated and an OWA client with a public folder has been disabled through OWA Segmentation. As you can see in Figure 10, the Public Folder button is completely lost.
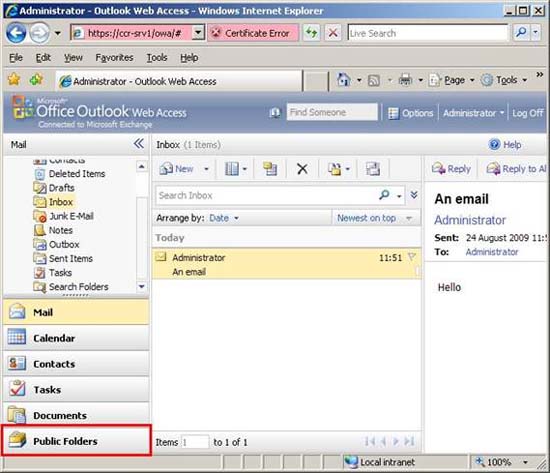
Figure 9: Public Folders available in OWA
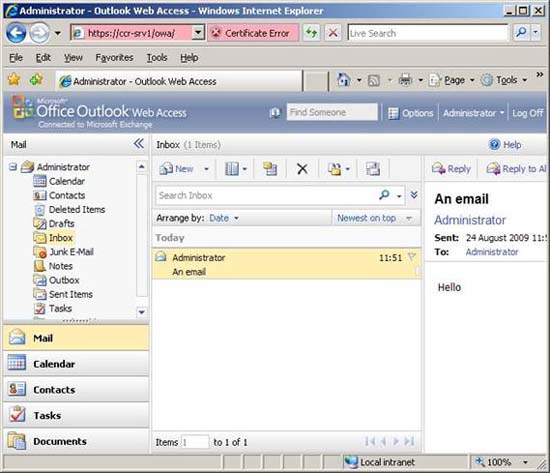
Figure 10: Public Folders disabled in OWA through OWA Segmentation
Or, perhaps you have not deployed Exchange ActiveSync devices or Unified Messaging server roles within your organization. Disabling these features is important, so the options do not appear in Outlook Web Access. Any configuration item that simplifies the user experience and can reduce calls that require assistance from the IT management team is a good thing.
It is possible to configure OWA segmentation for a range of features. This list includes, ActiveSync integration, address lists, calendar, contacts, journal, junk email, reminders and notifications notifications, premium client, search folders, signature email, spelling checker, tasks, theme selection, unified messaging integration, change password , rules, public folders, S / MIME and deleted item recovery.
You can control OWA segmentation for an entire virtual directory on the basis of Client Access Server or on the user. Let's first look at the control for the entire virtual directory, starting with the Exchange Management Console. To access the section that allows you to control Segmentation, call the properties of the / owa virtual directory and click the Segmentation tab. Figure 11 shows the contents of this tab.
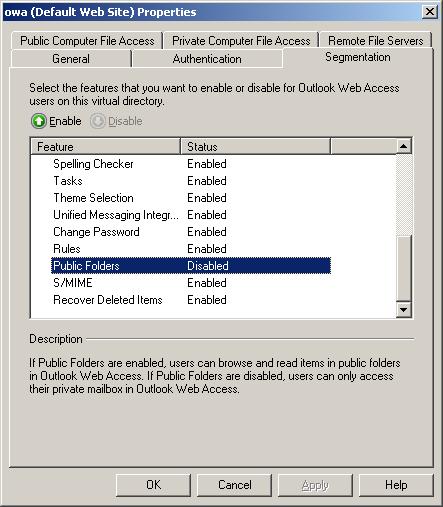
Figure 11: Tab Segmentation
As you can see in Figure 11, it's easy to understand how to enable or disable a feature here; You just have to choose which feature and click the enable or disable button.
Note : You can only configure Segmentation on the / owa virtual directory.
To use the Exchange Management Shell for configuring Segmentation, you can use the Set-OwaVirtualDirectory command. For example, if you want to invoke the / owa virtual directory property page on the CCR-SRV1 server, simply enter the following command:
Get-OwaVirtualDirectory 'CCR-SRV1owa (Default Web Site)'
This command will return for many parameters. Figure 12 shows some output parameters of this command, where you can see the status of each segment value.
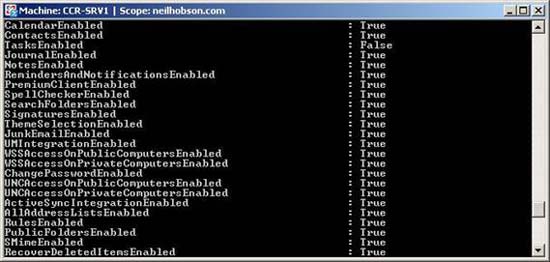
Figure 12: Output of the Get-OwaVirtualDirectory command
As mentioned earlier, it is possible to configure OWA Segmentation according to the user base. To do that, use the Set-CASMailbox command. For example, let's assume that we want to disable the Tasks feature for a certain user whose mailbox alias is neil . Then we can use the following command to achieve our goal:
Set-CASMailbox –Identity neil –OWATasksEnabled: $ false
You can then use the Get-CASMailbox command to verify that the setting has been made. Also note that user settings override any settings created on the virtual directory.
Conclude
In the third part of this series, I have shown you some important areas to consider when choosing the authentication methods, followed by the OWA feature segmentation. OWA segmentation is often overlooked when configuring Exchange 2007 but it is worth remembering that configuration helps users get a consistent feel when using Outlook compared to OWA.